I have a server on a remote site that needs to open port 80 to the internet from time to time to get a certificate. AT the moment - I cannot get this to work.
Details:
Sophos UTM on main Internet Connection at HQ: 192.168.200.0/24. Public IP A.B.C.D.
External Port is #2
Internal Port is br0, considting of Ports 1, 3 & 4. Internal IP is 192.168.200.1
Remote office on RED device: 192.168.201.0/24, Internal IP is 192.168.201.1
Server#1 on RED Network: 192.168.201.11 with .1 as gateway
VPN between UTM and Red. This is a leased line at the HO end and a VDSL at the remote site
For testing purposes I have an FTP Server installed on Server#1 (201.11) as 80 is not available all the time. This is accesible from the head office network.
What I need to do is accept incoming FTP (later to be HTTP) connections on the main firewall and pass them through the VPN to Server#1 which should then respond back through the VPN and out the main UTM bck to the originating client.
Attempt#1: I tried setting up a DNAT rule first, it didn't work and my understanding from searches that this is not expected to work,
Attempt #2 : I set up a NAT rule as below
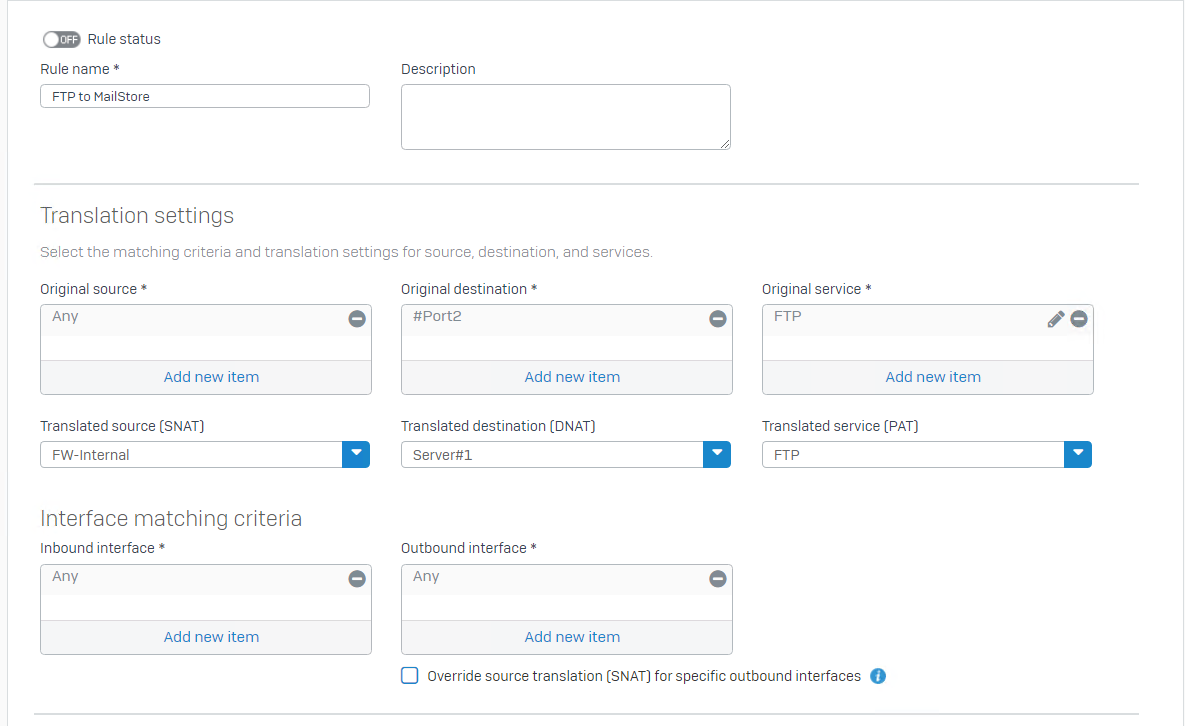
I then setup a Firewall Rule
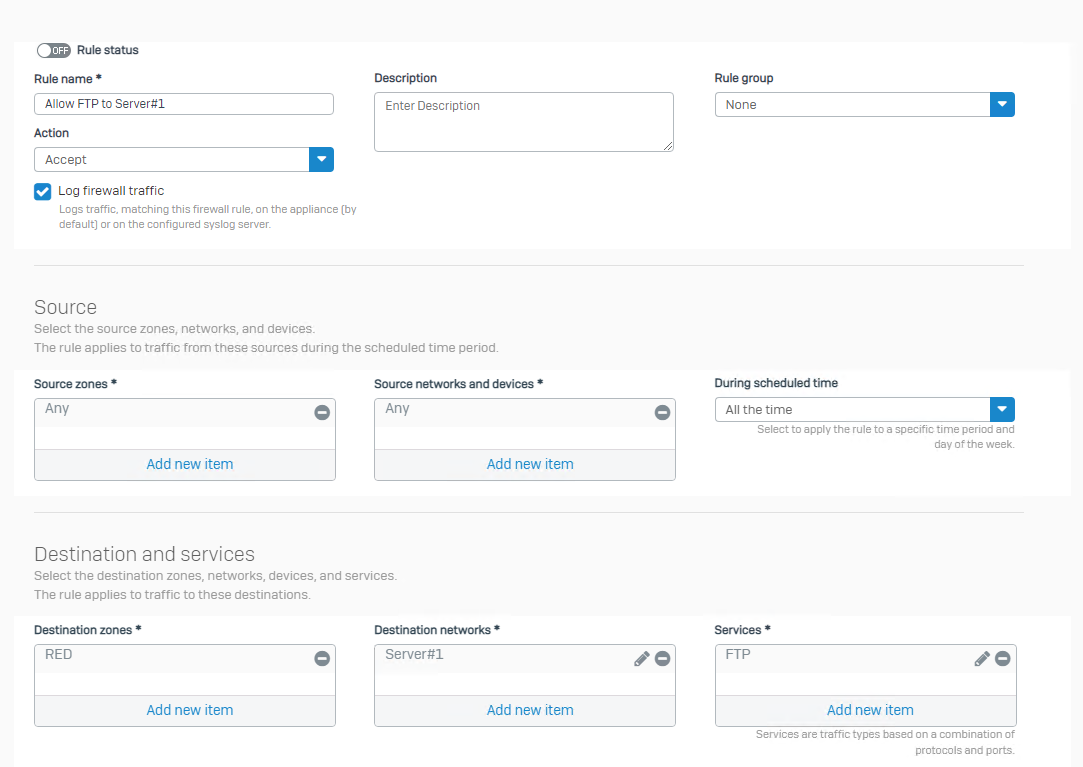
Butt his doesn't work - the FTP is not available from outside
Either this isn't possible (searches seem to say it is) OR (far more likley) I am not doing it right.
Anyone got any insight for me?
[The good news is that in 6 months or so the leased line will move to the office - which is becoming the head office so this will cease to be an issue. The bad news is that I need to get this working first]
RED VPN is standard/split which is I guess the major problem here
My thoughts are that the packets are probably reaching Server#1, but are being returned by the RED external port and IP address, which is never gonna work. I had hoped that using "Translated Source" as FW-Internal (192.168.200.1) would solve that problem causing the packets to return to the UTM.
This thread was automatically locked due to age.

