We're having a strange situation again after it happened last week already on our SFOS 19.0.1 XG430:
Some users browse to a website that has no exceptions on our firewall for decryption.
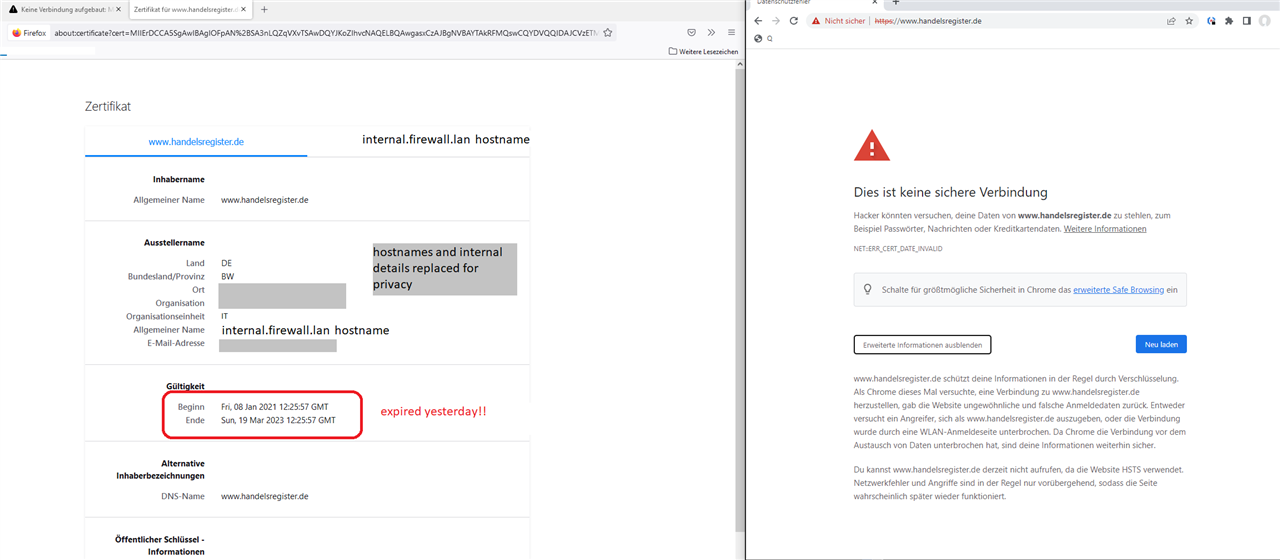
The browser (firefox or chrome) show an error that the site is not secure. If you check for the details, you can see, the website has been re-encrypted by the firewall root ca - so far so normal - but the certificate shown has expired yesterday. That is why the page is blocked. This situation is only for some users that are behind a SD-RED60 from our current debugging.
