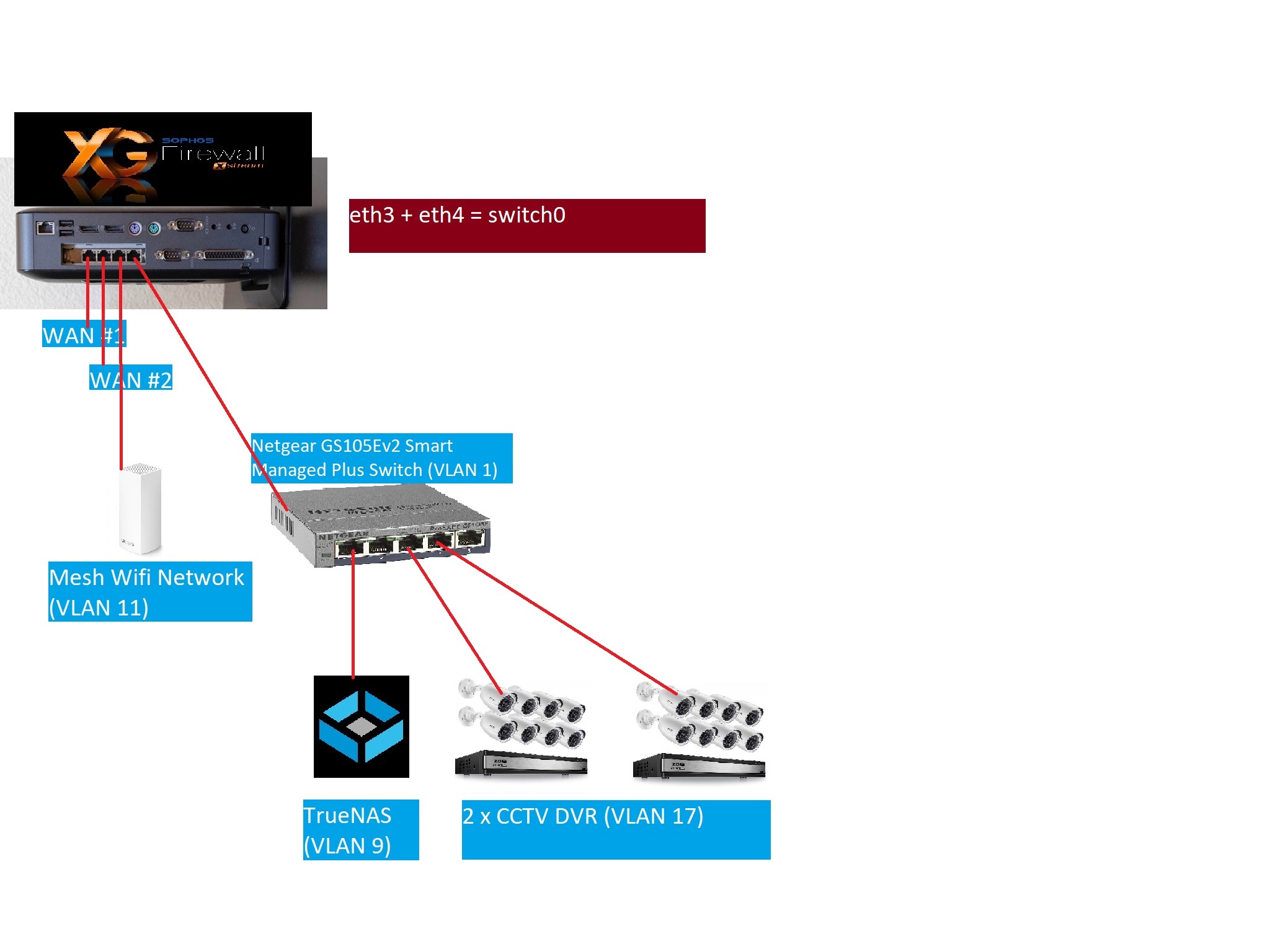
After having messed around with the webgui of Sophos XG (Home) on the HP T620 Plus & Intel I340-T4 NIC for a while, I have came to the conclusion that Sophos XG's VLAN feature set lacks the ability to assign PVID on the ports of the I340-T4. Having looked through some network maps of the troubleshooting posts here on the Sophos XG Forum, I found that most if not all of the working layouts consist of at least 1 802.1Q-compatible managed