Hi,
for some reason every SSL VPN client is quite randomly disconnected from the SSL VPN server (Sophos XGS87w): sometimes after only a few minutes, mostly between 15 and 20 minutes. Running a ping from the client side to a machine in the server network does not help to keep the connection alive. The VPN connection works fine as long as it is connected, though. The client is assigned the correct static IP address.
Here are some additional details:
- firmware: SFOS 20.0.0 GA-Build222
- the Sophos XGS is located behind a DSL router, the interface port 1 (of the Sophos FW) is the LAN port, port 2 is connected to the DSL router. The DSL router is the gateway to the internet.
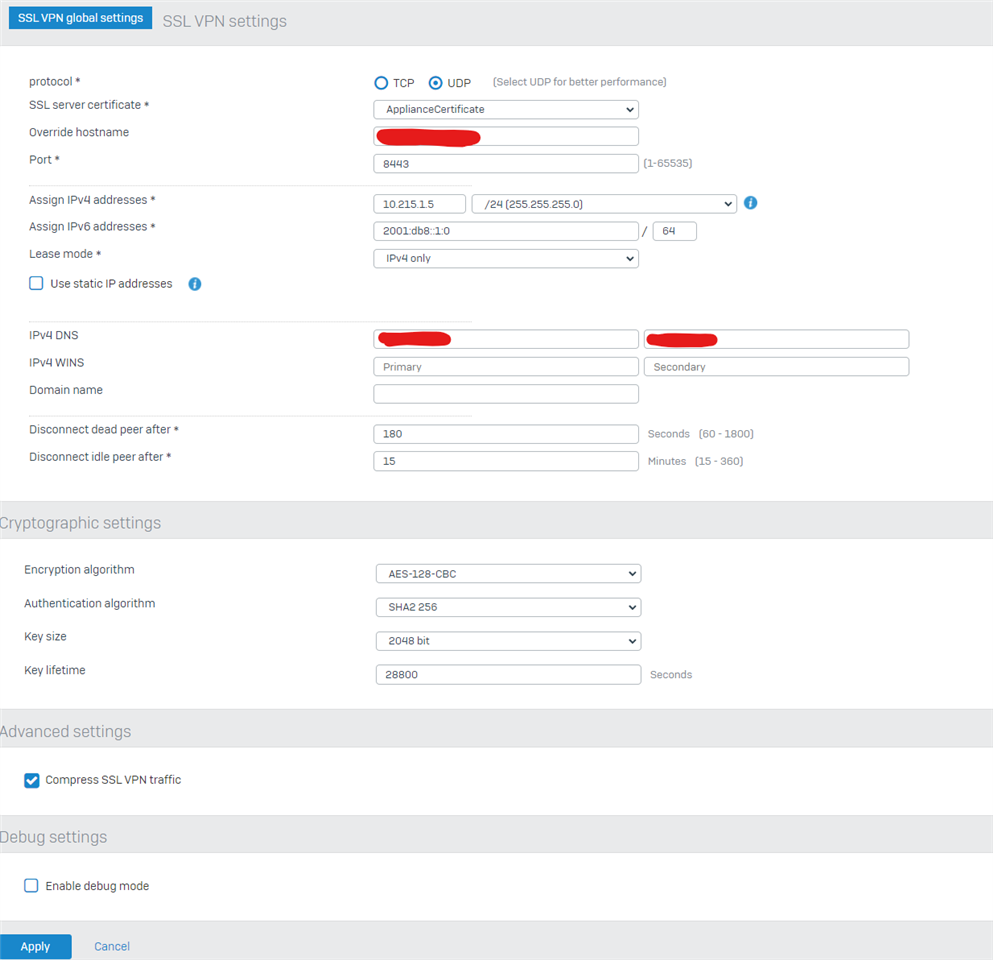
- SSL VPN global settings: protocol: TCP, override hostname is set to a domain name, Port: 8443, use static IP adresses is active, (every client has a correct "SSL VPN IP address" set), disconnect dead peer after 120 seconds, disconnect idle peer after 360 minutes, key lifetime: 36000 seconds, compress SSL VPN traffic is ON.
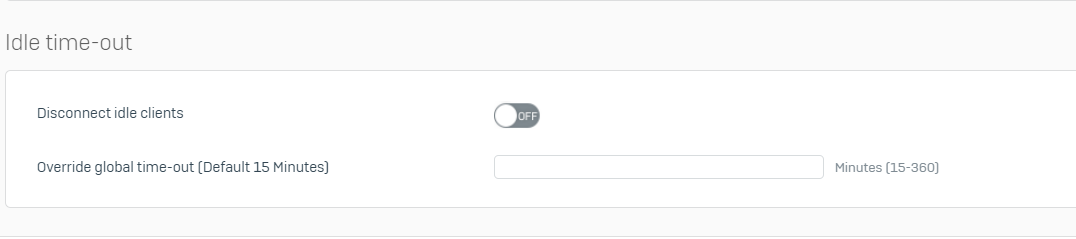
- SSL VPN settings: use as default gateway is OFF, permitted network resources is set to the internal LAN on the firewall side, disconnect idle clients is OFF.
This log shows the same user being disconnected quite often in a short time.
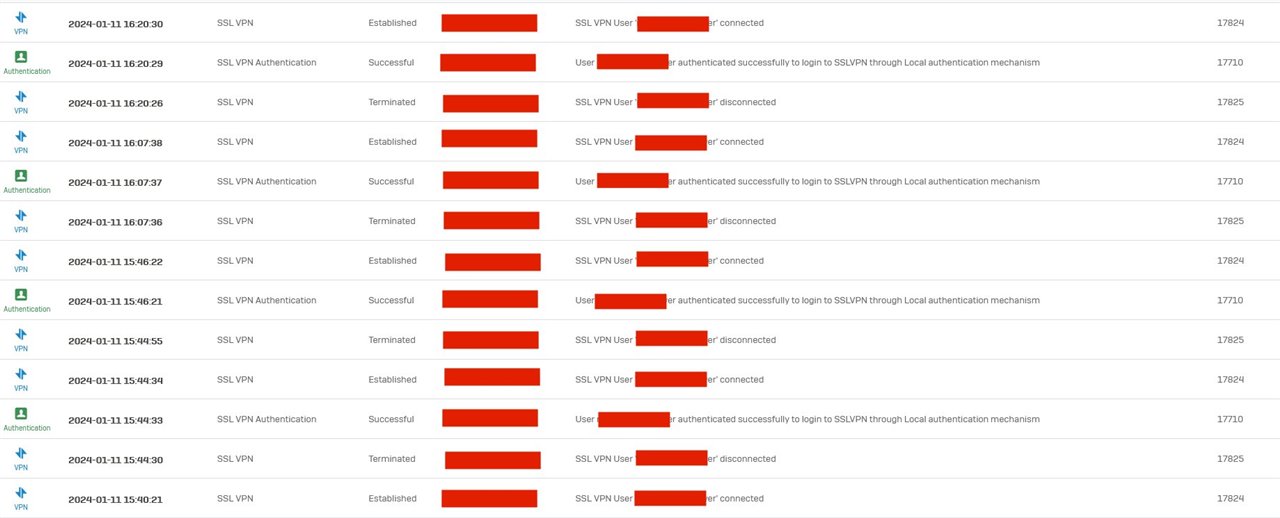
None of my time settings corresponds to the times when the client is disconnected. The client itself is not disconnecting manually, of course.
Any idea where this is coming from?
This thread was automatically locked due to age.