Sophos Firewall is NOT very intuitive so far. Nothing inbound works...but the default rules to let everything outbound does. So figured id ask the community.
I've reverted to the simplest test I can think of....Port forward ICMP from WAN to a LAN workstation..
First turned on ICMP on the WAN adapter to make sure it was listening from outside. It was so I turned ICMP off.
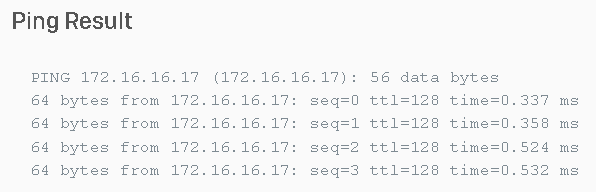
Second made sure the Firewall can reach the workstation using its LAN connection, it can
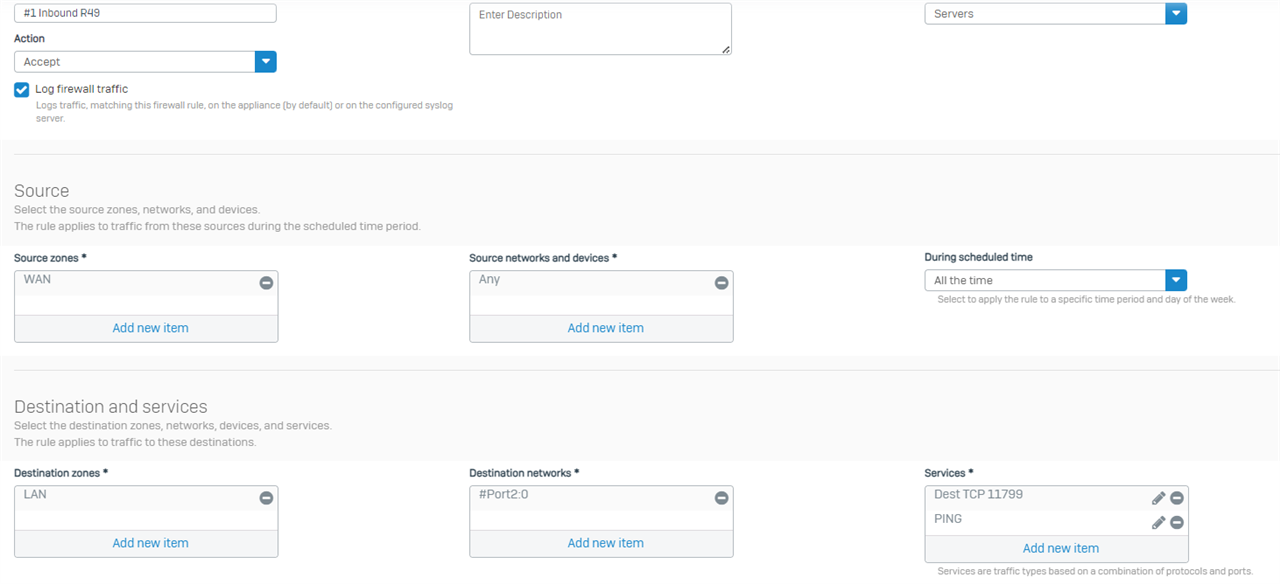