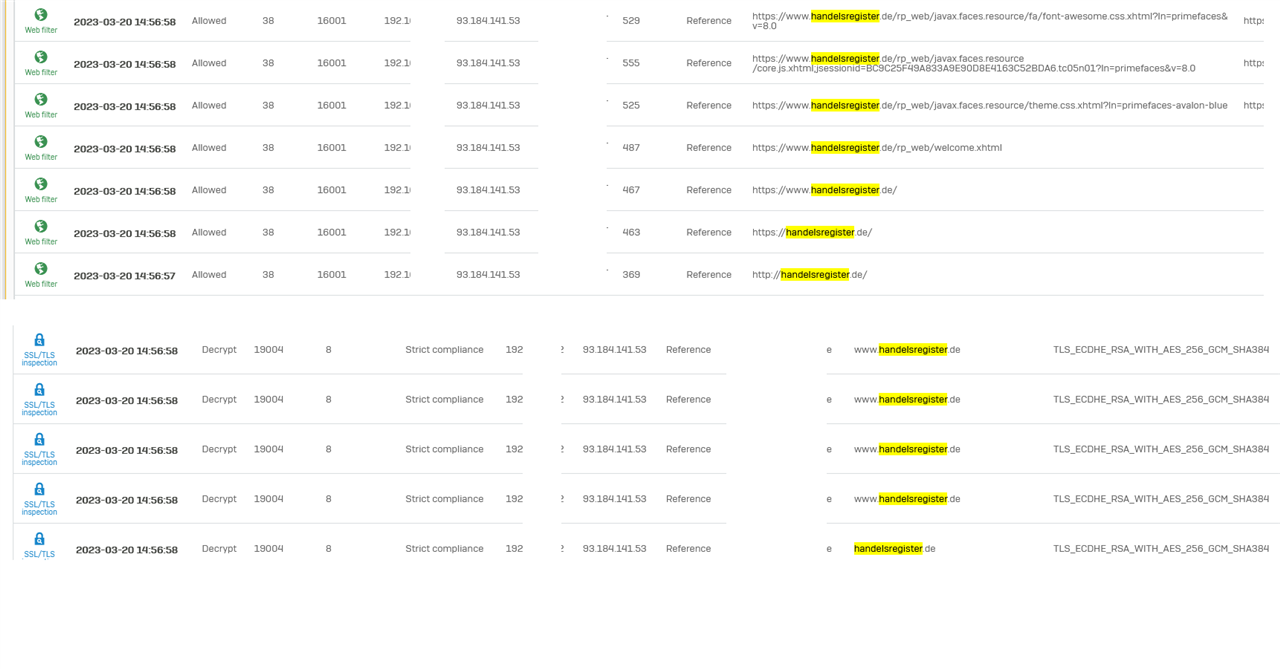
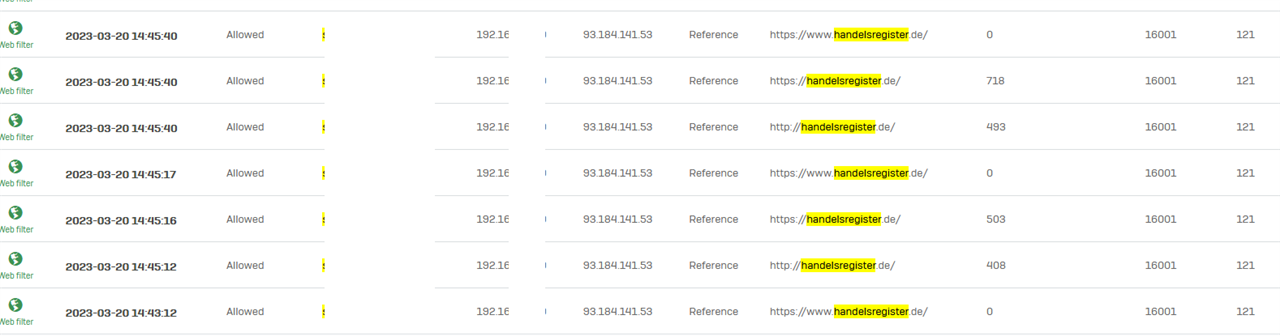
I can see the users that hit the issue with some website do not appear in the TLS logs, insteady their requests only appear in the Webfilter Logs.
Those users that can access the websites, show in both: Webfilter and TLS logs.
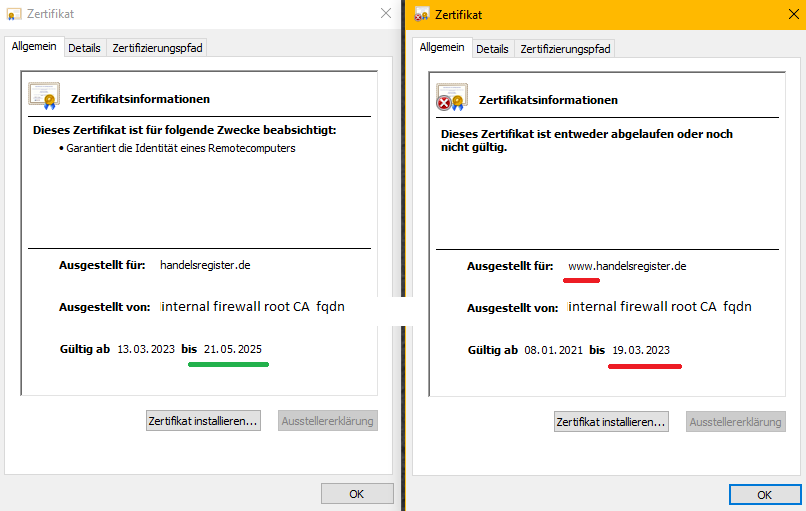
Here one example for the website handelsregister.de
Here it works:
Decrypted by Sophos EP on last instance. Cert valid until may 10th.
