Hello,
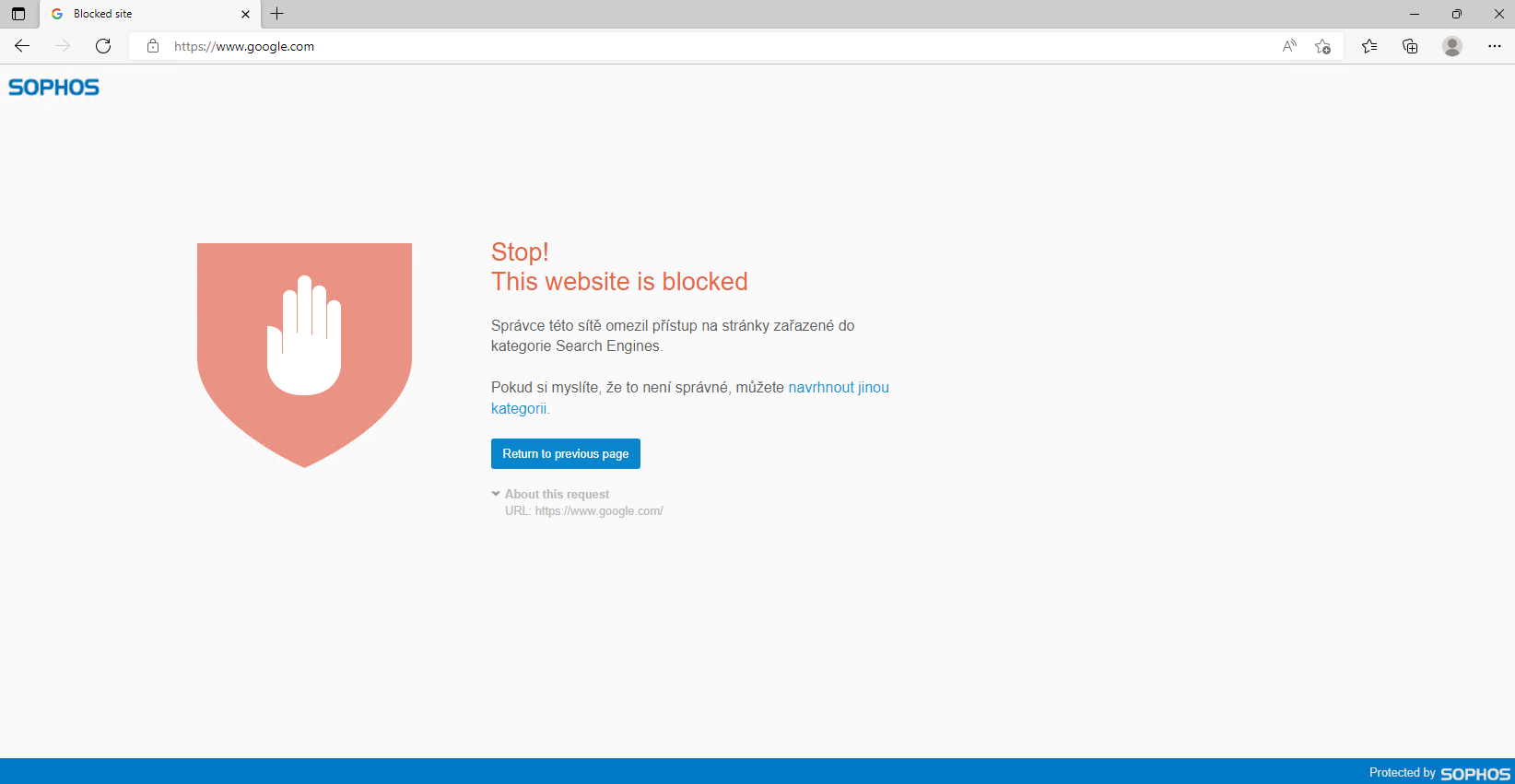
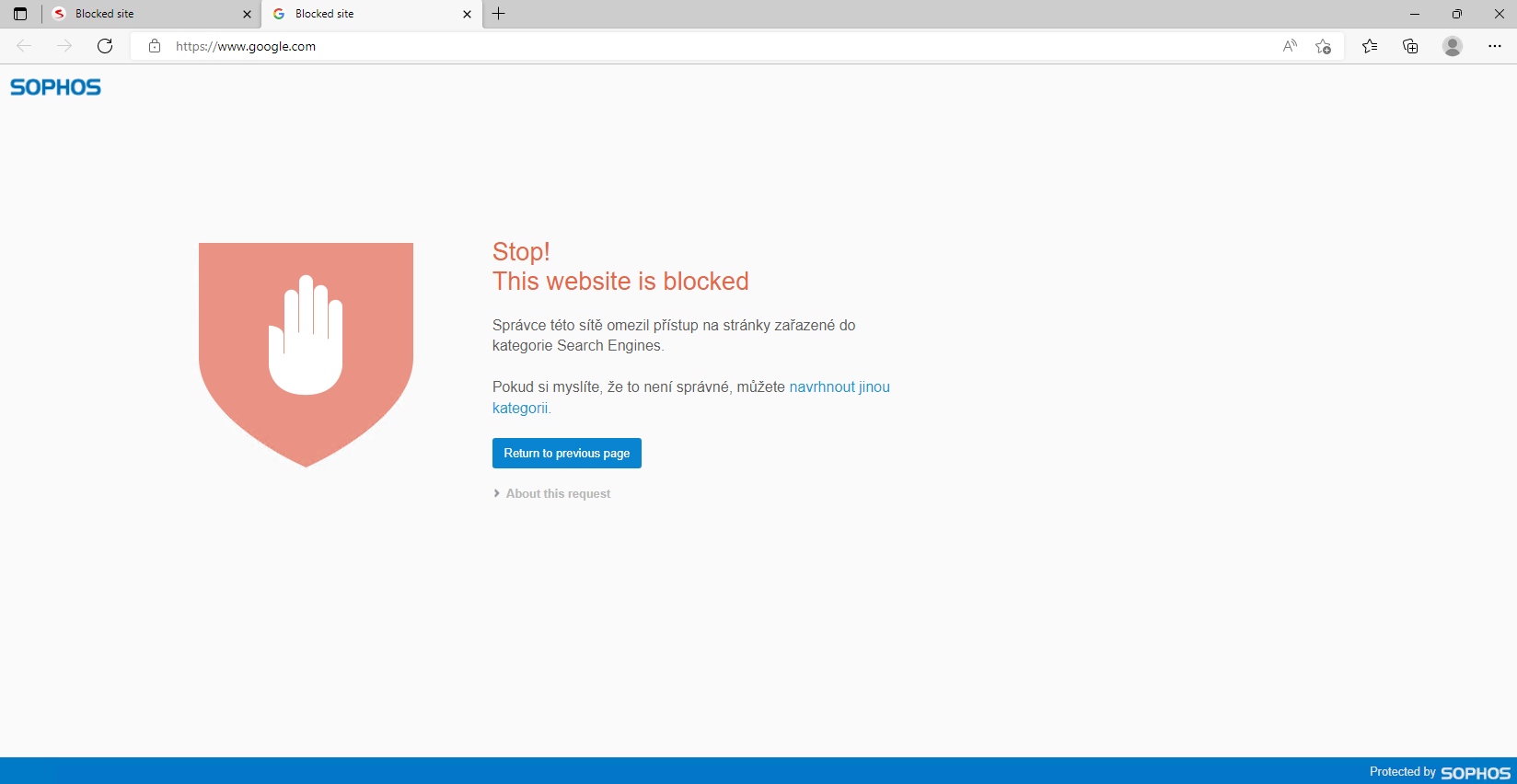
I'm using Sophos XG2300 SFOS 19.0.1 MR-1-Build365 and I would like to ask why do I get blocked when I'm trying to browse the internet with configured proxy, match known users turned on and web filtering set to none. Through testing and searching I managed to make a workaround where I had to make a new firewall rule for proxy only.
