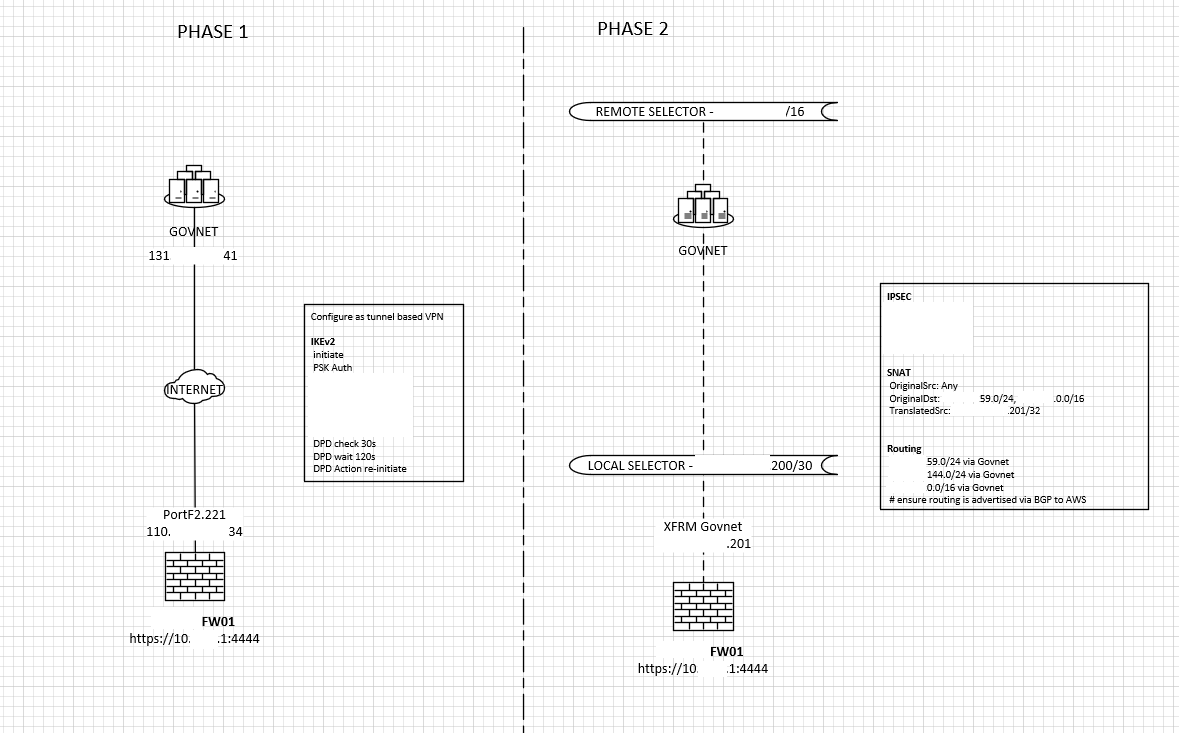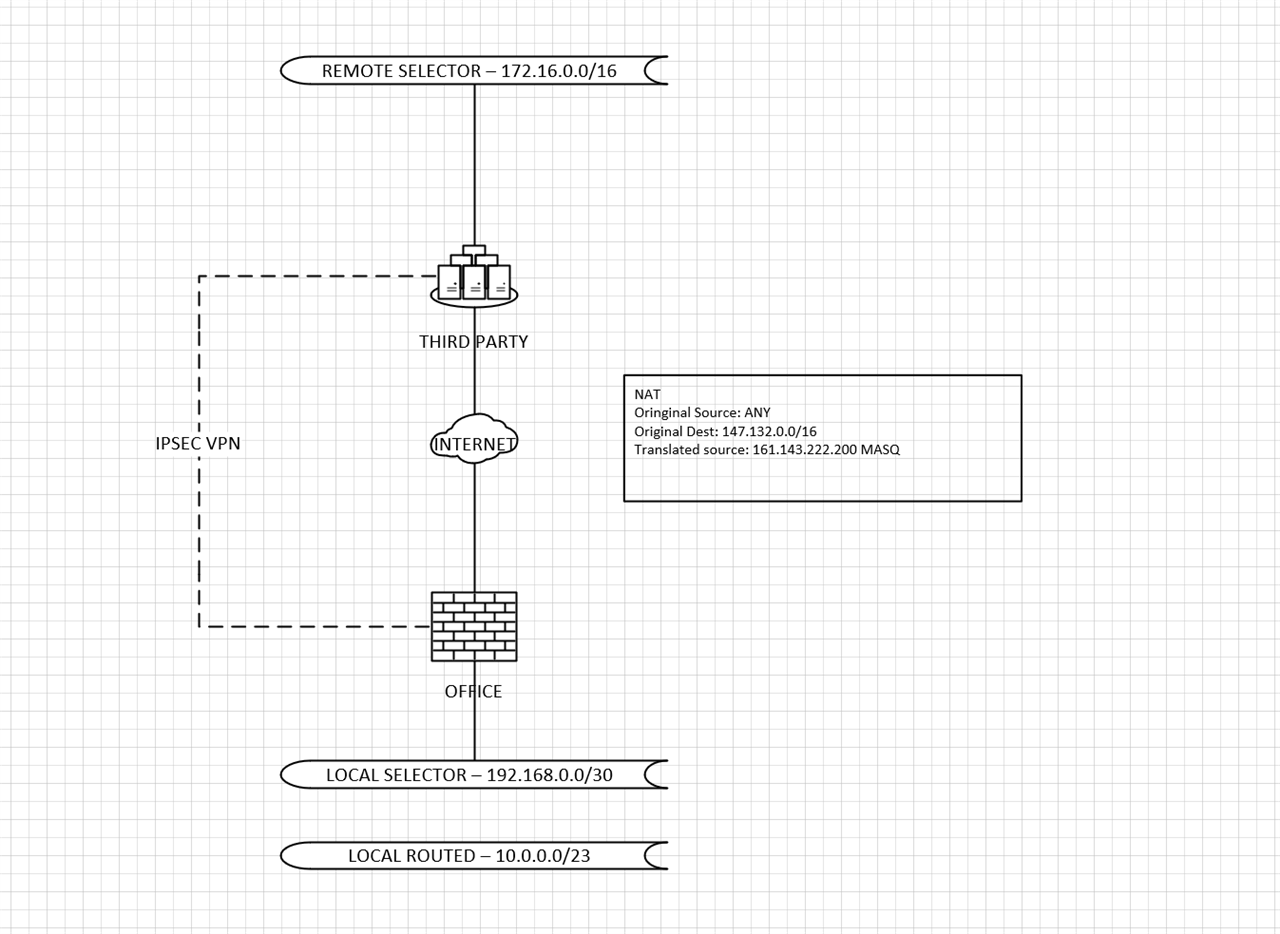
I'm migrating from a UTM to an XG so i'm trying to replicate a config that already existed.
I have the IPSEC VPN setup and the tunnel comes up.
The VPN selector on my side only has a /30
I need to have the rest of the organisation talk through this VPN as well, I simply want to source NAT everything from 10.0.0.0/23 through one of the IP's in that /30.
I have tried using the NAT option in the IPSEC configuration, but this doesn't seem to work and I can see a pop up that tells me the subnet mask needs to be the same both sides (suggest it would attempt a 1:1 mapping).
I also tried using a regular NAT rule but that didn't seem to work either.
XG is on 20.0
Any help would be appreciated, Is this doable?
This thread was automatically locked due to age.