I'm trying to copy a PXE Boot Optin from the DHCP Server of a UTM to Sophos XGS
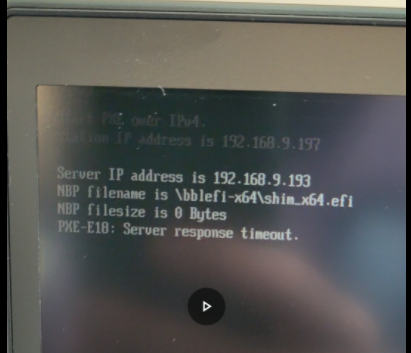
The problem I face is, the Boot Client uses the IP-Address of the Firewall/DHCP Server as TFTP Server instead of the value provided in the Option 66 (Next Server)
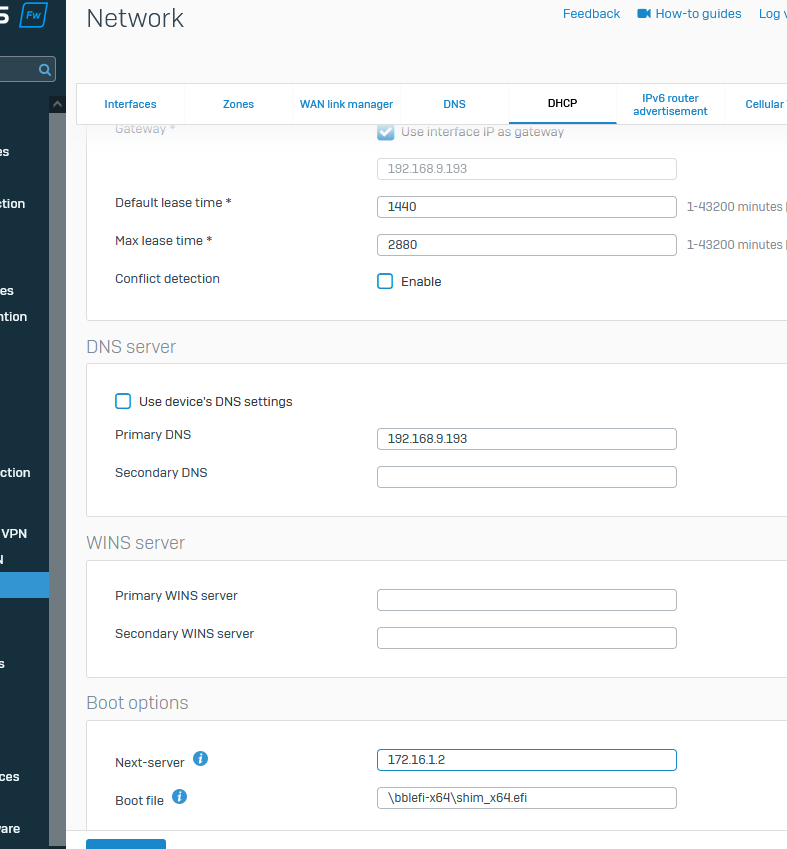
I tried with GUI
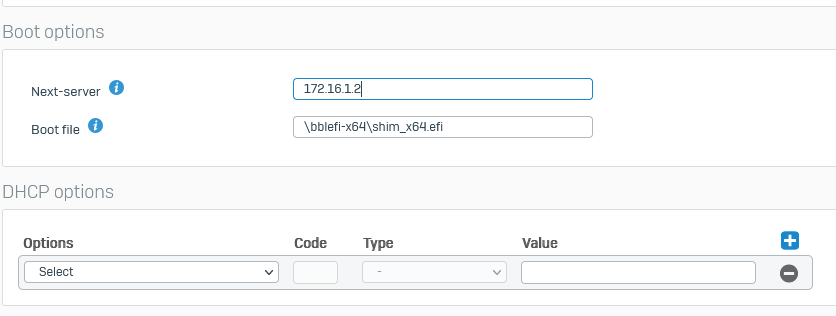
and with CLI
system dhcp dhcp-options binding add dhcpname my-dhcpservername optionname TFTP_Server_Name(66) value '172.16.1.2/bblefi-x64/shim_x64.efi'
console> system dhcp dhcp-options binding add dhcpname my-dhcpservername optionname TFTP_Server_Name(66) value '172.16.1.2'
DHCP option TFTP_Server_Name(66) added for DHCP Server my-dhcpservername.
