We have a main HA firewall XG210 pair, currently in 19.0 latest MR release, connecting to various XG and XGS units in the field.
We have dedicated links to the far end locations, and on the XG210 at the head office it is configured as being over LAN zone.
There are also gateways with the lan interface specified in the LAN zone.
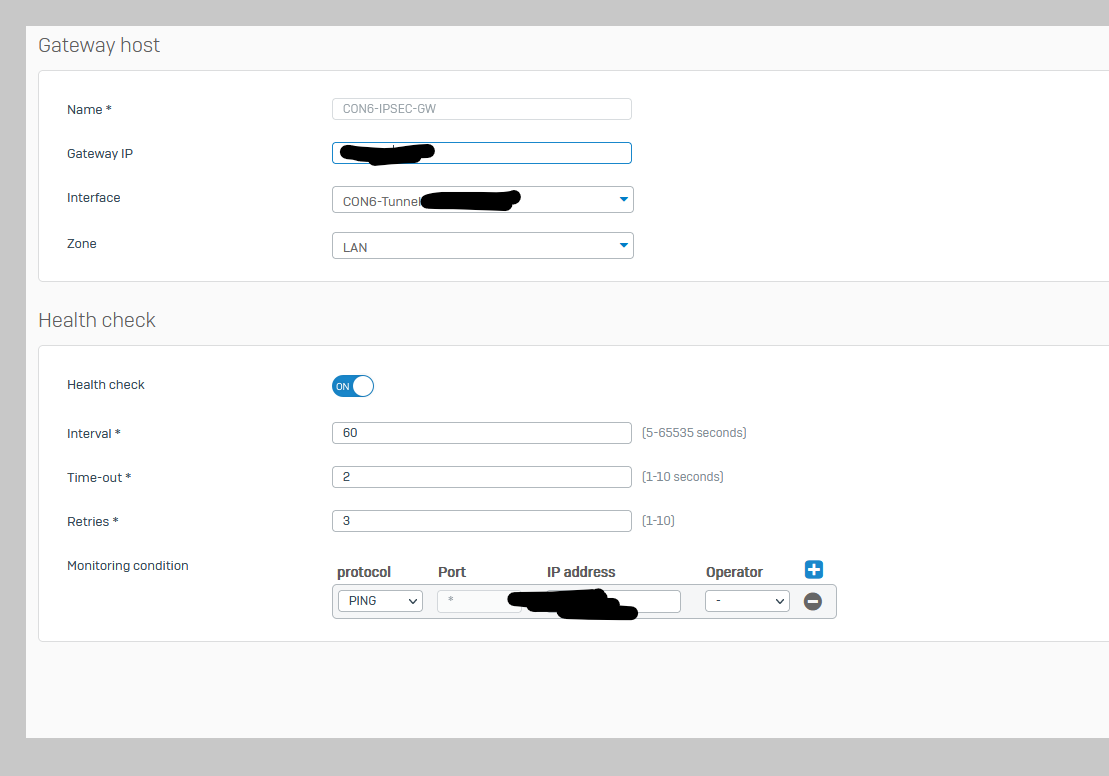
There are backup links to these remote sites over IPSEC P2P VPN (route based, tunnel mode).