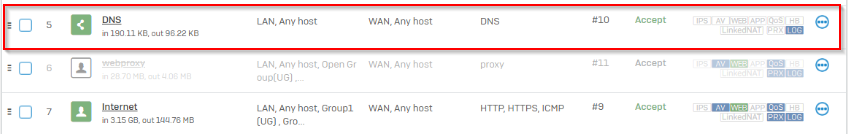
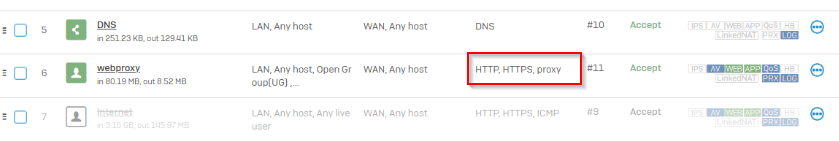
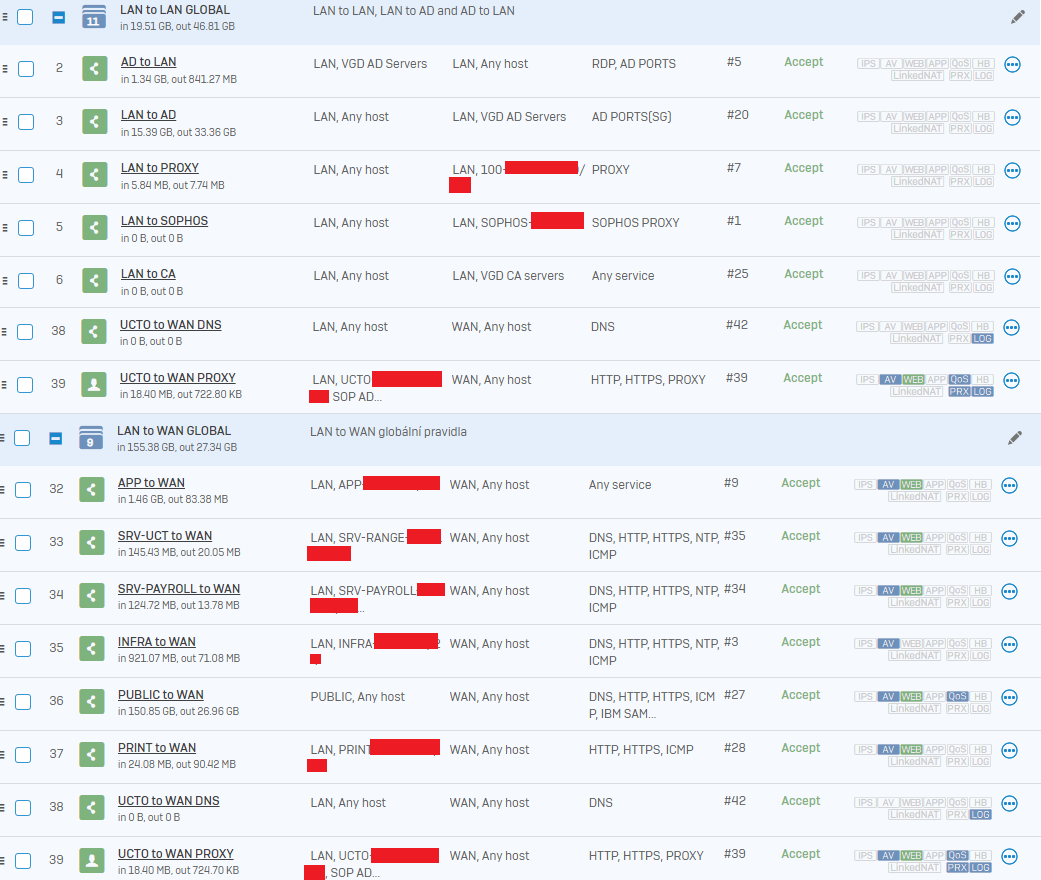
- first firewall rule (LAN to WAN) has these settings: Services HTTP/S, ICMP; Match known users and Web proxy instead of DPI engine
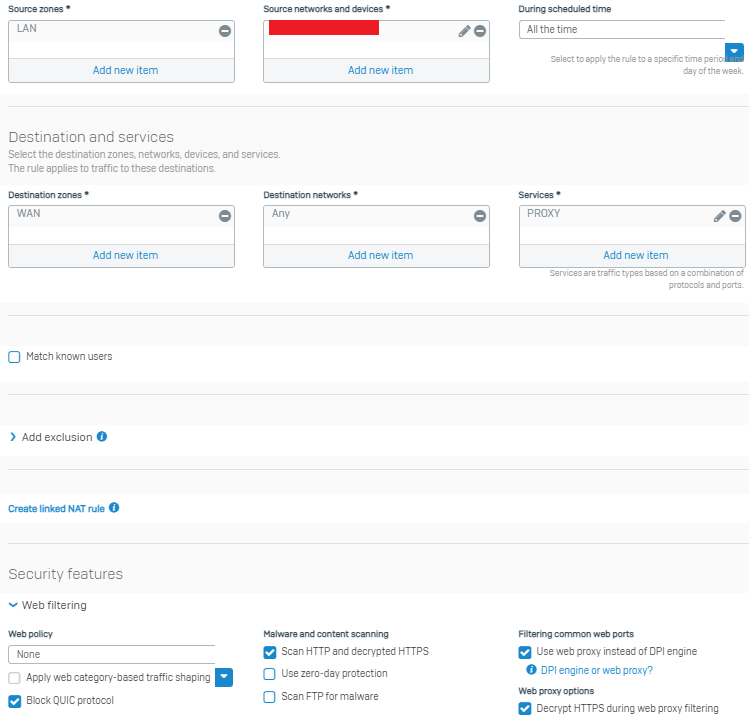
- second firewall rule (LAN to WAN PROXY) has these settings: Services PROXY(TCP 3128); Web proxy instead of DPI engine
