Hello,
I am getting some unexpected and unwanted requests (trying to find exploits) that are handled by one of the WAF Rules:
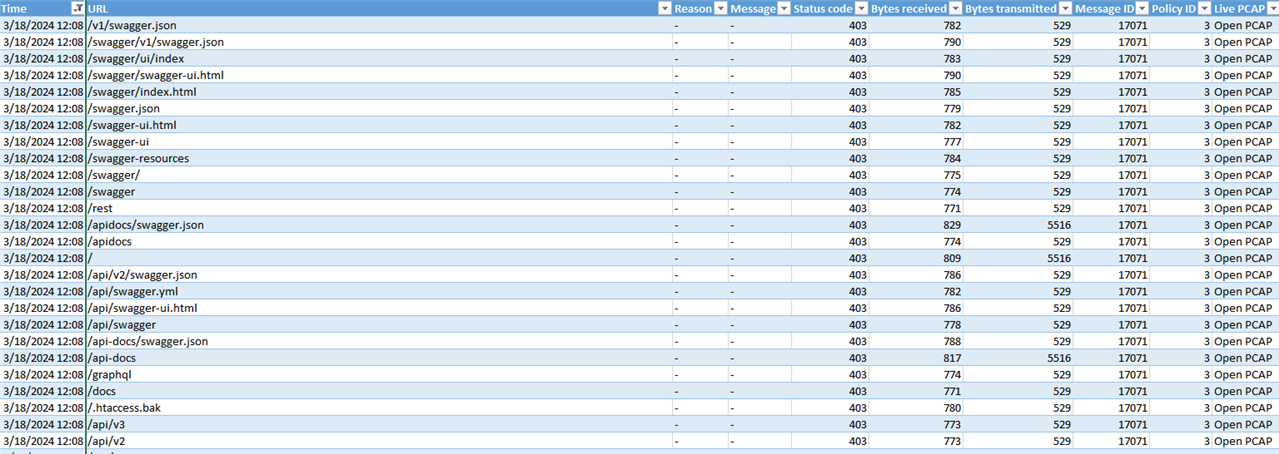
Here's the WAF Rule that is being it with this traffic: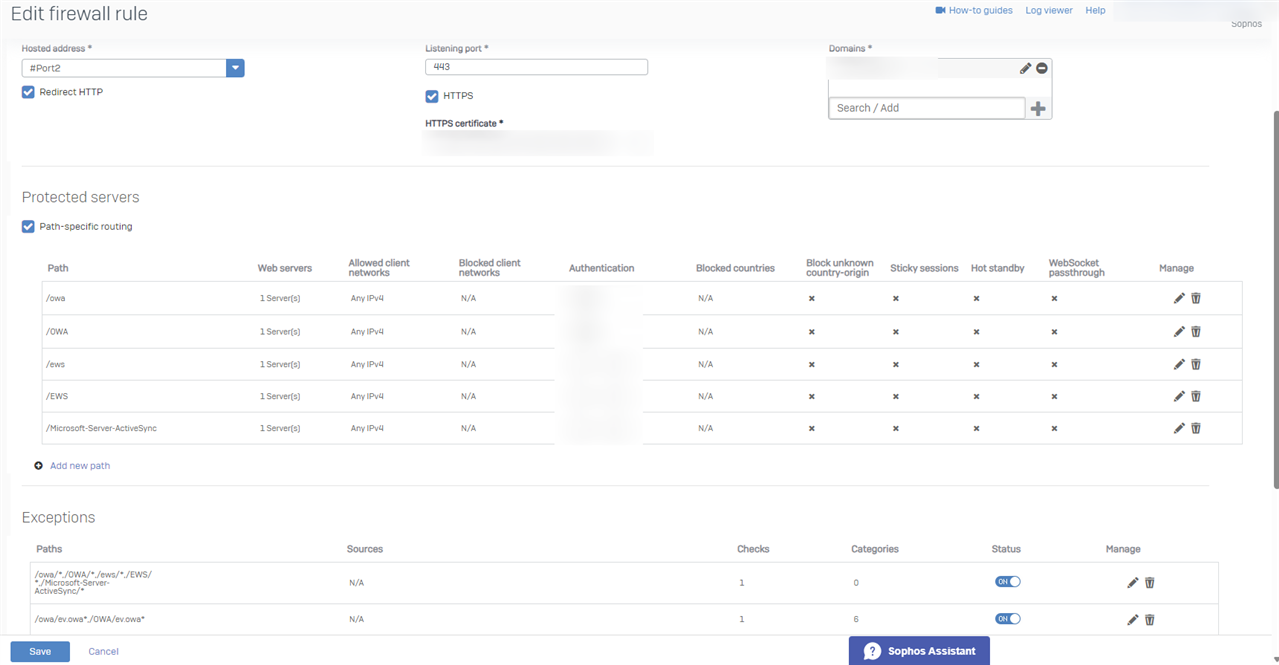
Here's how it looks in the Event Viewer: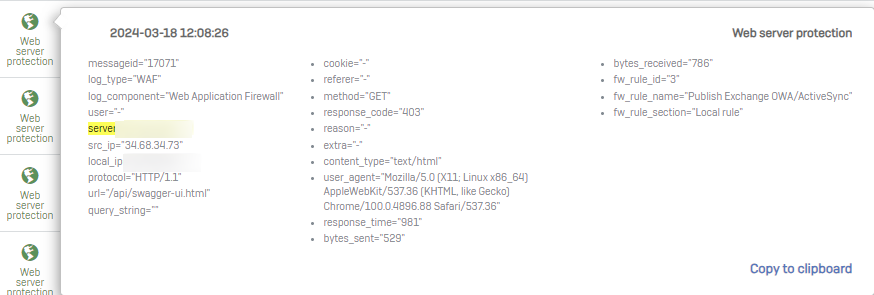
How can I change the WAF rule (or through another rule) so if the traffic doesn't match the published paths (below), it gets dropped (instead of returning an HTTP 403)?
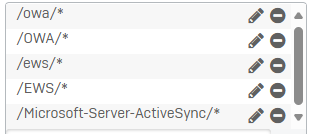
Thanks!
This thread was automatically locked due to age.