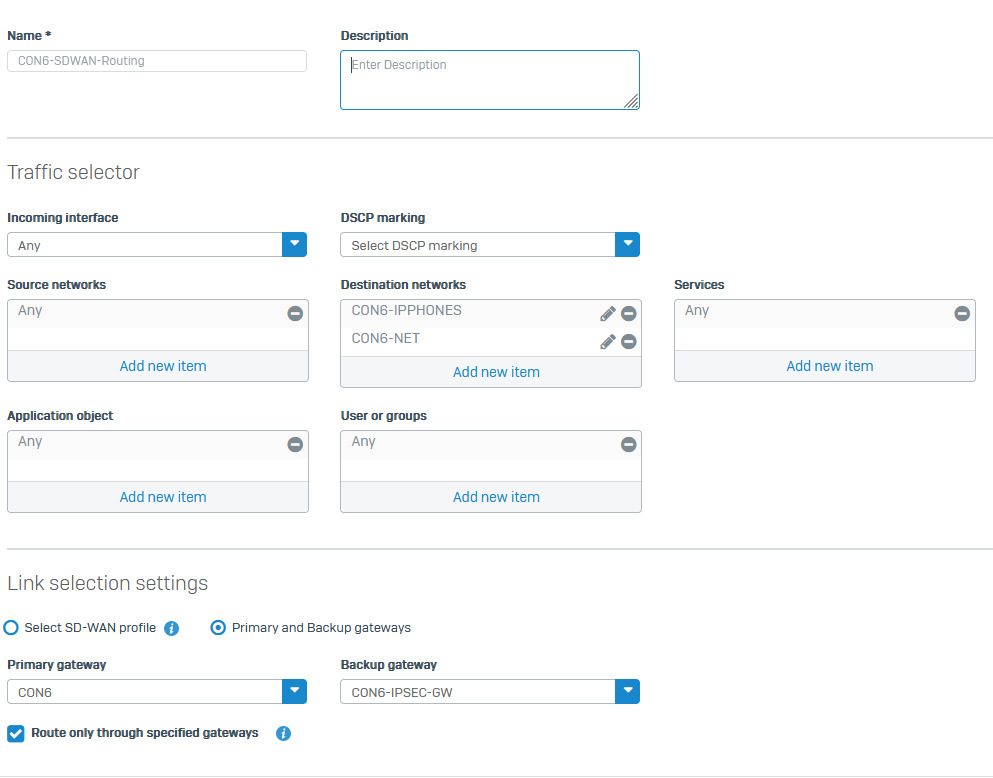
We then use SDWAN rules (no policies yet) to specify primary and backup gateways, and have even tried checking the box for only use specified gateways.
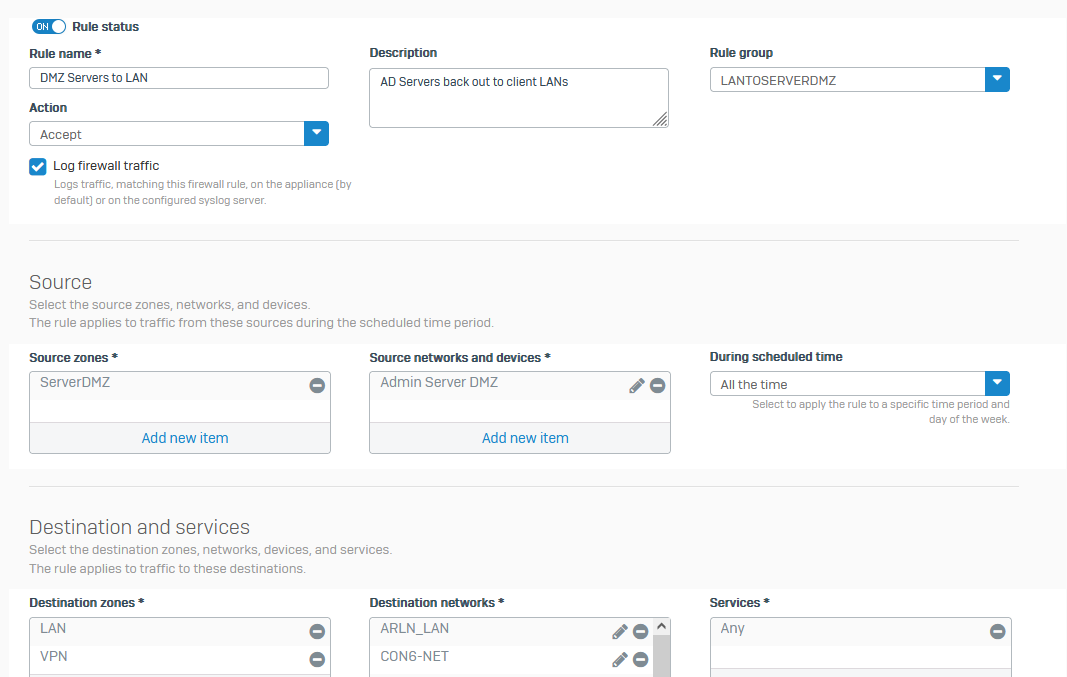
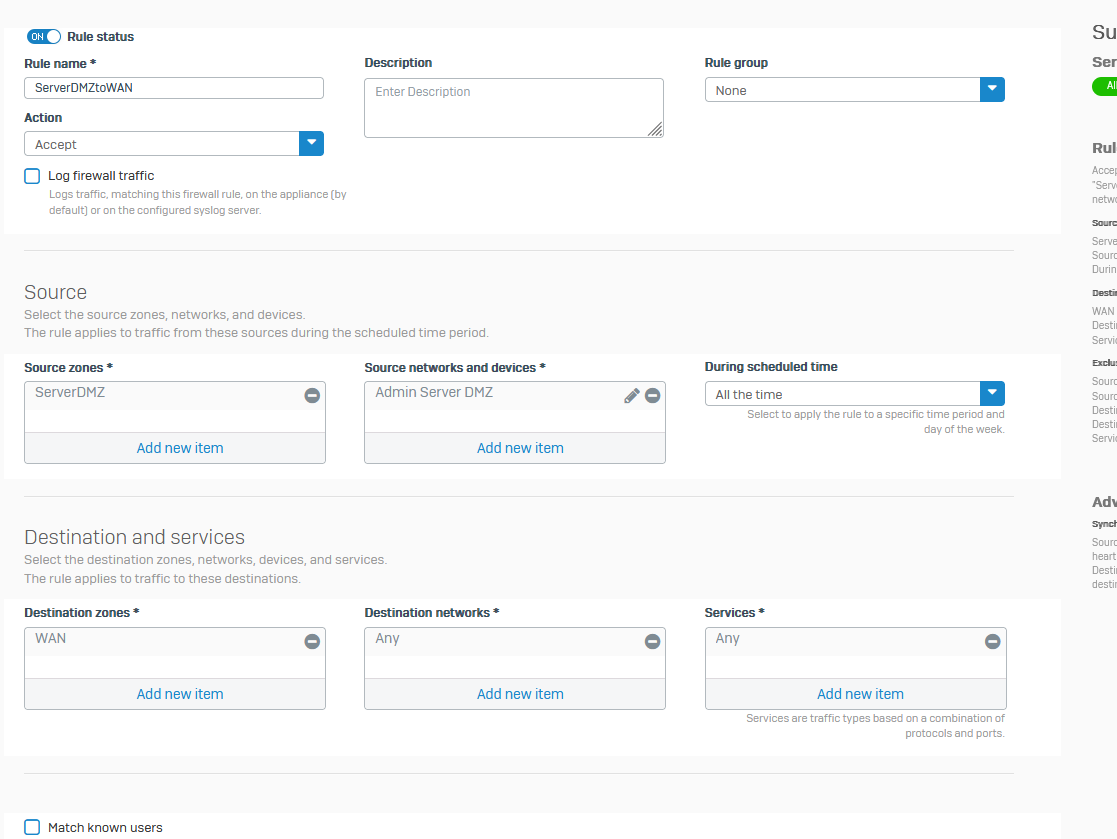
All of the routing and failover works ok, however during debug of an issue I discovered that instead of my firewall rule for "ServerDMZtoLAN" which has specific LAN subnets and source as the dmz, destination as the LAN, it is using my other firewall rule for the default "serverdmztoWAN" with source also serverdmz but destination is WAN, and when checking WAN it clearly shows ports 2 and 4 as my internet services to the head office.
When I run a debug in the policy tester, it always chooses the WAN facing firewall rule, even though all the gateways/firewall rules/sdwan policy is set to use LAN next hop as first choice, and VPN as next choice, never WAN zone at all.
If I add an exception to the WAN rule, it is entirely denied on the firewall.
For sites that are only on dedicated private links with no internet backup yet, I use static routes and they work fine with the firewall rule matching the serverdmztoLAN.
It seems like using sdwan rules, even if all the gateways and firewall rules are set to use lan/vpn, sdwan policy automatically ignores all of this and makes it use wan fw rules only?
When I do a traceroute is always locks up the web interface to any subnet that is using sdwan.
when I do a route lookup, it always says the far end is on the public internet which is not the case at all, even though I have all the gateways and routes and the failover technically works.
is this something fixed in later versions of sophos firewall? I'm configuring a newer unit to replace the HO but seems like every unit even ones running 19.5 latest MR suffer this issue of thinking the route is out the public internet and not using the gateways and sdwan rules at least when doing troubleshooting.
This thread was automatically locked due to age.


