Hi All,
I would like to connect my Unifi Dream Machina Pro (UDMP) router to Sophos XG Home (SFOS 19.5.3 MR-3) installed on a separate computer with two LAN ports. What I want to do is not obvious and I don't know if it's even possible. In general, the entire network, VLANs, and basic firewall rules are defined in UDMP and it should stay that way, because I am very happy with it. What I miss is the more advanced New Generation Firewall configuration. No SSL Inspection, web filtering configuration, DPI etc. And I wanted to use SFOS for this.
Of course, I can put SFOS in bridge mode, but then I have to pass all the traffic through one interface, which is not necessary and will burden SFOS with analyzing traffic that I do not care about. But in UDMP I have 2 WAN ports and I can define that a specific device or VLAN uses one or the other WAN port. My ISP only provides an ONT with one port, so the idea is to go from the WAN2 port in UDMP, connect to the LAN interface in SFOS and the WAN from SFOS to the LAN in UDMP. This means that for selected devices the traffic actually goes through a double firewall, and for less risky ones only through a UDMP firewall.
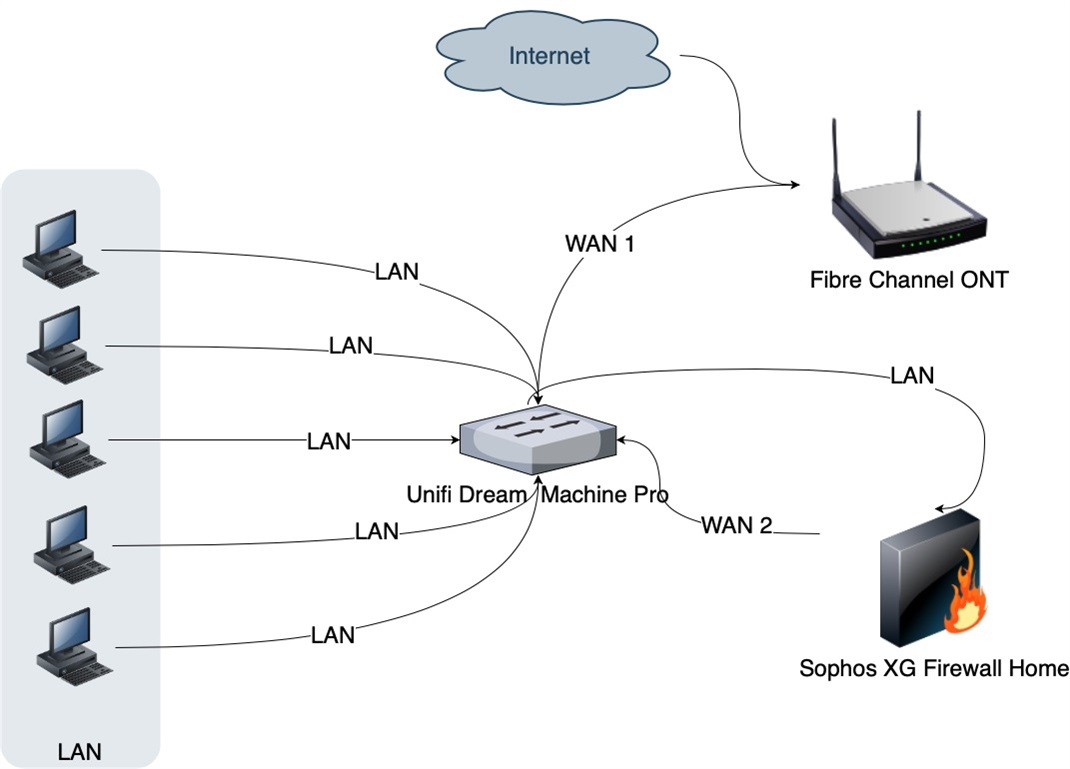
In SFOS bridge mode this causes a loop and freezes the entire network, but in router mode it even works. Unfortunately, NAT (which I cannot turn off in UDMP) makes all traffic anonymous in SFOS and I cannot set rules for specific devices. Is it possible to somehow set this traffic to transmit information about the source IP? I tried to do something about setting up a local IPv6 network, but without success. The LAN port in SFOS would have to pretend to be an ISP and provide a network prefix, but it doesn't do that.
I will be grateful for any tips.
This thread was automatically locked due to age.