switch being connected to a VLAN interface of the XG via an RJ45 port. Only then that endpoint devices can be recognised and connected to the XG's network. Some example layouts can look like this :
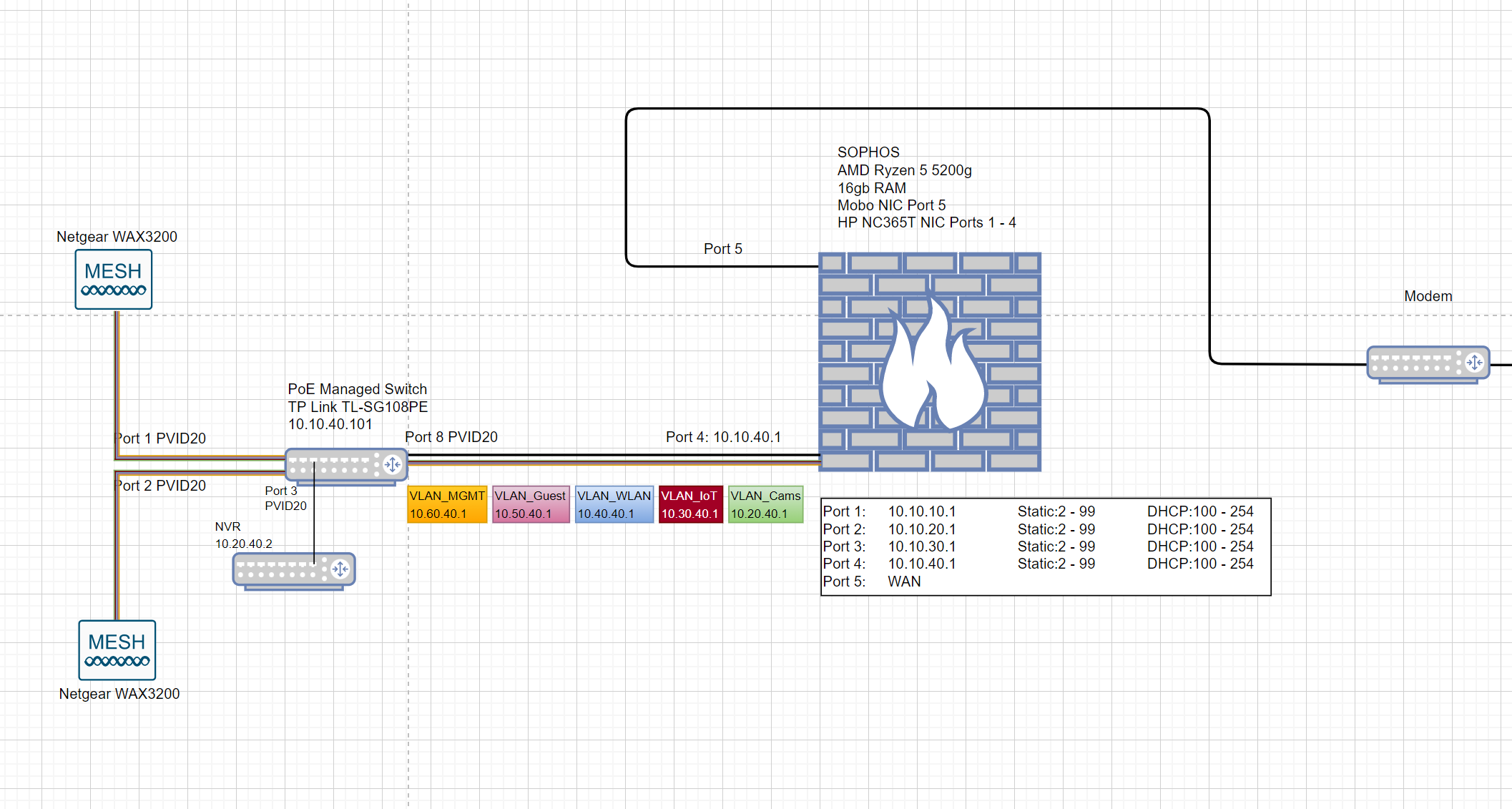
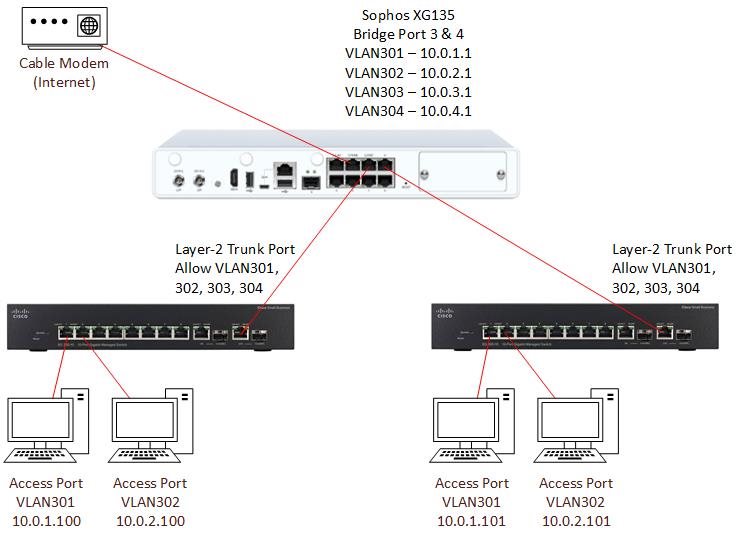
Hence the conclusion. If this is true, then I believe that this is an Achilles Heel of the XG when compared to other router solutions, e.g. Ubiquiti's EdgeOS, which allows assigning PVID on every one of the router's LAN port:
