Hello all,
I have a specific NAT question and problem, the reason would be, that am not a native or excellent networking guy... so learning by doing and reading specific when needed. Maybe someone could help me.
In my home network I use a XG as firewall with 2 different physical subnets for LAN and switching, some WLAN ssids in separated zones and some kids and a wife here. To protect them I have a pihole dns virtualized for all dns requests in our home.
Because some smartphones and browsers trying so use a "secured dns resolver" automatically on its own choice, I tried some tricks to prevent such overrides.
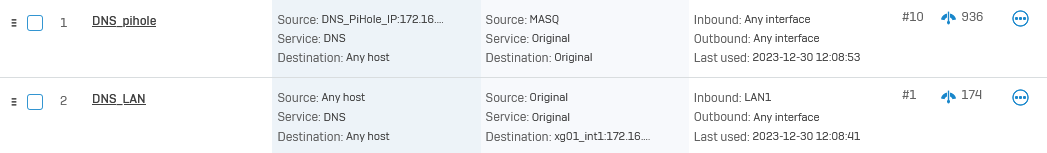
For that I have added a NAT rule for each network which looks like the following:
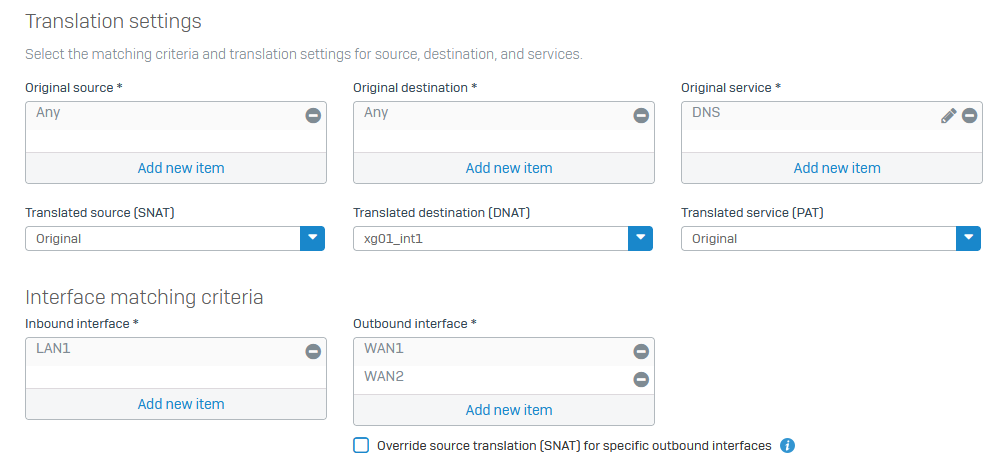
So every directly try on another externally dns should be affected.
Further there are policies which denying "dns over https" and some app filters for dns and proxy etc.
Global dns settings:
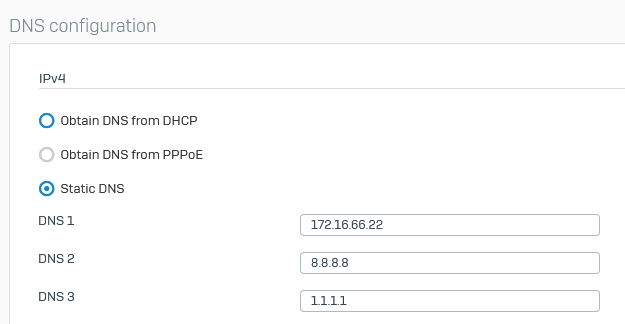
dns settings on LAN1 / dhcp:
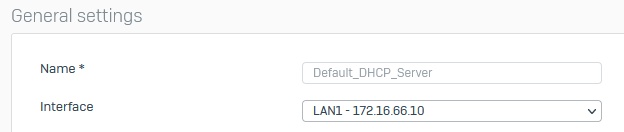
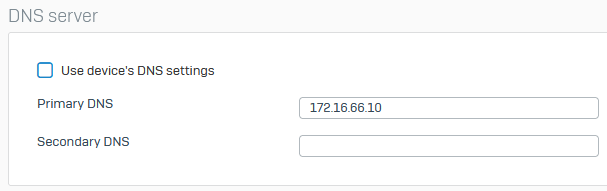
dns settings on other networks / dhcp:
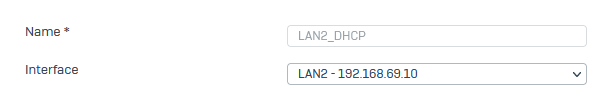
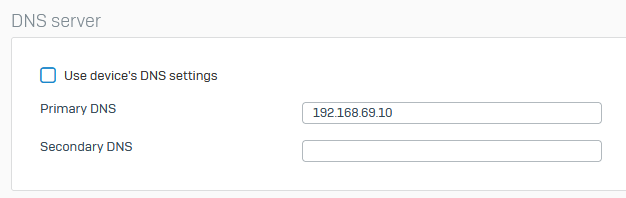
According to several tests it looks great and I think all dns requests for external will be handled by the pihole.
BUT: The browsing speed and load times for websites is incredible slow (3-10 sec) for me directly in LAN1, which seems to be caused by the NAT rule.
When disabling, the speed is normally like attached directly to the router behind. In LAN2 or WLANs there is no problem with browsing.
So can anyone explain me that and maybe tell me a solution or different way so solve my wish for the pihole-dns-only network?
Thanks a lot and regards,
Andy. :)
This thread was automatically locked due to age.