Hello community,
I'm stumbling over the following problem:
IPSec VPN ist configured to be used as standard-gateway when clients are connected with Sophos Connect Client.
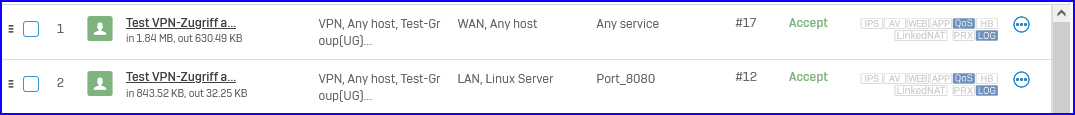
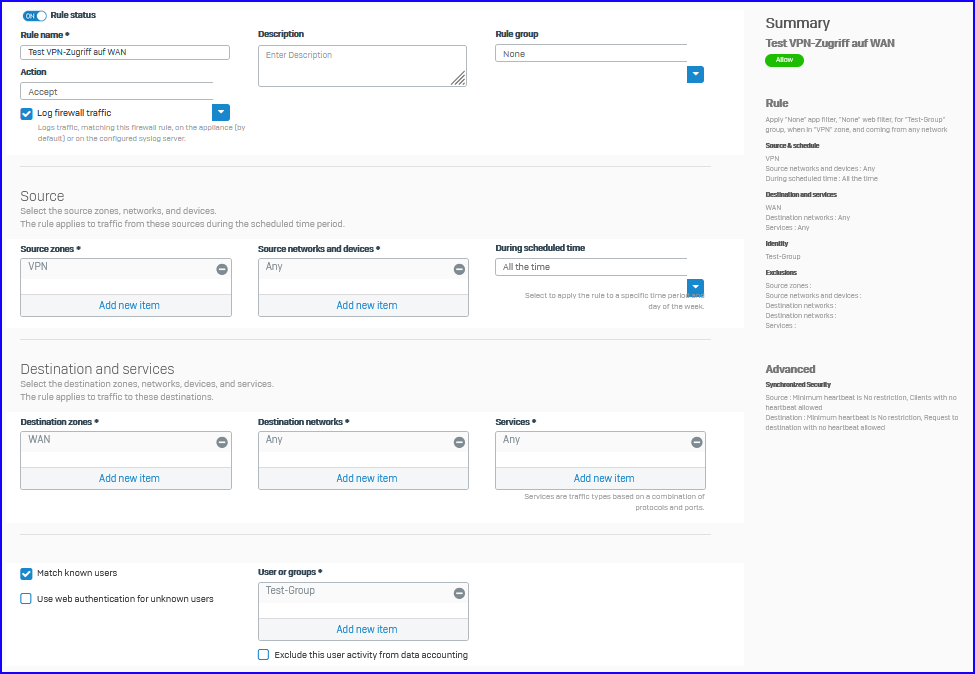
Firewall-rule is created with target zones LAN and WAN and works fine.
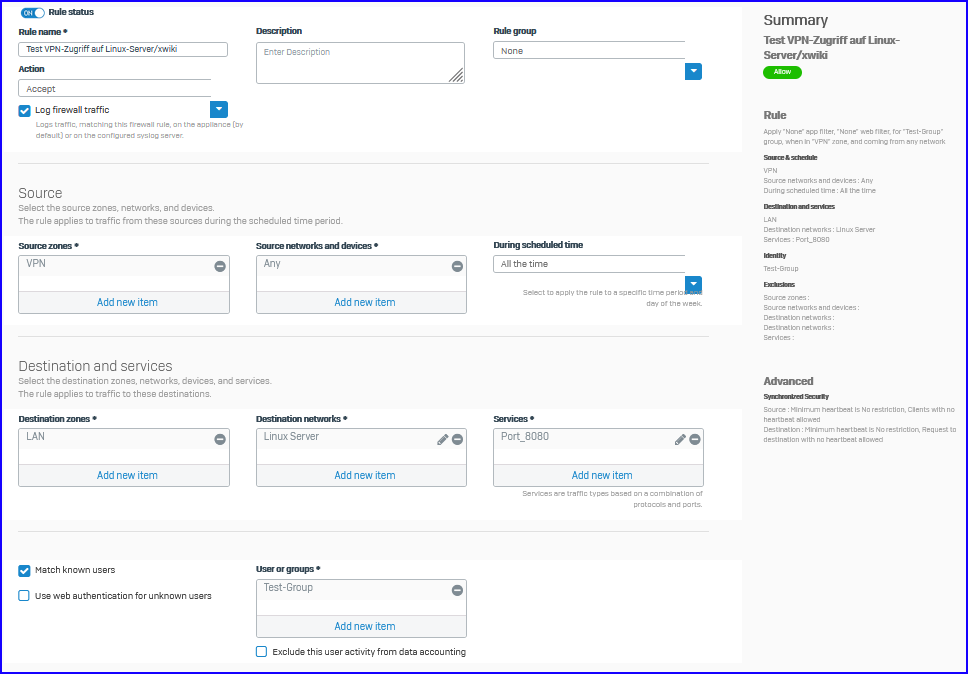
Now there is a user who should only have access to a single server in LAN via a special port.
If I add the server to the accepted destination networks, the WAN access is not possible anymore.
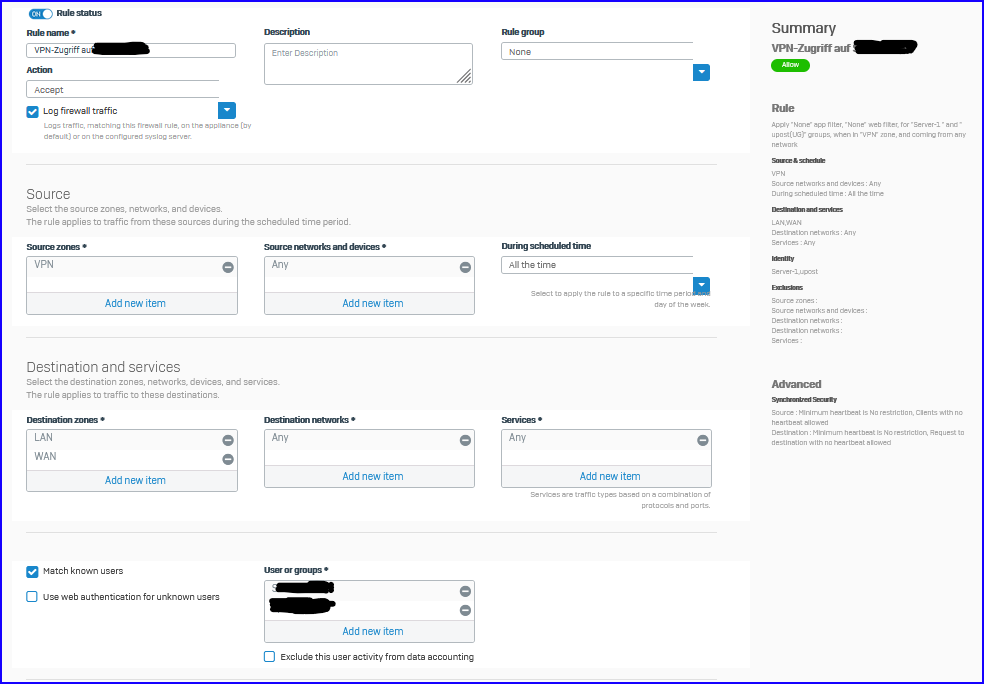
What is best practice to realize connection through VPN to a specific internal server at specific port AND WAN?
This thread was automatically locked due to age.