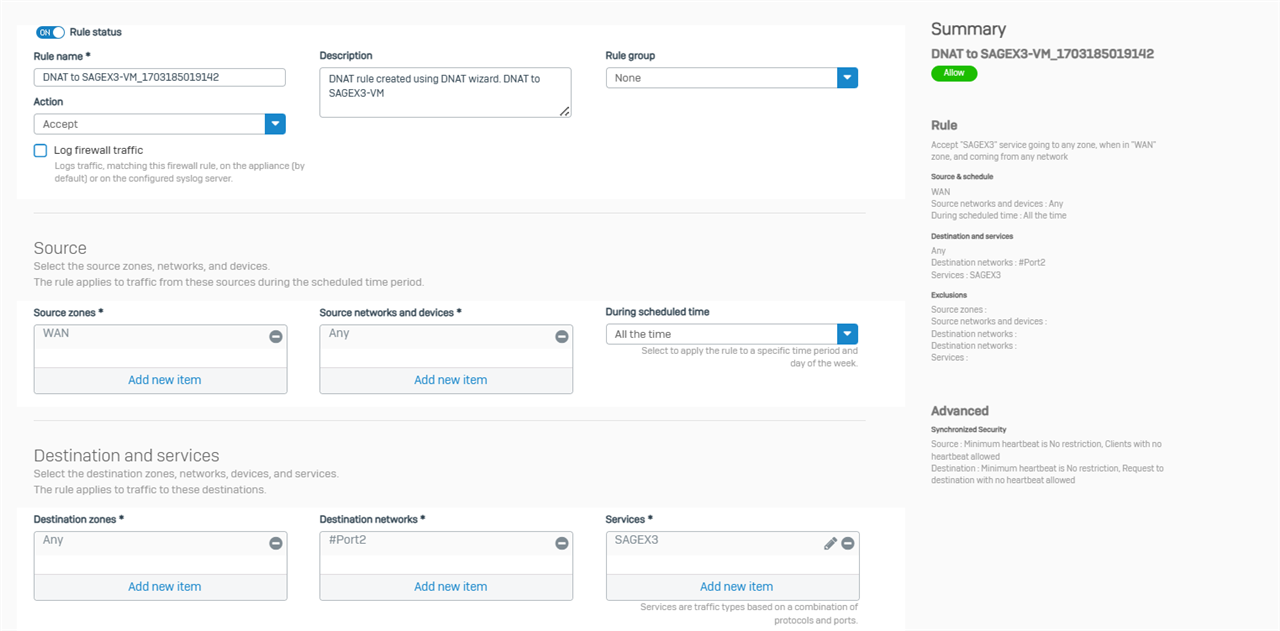
Hello Please be informed that i have an ERP which is accessible locally "LAN" but when i tried to access from outside im not able to, however i set up a DNAT rule please find below the screenshot it is in french language
i set up port forwarder on the router
Please can you assist me to solv this issue , iperfomed test with telnet ip affected to port WAN & numer of port opened
This thread was automatically locked due to age.