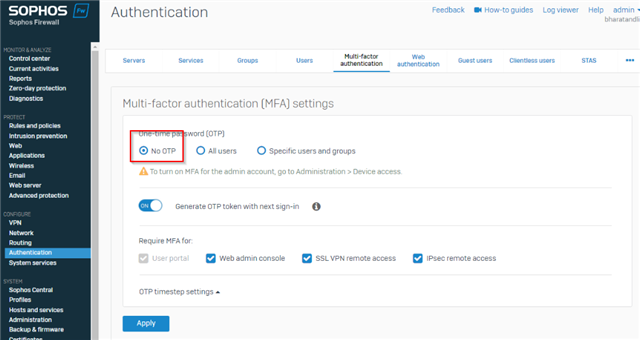
Hi,
We have enabled MFA for our SSL VPN users, however that has meant that it has been enabled for the Captive Portal as well. We really do not want to have users authenticate to the captive portal with MFA, in fact we would really prefer an SSO solution since we get many tickets generated with users struggling to login to the Captive portal when we reboot the firewall after upgrades.
We have implemented STAS and everything seems to be working. All tests when we query workstations are successful, we see live users populate etc. However users are still being forwarded to captive portal. We opened a ticket but the tech wasn't sure if STAS works with MFA.
Any help would be greatly appreciated.
This thread was automatically locked due to age.