Hello
I have searched and can see others have this issue, however none of the solutions have worked for me so far.
I have followed the steps at https://docs.sophos.com/nsg/sophos-firewall/19.5/Help/en-us/webhelp/onlinehelp/AdministratorHelp/RulesAndPolicies/NATRules/RulesPoliciesCreateDNATAndFirewallRulesForInternalServers/index.html#specify-the-nat-rule-settings to create the following policies, with the intention of allowing WAN -> LAN traffic the specified ports:
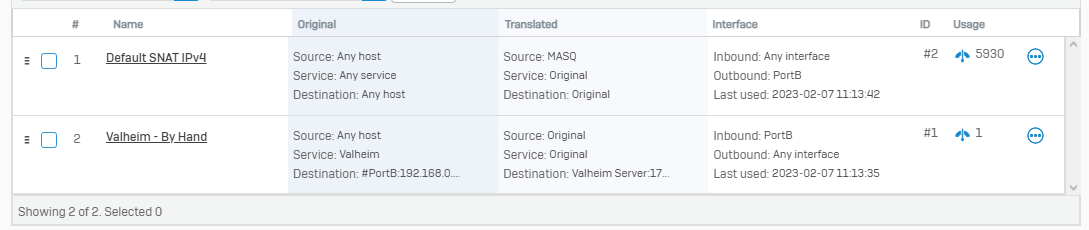
