Good morning,
I have two clusters of XGS 2100 in HA (Active-Passive) running with the firmware version 19.5.3 MR-3-Build652. This is my current setup in both of the clusters:
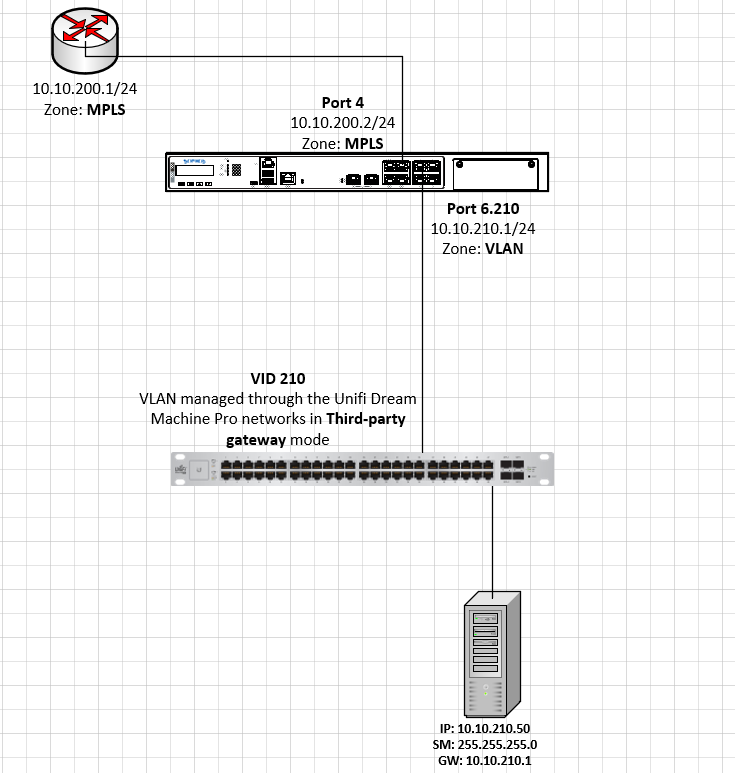
WAN1 (ISP) > Port2
LAN > PortF1
HA > PortF2 - PortF2
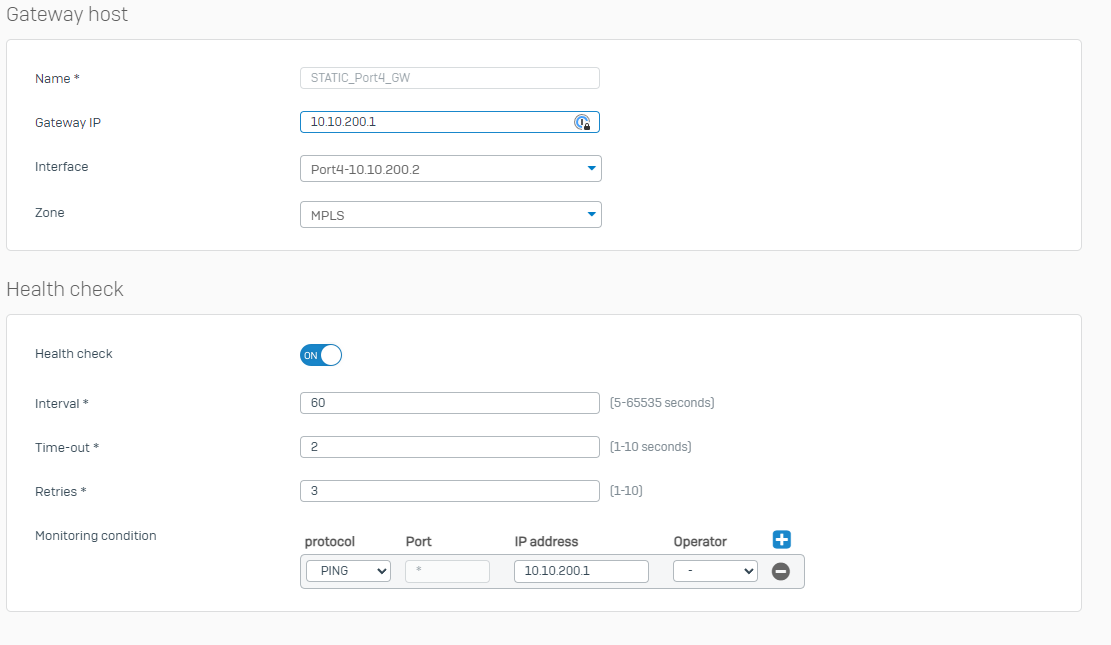
As per object, in one of them, I need to set an indipendent second WAN interface (WAN2) for connecting a MPLS router that will be reachable only from a VLAN. This operation is quite simple and I made it from Network > Add Interface. I set the IP information, the WAN zone and the port.
The desired setup would be:
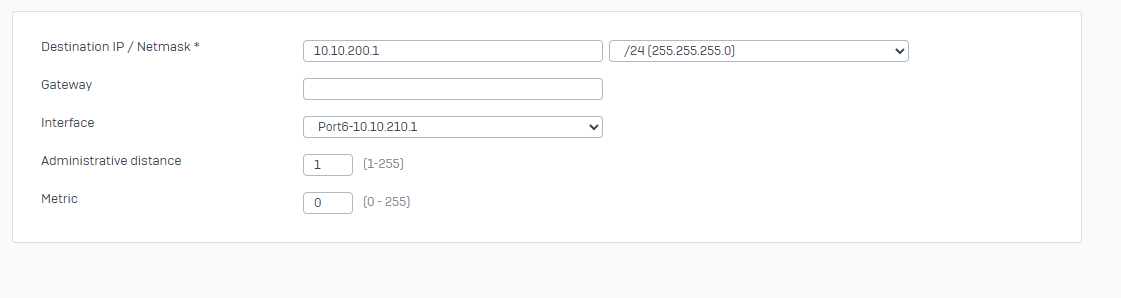
WAN2 (MPLS with NO Internet access) > Port4
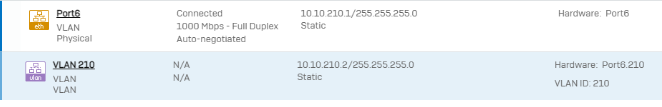
VLAN > Port6
However, after I enable the port and I plug the cable in, that will connect the MPLS router to the Port4 of the firewall, the Load Balancing (that I don't need) starts to work and most ot my users lose the Internet access (WAN1). Even configuring the weights, for each gateway, from the WAN link manager, is not helping at all.
Furthermore, I tried to set my firewalling rules so part of the traffic gets forwarded to the WAN1 (I selected WAN from the Destination zones and Port2 from the Destination networks) and some to the WAN2 (I selected WAN from the Destination zones and Port4 from the Destination networks) but it is not working at all.
Do you have any suggestions or any idea on why this setup is not working? Please let me know if you need further information, I have been vague just to explain the main issue.
As a temporary workaround, I just created a VLAN on the switch, and on the XGS cluster, and connected the MPLS router directly to the tagged switch port. Of course, this is not sustainable and this is not the setup I want.
Thank you and have a nice day!
Best regards.
This thread was automatically locked due to age.