Last year or so ago we had a case regarding this issue. Once again a vendor conducted a friendly PCI scan on our public interfaces and send us a notice of Non-compliance.
The robot scanner is seeing the self-signed appliance certificate on PORT 3400 - RED.
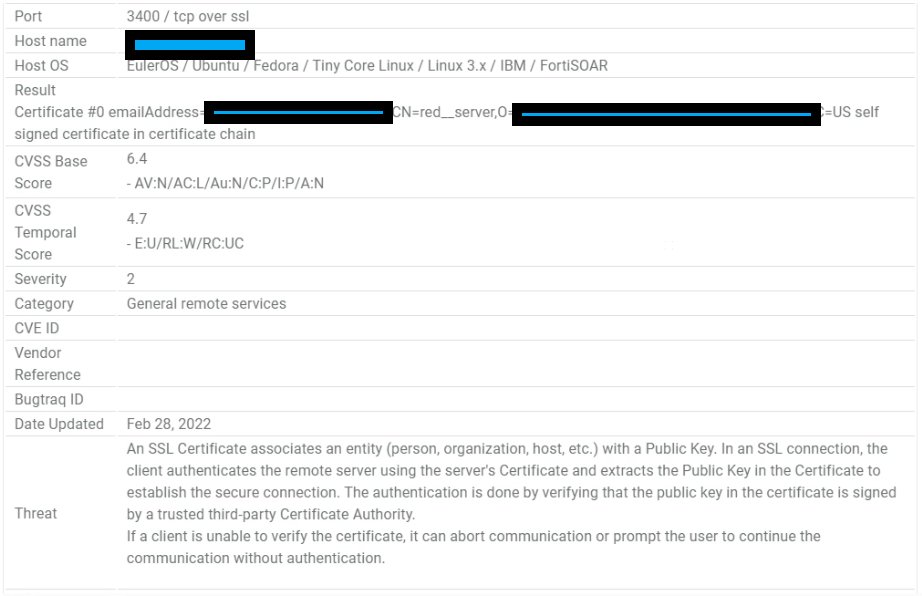
From our discussion with Sophos we believe this is a false positive. However notices like this are annoying as we must respond.
If we replace the Sophos generated appliance certificate with one from a trusted CA $$$, this issue should go away because the certificate length will be shorter and it will come from a CA giving snoopy venders warm fuzzies.
However from a management perspective, what will break? Will our REDS stop working correctly? Will we have to reissue SSL VPN certificates for VPN users?
What about Site to Site VPN?
This thread was automatically locked due to age.