NAT Rule: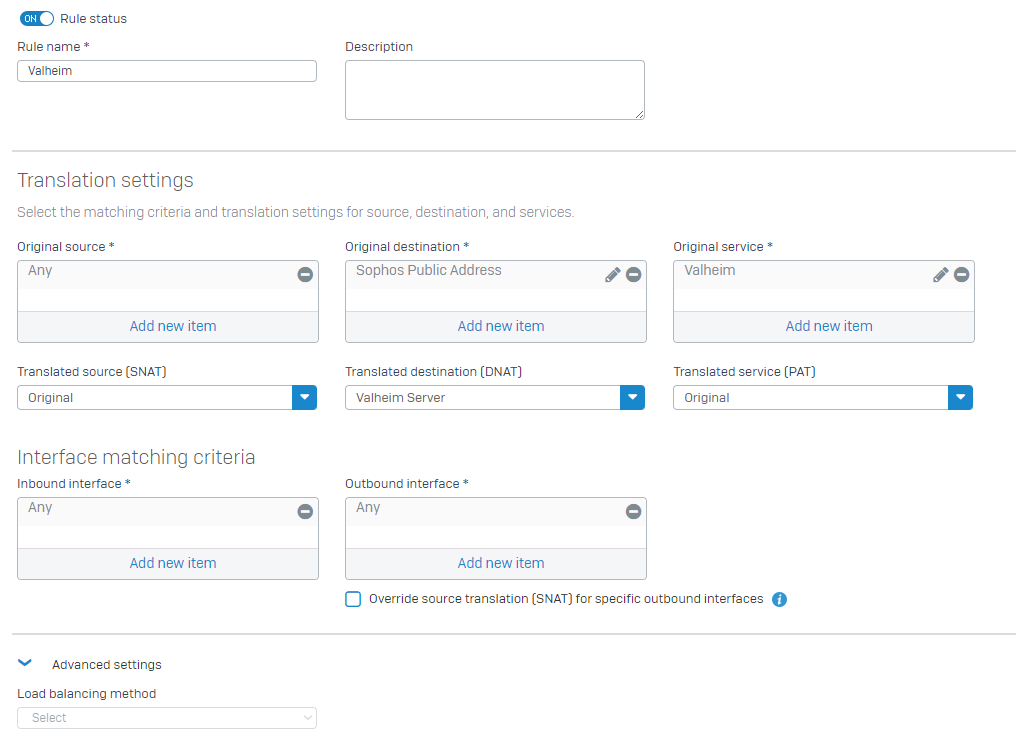
Sophos Public Address is an IP 192.168.0.90
Valheim Server is an IP 172.16.50.110
Firewall Rule:
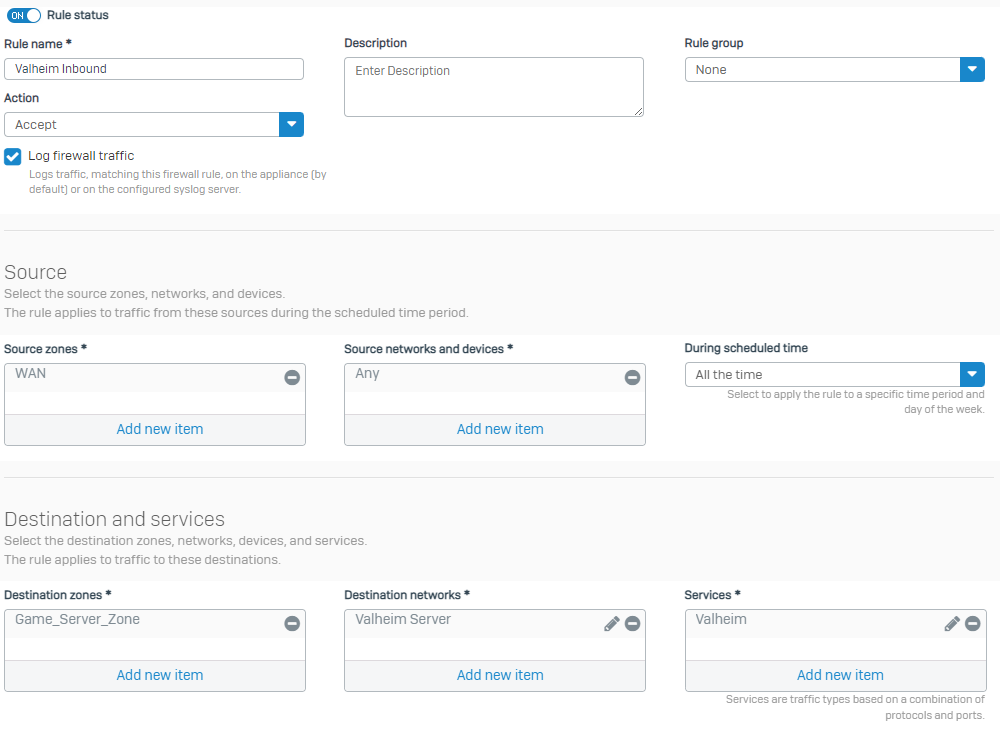
The service 'Valheim' is defined as: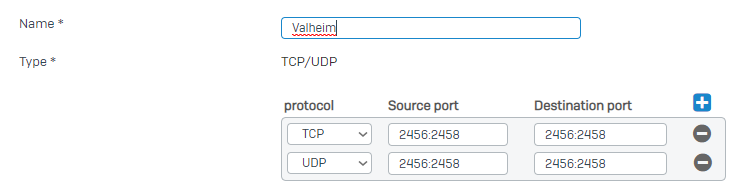
The packet captures I have been getting are as follows: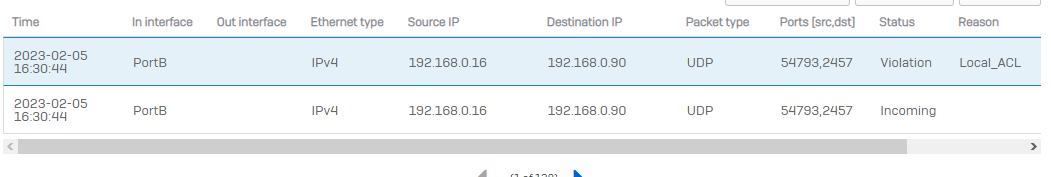
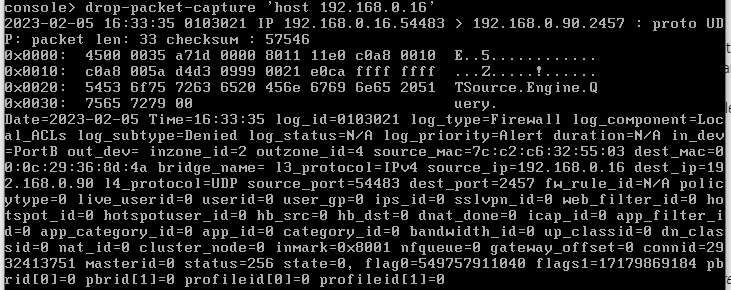
(apologies for drop-packet as an image and not plain text)
Any help would be greatly appreciated
This thread was automatically locked due to age.