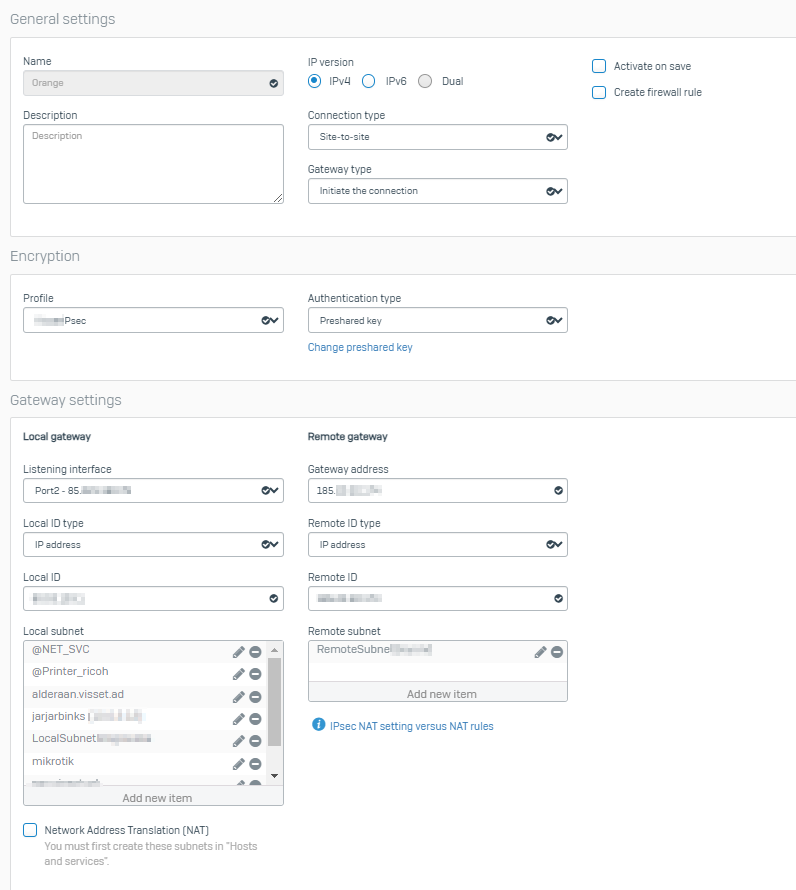
Hi,
We have an IPSec s2s connection, and there is a remote subnet 10.0.0.0/255.255.255.0.
Migration was done with configuration export/import and it seemed almost everything migrated successfully (only some firewall rules involvind ad users where missing).
On new device I can't ping or access remote AD server from xgs, which is crucial (AD controller).
- Old device (working):
- ping 10.0.0.100 (remote server) from sophos ssh - OK
- ping 10.0.0.110 (remote AD controller) from sophos ssh - OK
- ping 10.0.0.110 (remote AD controller) from local PC - OK
- packet capturing: packet is sent through ipsec0 interface from 10.0.1.1 (Port1 - LAN). No NAT or firewall rule applies.
- New device (not working):
- ping 10.0.0.100 (remote server) from sophos ssh - OK
- ping 10.0.0.110 (remote AD controller) from sophos ssh - FAILS
- ping 10.0.0.110 (remote AD controller) from local PC - OK
- packet capturing: packet is sent throuth ipsec0 interface but from 169.254.234.5 (ipsec0 interface). No NAT or firewall rule applies.
What may be causing the difference?
This thread was automatically locked due to age.