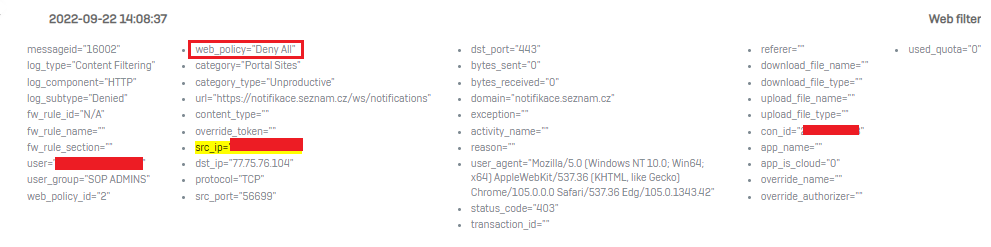
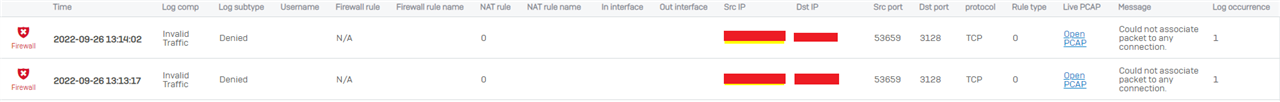
If I enable match known users on the second firewall rule I get blocked from all websites even if I don't have web filtering on. I don't quite understand why that is happening so I would like to ask anyone who could tell me the reason why this is happening.