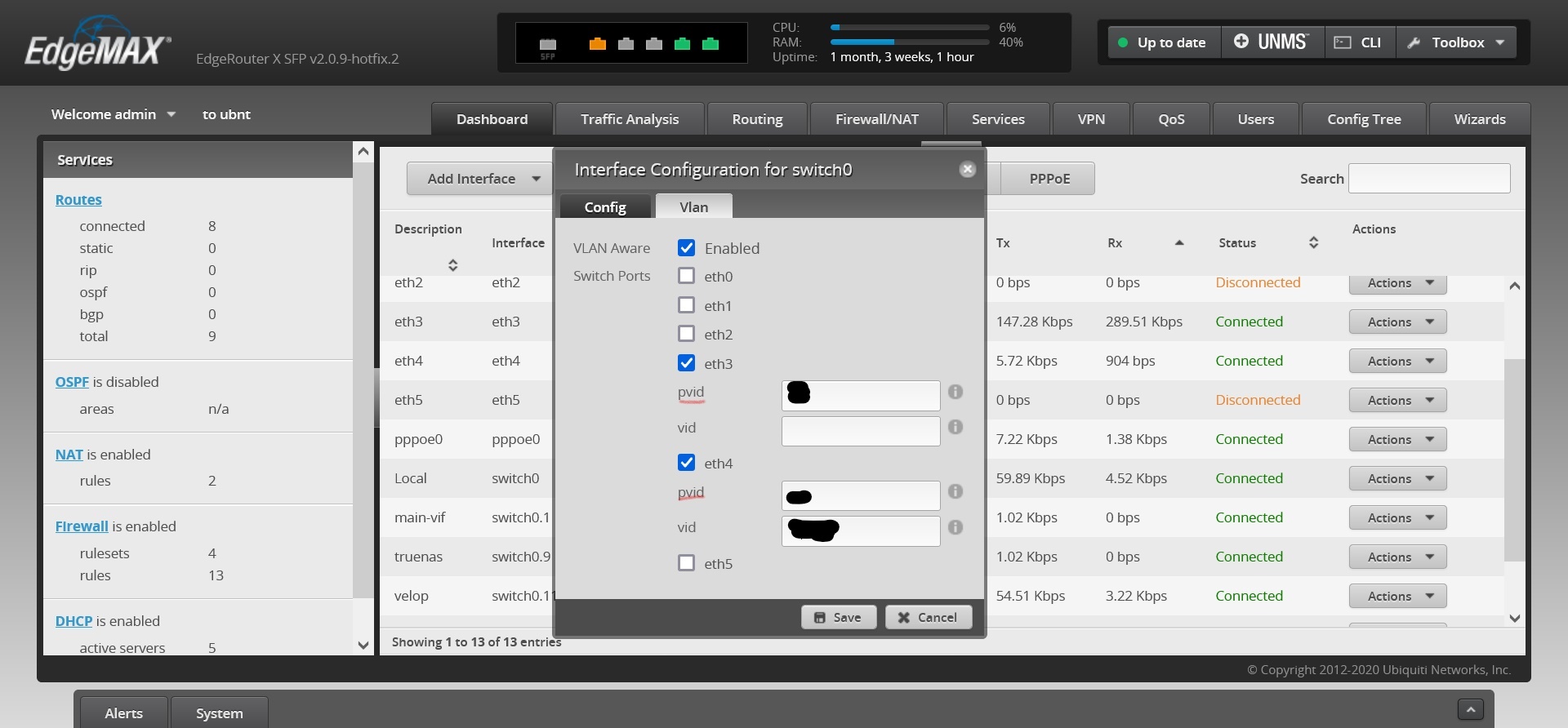
I don't believe that adding the PVID functionality into the Sophos XG will cannibalise the sale of Sophos' managed switches, as Ubiquiti sell both their routers & managed switches very well.
Article on PVID: docs.oracle.com/.../index.html
Does Sophos plan to add this PVID functionality to its XG line of product later on or can I raise a feature request ?
This thread was automatically locked due to age.