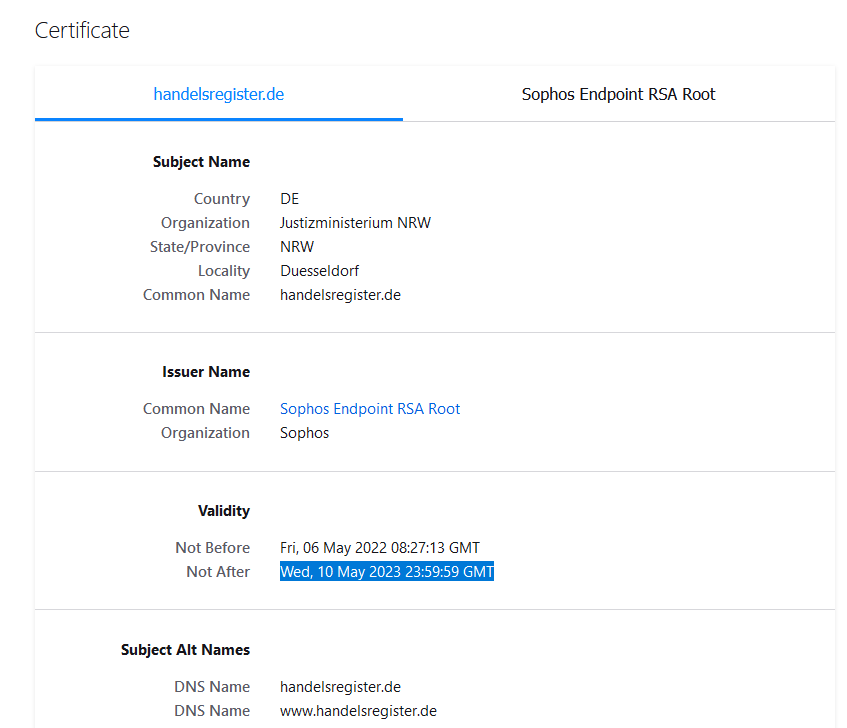
Lets check the real certificate Chain:
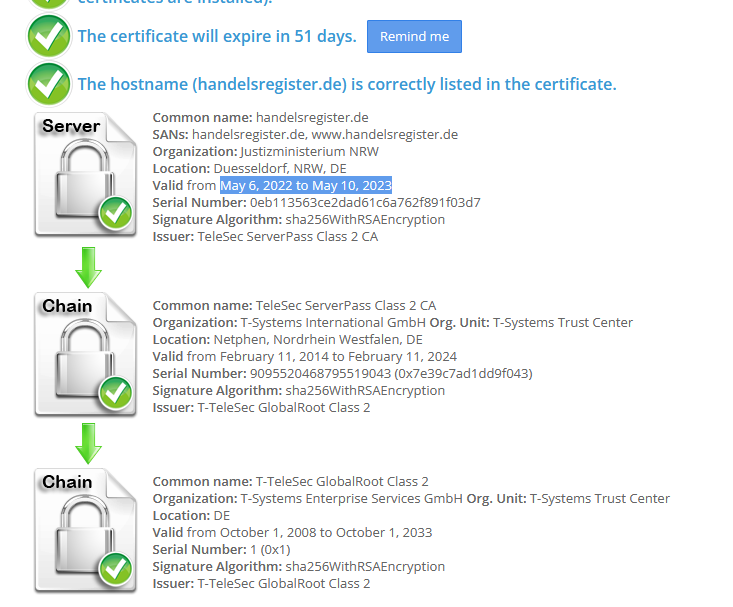
And this is it on the endpoints behind SD-RED60:
This thread was automatically locked due to age.