console> system dhcp dhcp-options binding add dhcpname my-dhcpservername optionname Bootfile_Name(67) value '\bblefi-x64\shim_x64.efi'
DHCP option Bootfile_Name(67) added for DHCP Server my-dhcpservername.
console> system dhcp dhcp-options binding show dhcpname my-dhcpservername
Options Configured from GUI
---------------------------
xxx-removedbyauthor-xxx
Options Configured from CLI
---------------------------
TFTP_Server_Name(66) "172.16.1.2"
Bootfile_Name(67) "\\bblefi-x64\\shim_x64.efi"
and get the same result at the client:
192.168.32.1 is the sophos firewall
it should use 172.16.2.1 but it does not
172.16.2.1 is behind a IPSEC-VPN from the perspective of the Client.
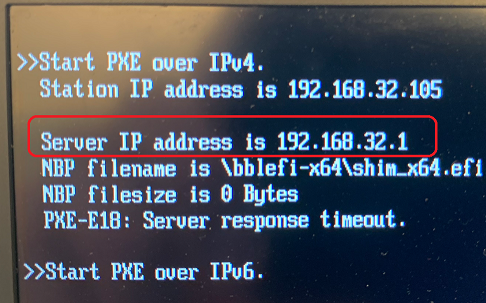
That is the IP-Address of the Firewall that is also the DHCP Server.
Then I tested this - I found it in an other post here from Sophos Staff but with that value, the Client did not receive an IP Address at all. It already looks ugly.
console> system dhcp dhcp-options binding add dhcpname my-dhcpservername optionname TFTP_Server_Name(66) value '172.16.1.2/bblefi-x64/shim_x64.efi'
DHCP option TFTP_Server_Name(66) added for DHCP Server my-dhcpservername.
console> system dhcp dhcp-options binding show dhcpname my-dhcpservername
Options Configured from GUI
---------------------------
xxx-removed-xxx
Options Configured from CLI
---------------------------
TFTP_Server_Name(66) "172.16.1.2/bblefi-x64/shim_x64.efi"
In a tcp dump, it all looks fine so far - the offer includes the correct IP:
Option: (54) DHCP Server Identifier (192.168.32.1)
Length: 4
DHCP Server Identifier: 192.168.32.1
Option: (51) IP Address Lease Time
Option: (1) Subnet Mask (255.255.255.128)
Option: (3) Router
Option: (6) Domain Name Server
Option: (15) Domain Name
Option: (66) TFTP Server Name
Length: 13
TFTP Server Name: 172.16.1.2
Option: (67) Bootfile name
Length: 23
Bootfile name: bblefi-x64\shim_x64.efi
Option: (255) End
Option End: 255
But then the Client uses the Firewall IP again instead of the real Server IP in TFTP communication:
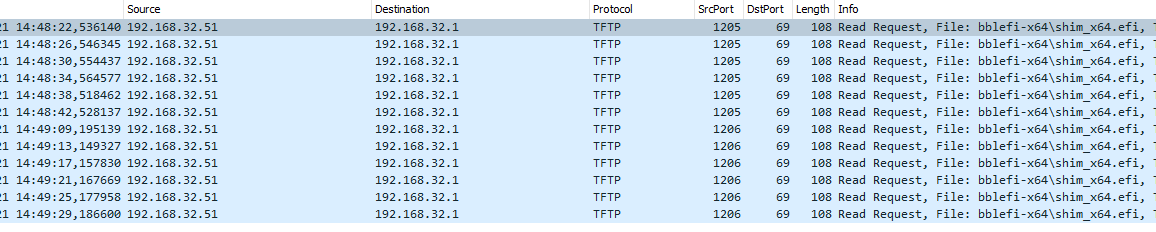
Any idea?
This thread was automatically locked due to age.