Hello everyone,
Recently i noticed a bunch of tickets regarding the following.
i want to go on facebook, but facebook is blocked.
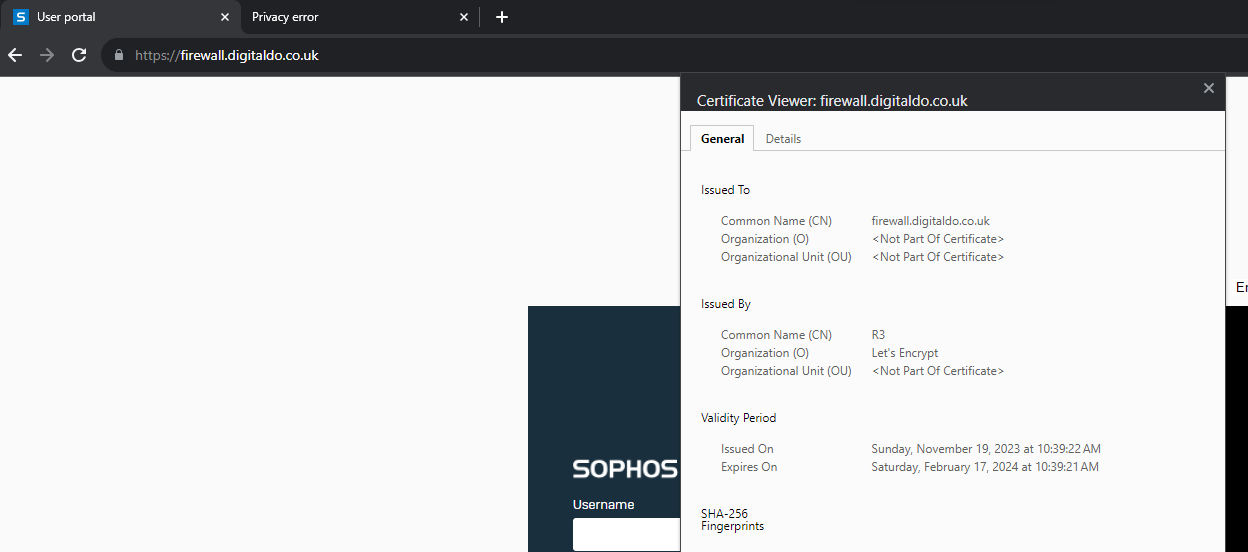
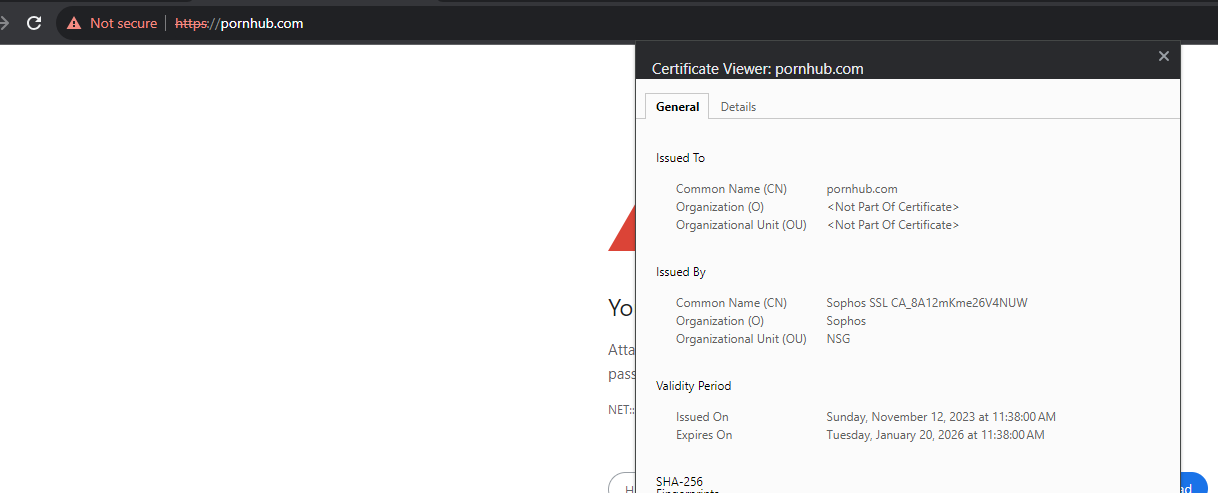
instead of the blocked page i get Error code: SEC_ERROR_UNKNOWN_ISSUER(firefox) or NET::ERR_CERT_AUTHORITY_INVALID(chrome)
it works fine if i install the sophos certificate.
I understand that the certificate must be pushed to end devices, however i can not ask guest users to install the sophos certificate.
I also understand that that this can be secured with a public cert.
This seems so random, as for some customers works just fine, but for others not.
I can not ask 200+ customers to buy a certificate to display a blocked page on guest networks.
Can anyone advise?
Kind regards,
Dragos
This thread was automatically locked due to age.