Hi all,
I'm struggling with setting up Sophos VPN Client on user's Windows computers.
What behaviour I expect is to automatically connect when user connects any network except internal LAN/WIFI.
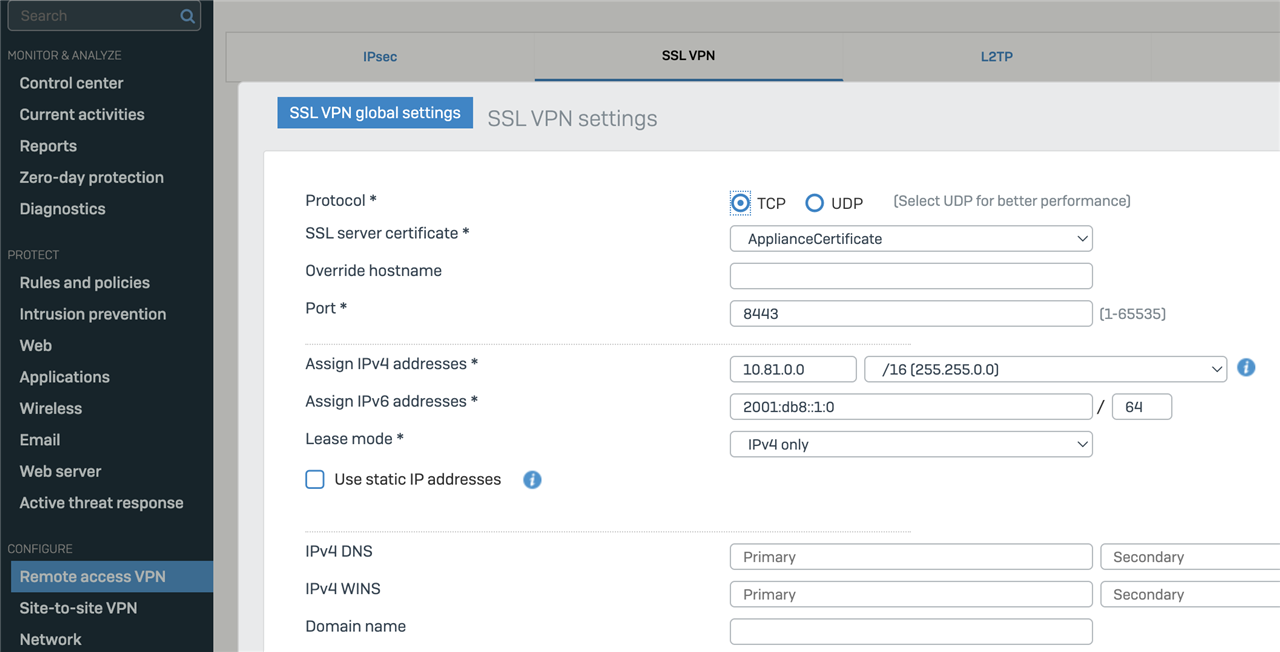
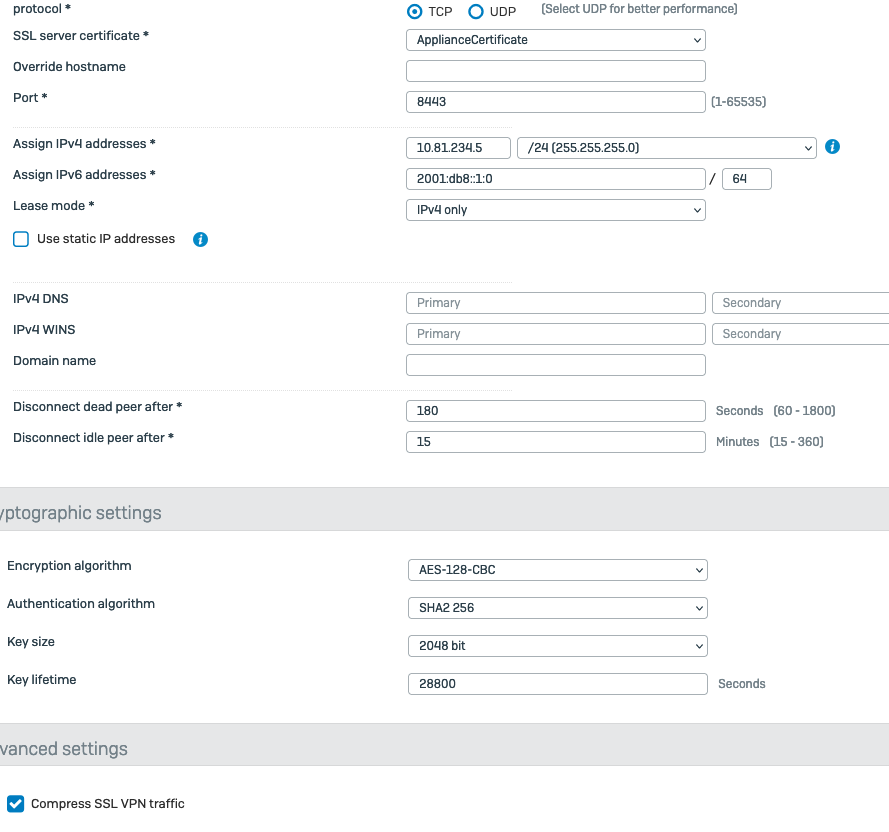
So if users is turning on the laptop at home and connects to his/her home WIFI, Sophos Client shoud connect VPN immediately. But when user comes to the office and connects to LAN network, Sophos Client should stop connecting. I edited ovpn config file and added auto_connect parameter as LAN VLAN network address (192.168.3.1), but it didn't help - after connecting to office's wifi, Sophos Client is connecting to VPN.