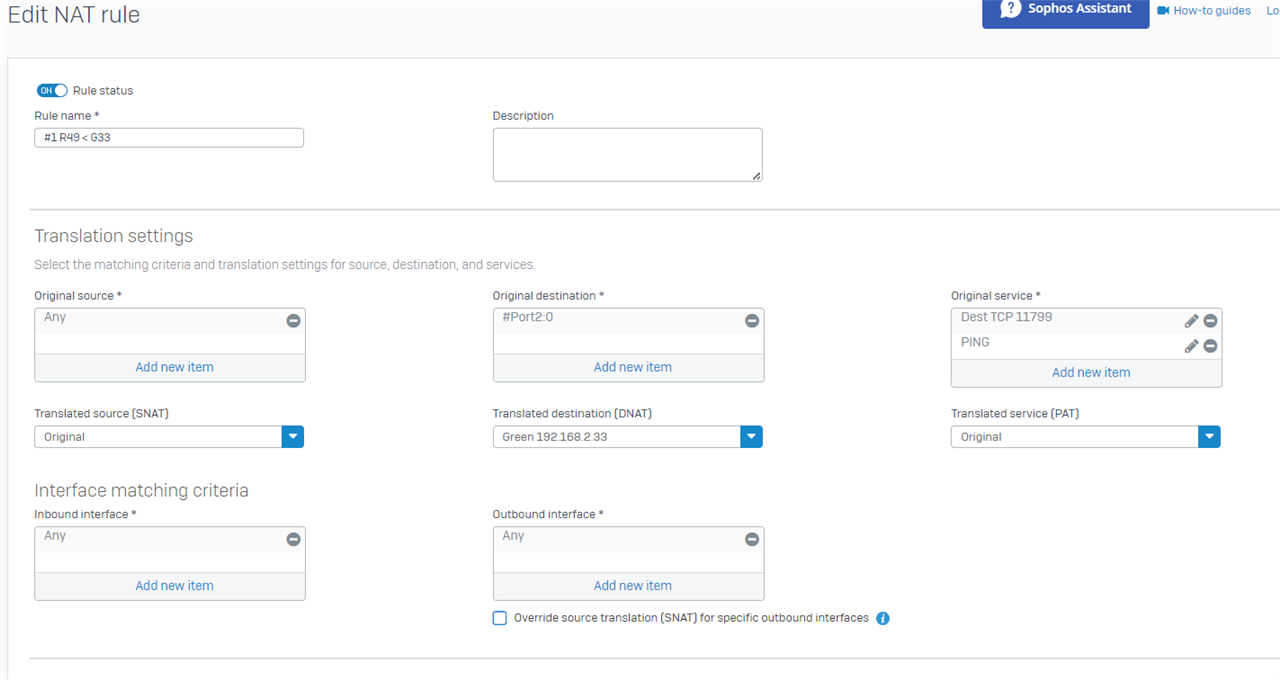
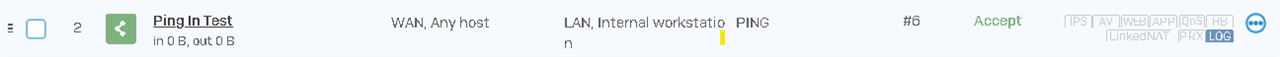
Created the Rule,
WAN, Any, to LAN, workstation 172.16.16.17 with the predefined PING
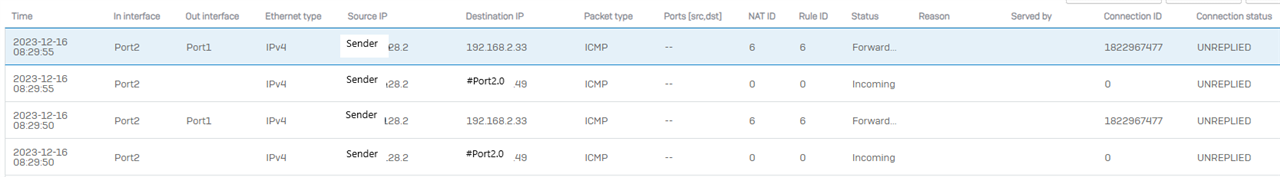
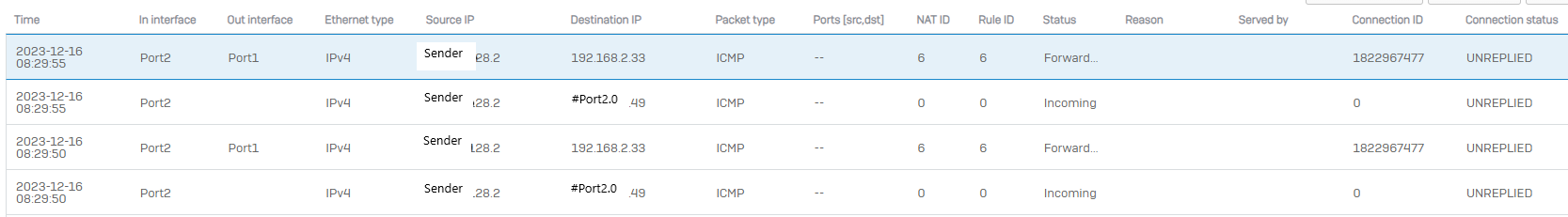
.Nothing. System isn't logging it. Just nothing. Cant forward anything.
At this point I cant test the system because it doesn't even port forward. Lots of time wasted trying to figure out why this easy test is so hard. Thanks
This thread was automatically locked due to age.