Hi, maybe a dumb question but what does the command really do?
Maybe it is because of my special setup with the BO firewall tunneling all traffic to the HO firewall. But as far as I understood the - very well hidden - comparison whenever I want to do DHCP relay over IPsec I will have to add a system ipsec_route to the DHCP server using the IPsec tunnel.
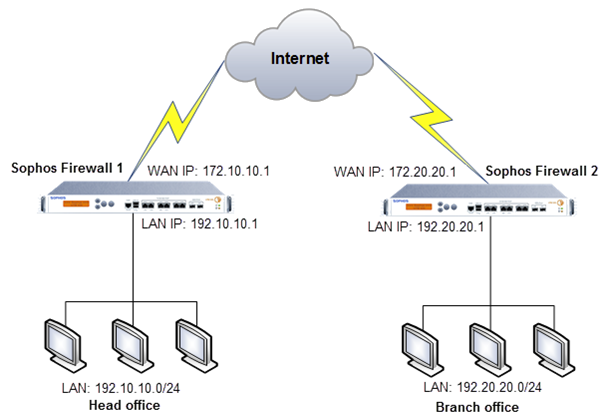
Today I played around with DHCP relaying over a (policy based) VPN. I do not see any need for the system ipsec_route at all. I have set up some rules in advanced firewall via console for system-generated traffic and as far as I can tell everything is working fine.
My BO firewall has no MASQ rule active and a „local networks to Any“ VPN connection.
For every DHCP scope I configured a advanced firewall rule for sys traffic to DHCP server in HO, mask 255.255.255.255 interface where i want DHCP relay to be in place, SNAT to the firewalls IP in the specific local network (e.g. 10.0.0.1 in 10.0.0.0/24). One rule for every vlan interface where I want DHCP to be in use.
Then a general route for the firewall pointing to 0.0.0.0 0.0.0.0 and SNAT to one of it‘s local IPs (for internet connectivity).
In DHCP relay I configured relaying to the DHCP IP and with „IPsec checkbox checked“.
Maybe someone can answer me the following question, why my setup from above should not work over a tunnel interface VPN.
I didn‘t test it until now but I see no point why it should not work.
This thread was automatically locked due to age.