Hi,
I have problem with pppoe connection which I don't know how to solve
MTU 1492
MSS 1452
no web policy
no ips
no DoS
tried changing port (on port 2 connection was terrible)
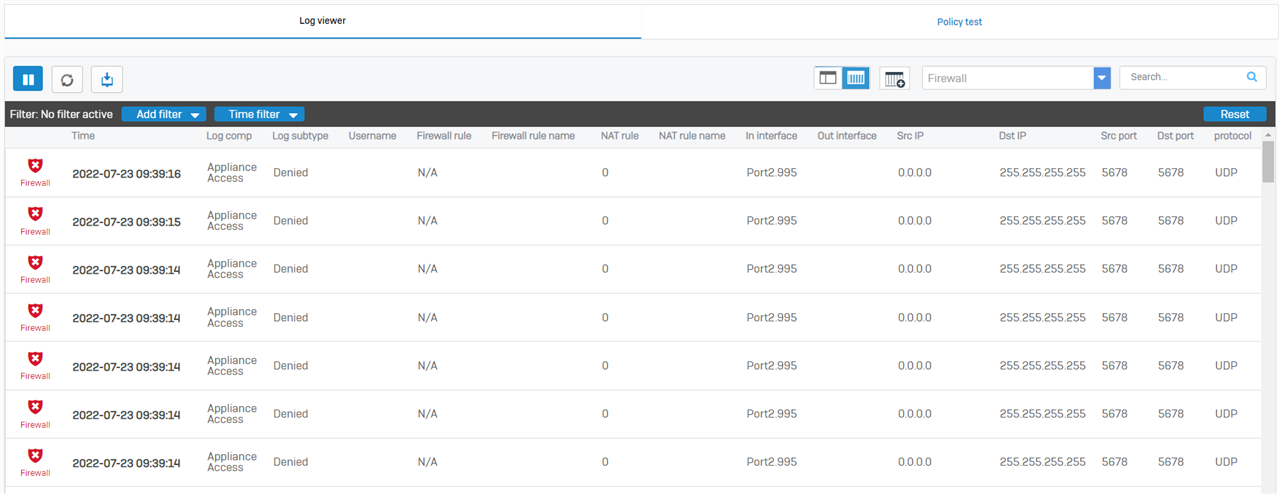
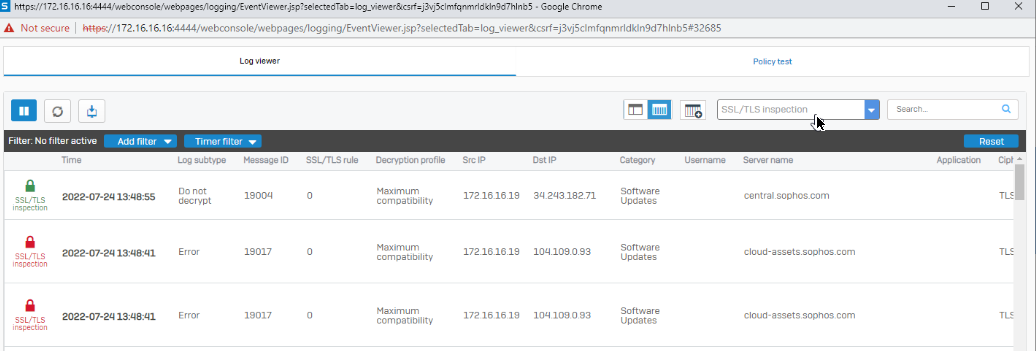
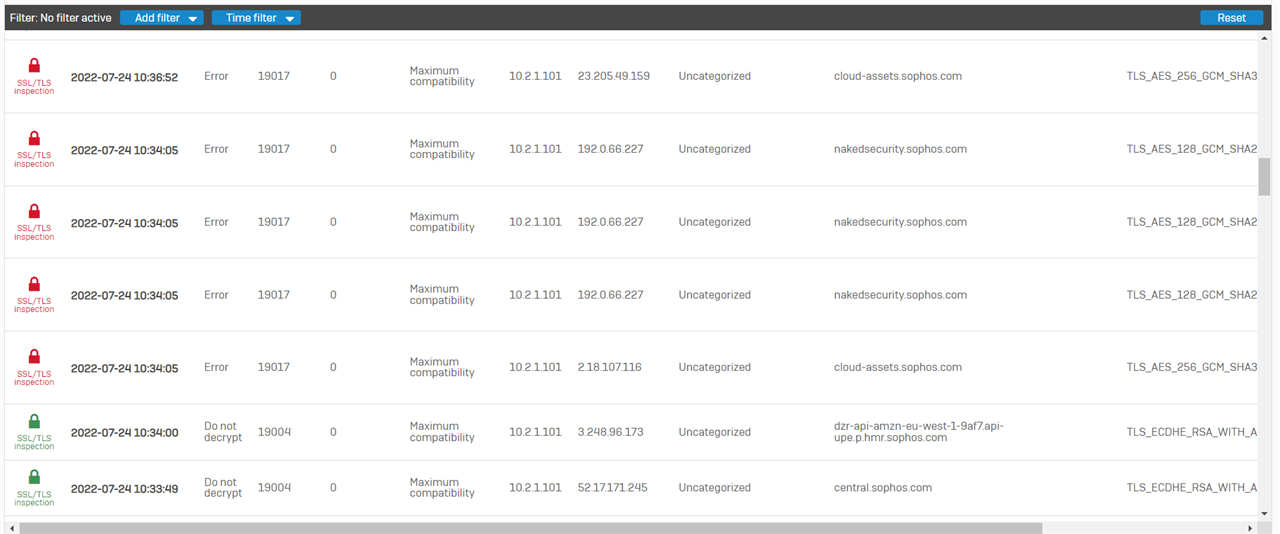
Problem is that pages are loading slow, after I press "enter" on url nothing happens for 10 seconds and then it start to looking for page. I checked on multiple pc's, diferent browsers and directly plugged to lan port (without other clients). Internet speed is about 200 mbps faster on ISP equipment. Behind XG I get around 350 download and 200 upload.
Maybe this has to do something with dns but I don't know how to troubleshoot.
Thanks.
Carlo
This thread was automatically locked due to age.