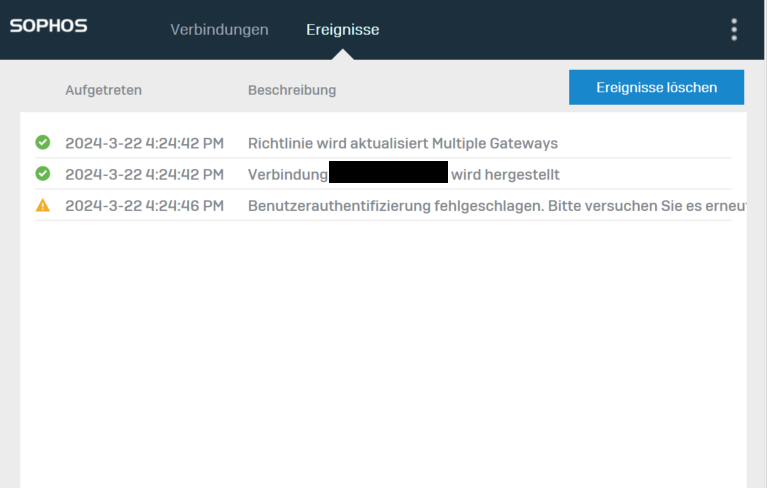
Is there any way to activate the MFA box at login in Sophos Connect direct in a .ovpn config (no provisioning)?
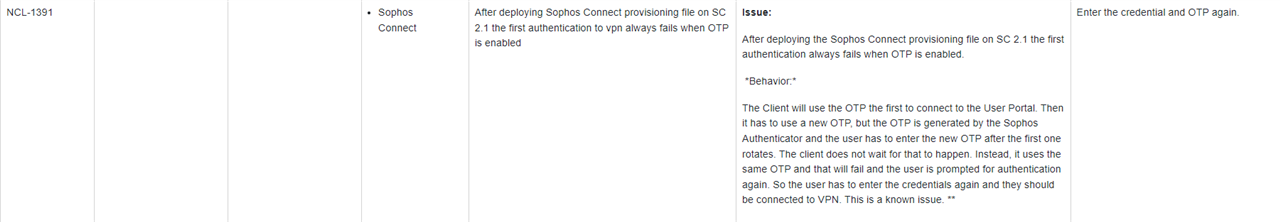
I guess with provisioning the firewall will also only create a .ovpn config with a parameter for MFA.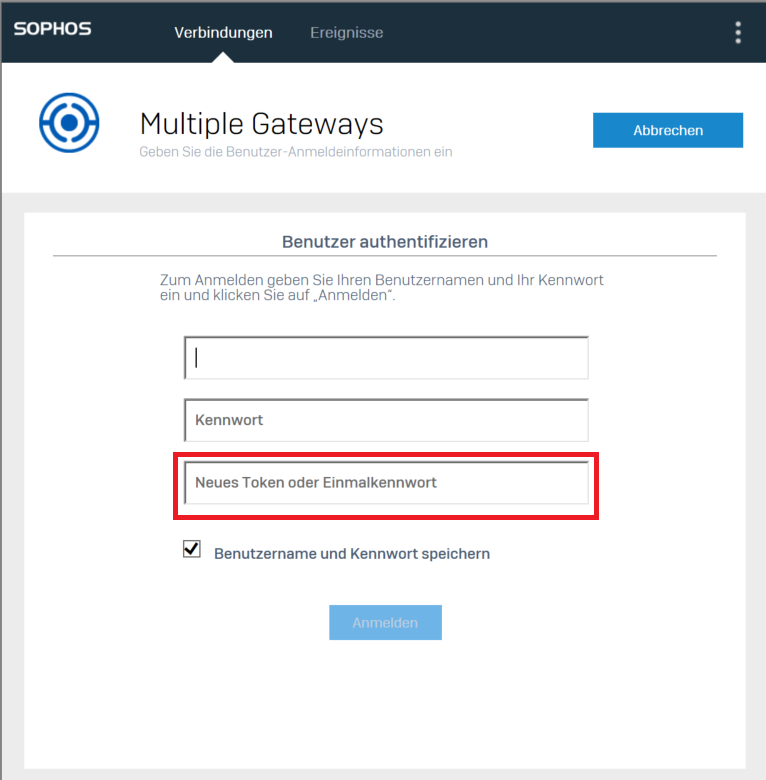
client
dev tun
proto udp
verify-x509-name "C=NA, ST=NA, L=NA, O=NA, OU=NA, CN=Appliance_Certificate_R3i4MjKOeECloSs, emailAddress=na@example.com"
route remote_host 255.255.255.255 net_gateway
resolv-retry infinite
nobind
persist-key
persist-tun
<ca>
....
</key>
auth-user-pass
cipher AES-128-GCM
auth SHA256
comp-lzo no
;can_save no
;otp no ???
;run_logon_script no
;auto_connect
route-delay 4
verb 3
reneg-sec 0
remote xxxxxxxxxx 443
explicit-exit-notify
This thread was automatically locked due to age.