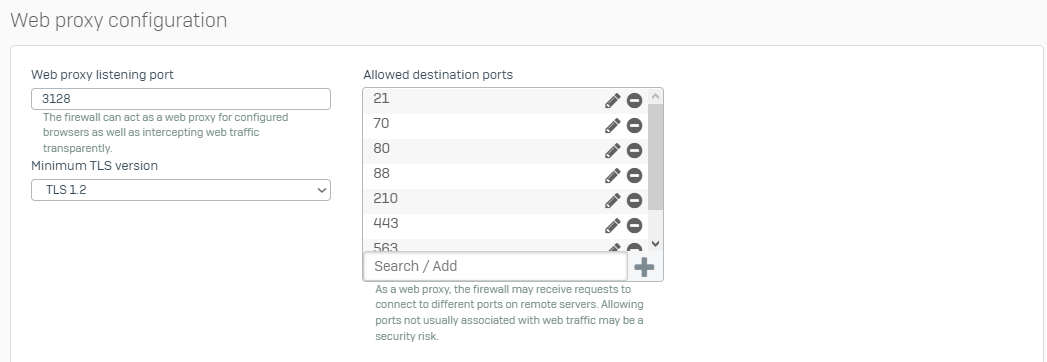
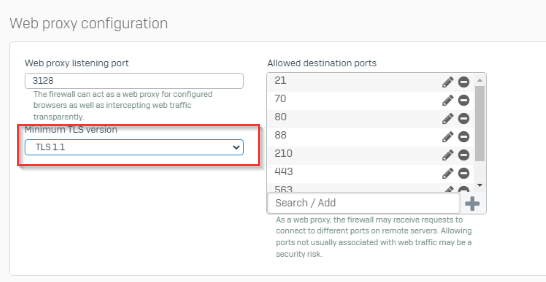
Another problem with match known users is that the Web proxy transparently handles traffic only on TCP ports 80 and 443. If I have match known users on and proxy turned off for the browser I can't seem to get on any website, I get stuck on loading and then the connection times out. If I have match known users off and proxy turned off for the browser I manage to get on websites
LAN to WAN
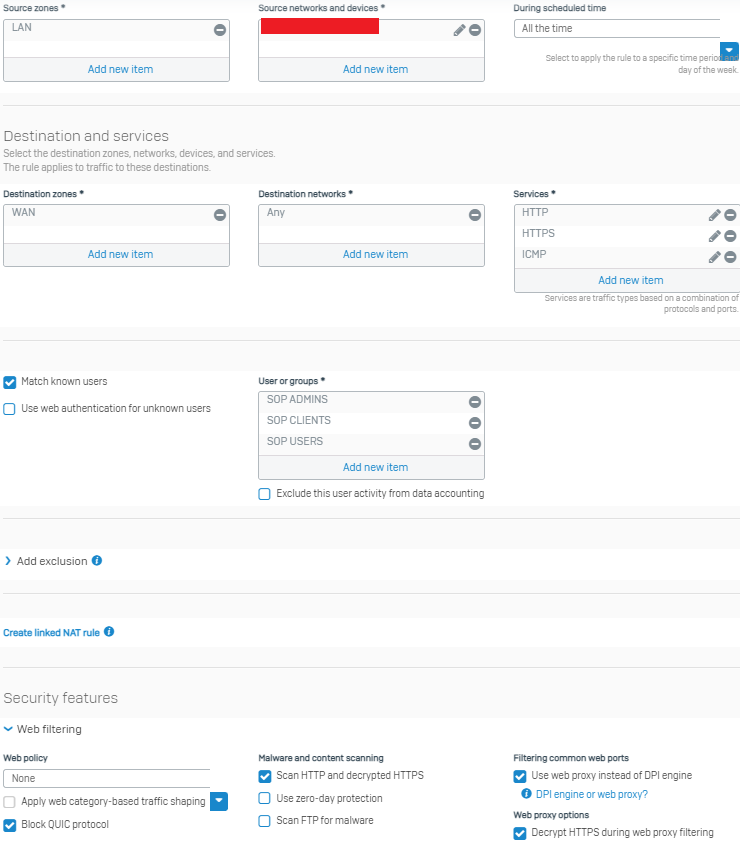
LAN to WAN PROXY
This thread was automatically locked due to age.