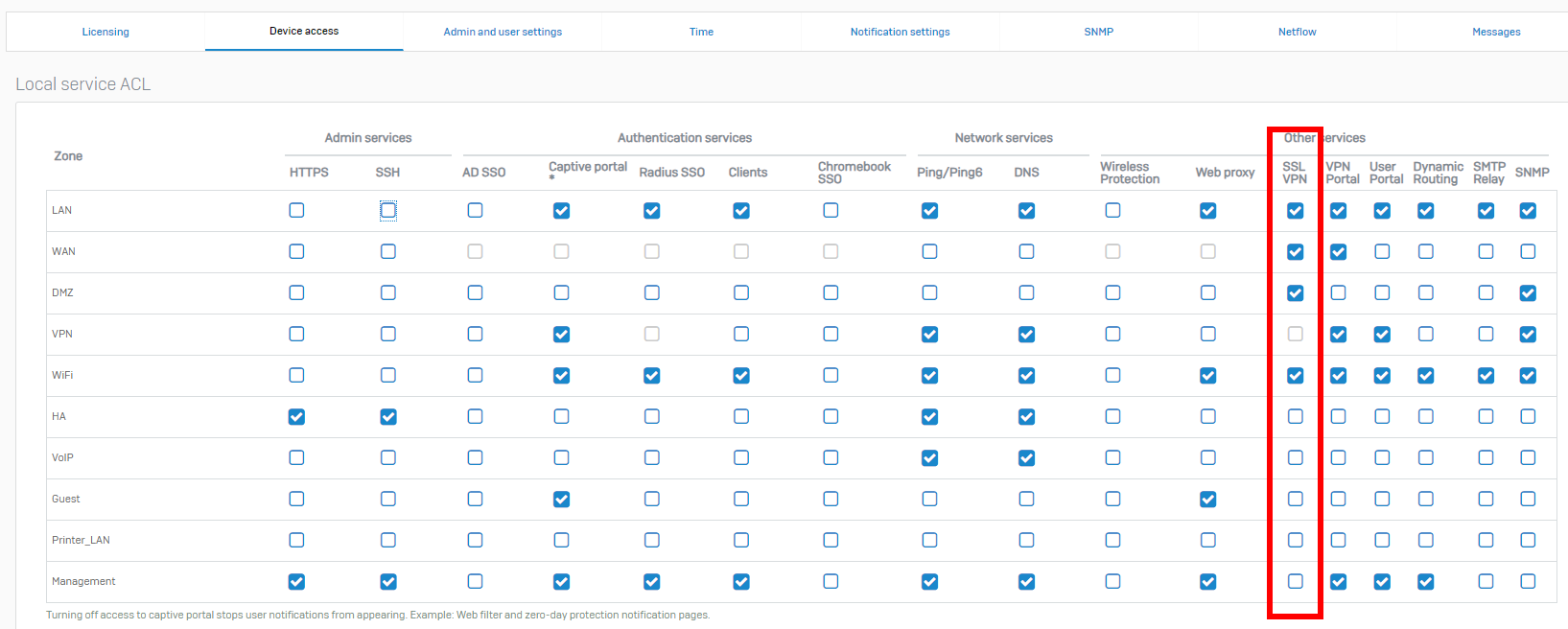
Next thing I tried was to block SSL VPN in firewall administration and it helped, but now Sophos Client is continuously trying to connect, fails, tries again, fails, and so on.
How to set it up so it just stops trying to connect when in LAN, and after network change (going back to home), connects VPN immediately?
This thread was automatically locked due to age.