Dear community,
i think we are suffering the same problem mark57165 described in his post 'IPS Service - with no FW rules - Prevents Certain Sites from Loading'.
Our Situation:
SOPHOS XG / XGS Firewall
in Bridge Mode
no firewall rule / no SSL/TLS inspection rule for the problem connections
multiple IPv4 Subnets on the LAN side
SSL/TLS connections from one local subnet to another local subnet time out
Unsatisfying workarounds:
- disable SSL/TLS inspection completely
- stop IPS Service
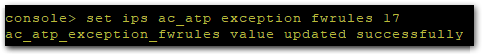
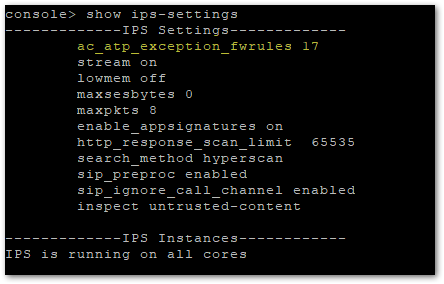
- add bypass-stateful-firewall-config rules for the local subnets
Is someone facing the same problem?
Did someone find a solution?
Regards, Nicolai
This thread was automatically locked due to age.