2 XGS connected via ISP PTP fiber as primary.
Each XGS has a second ISP which will be used for a IPSEC tunnel in case the primary link fails.
Currently OSPF is in use.
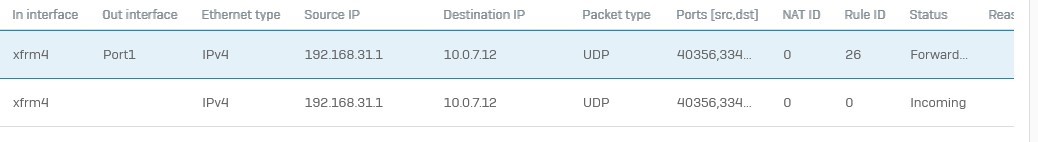
I have a IPSec VPN between 2 XGS using a tunnel. Both XFRM interfaces are 192.168.31.1 and 192.168.31.2.
Each XGS can ping the other address via the tunnel VPN. Doable from the ping under diagnostic.
Sophos has not added the XFRM interfaces to diagnostics so I can't tell it to traceroute via the XFRM interface.
I want to make sure rules / polices are working before adding / changing OSPF.
Is there a way to test this from the Advanced Shell or Device Console?
I want to prevent what I did the other day. I added the tunnel network info to OSPF on each XGS as shown on a help document. After I did this, the connectivity between (2) XGS went DOWN. Thankfully, I was able to login via central and remove the changed OSPF. Still not sure what I did wrong, other than I think I did not have a rule in place for one of the XFRM interfaces.
Ideas?
The scenario above is for connectivity between 2 offices. Should we use OSPF, or Sophos SDN? Can both be used at once without issues?
This thread was automatically locked due to age.