Hey all, this is my first post
I think i am missing something and need a little guidance on how to enable access to the sophos gui on the lan side from my main PC within my current setup.
The setup (see pics)
Router -> Sophos XG -> Core Switch -> VLANS (APs/Comps/Etc)
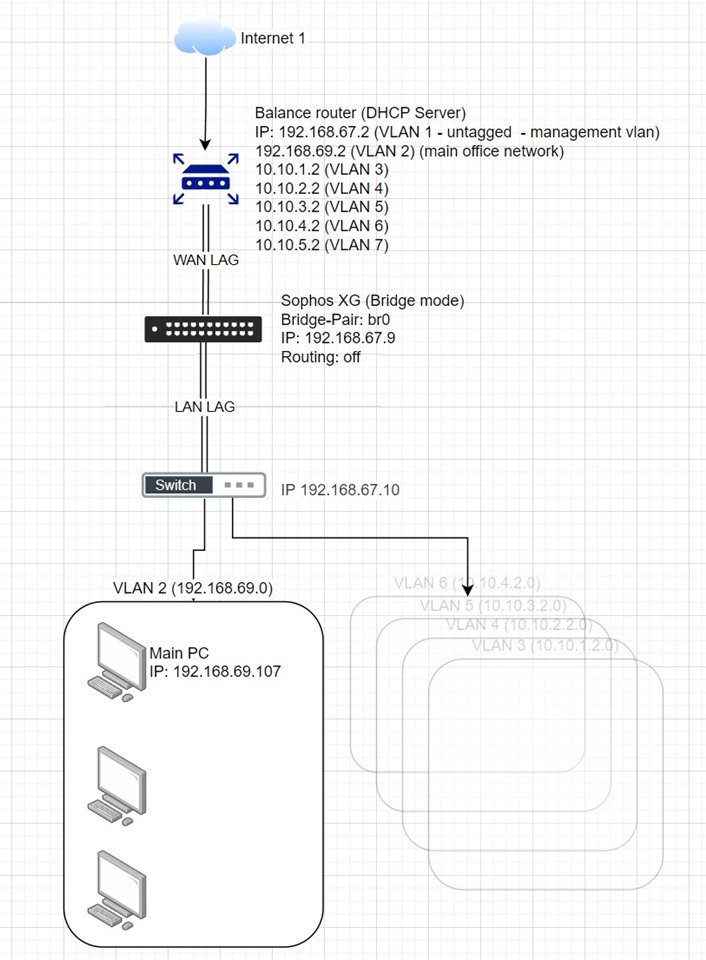
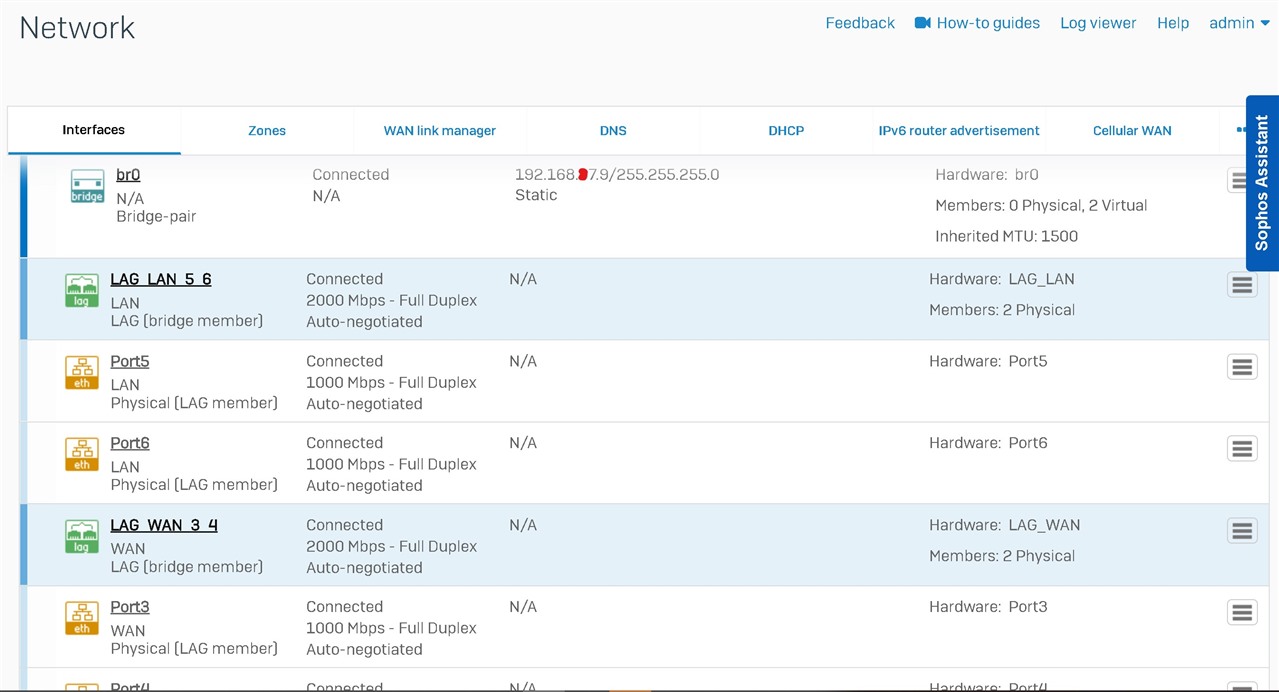
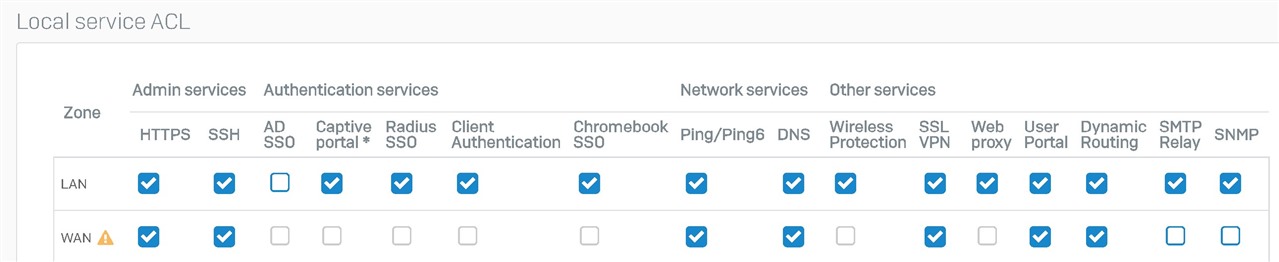
I've setup rules to allow ping/DHCP etc through all connections and i have setup rules to allow Main PC (192.168.69.107) access to 192.168.67.9 on port 4444.
I can ping any gateway on the Router (192.168.67.2 and 192.168.69.2) from the main PC
IF i ping the Sophos 192.168.67.9 (LAN) i get no response, but if i ping it from the WAN side (via routers ping tool) i get a response. So the IP is accessible only from the WAN side.
I can see in the logs, that the incoming request is accepted, but the return journey is denied, despite being a rule in place.
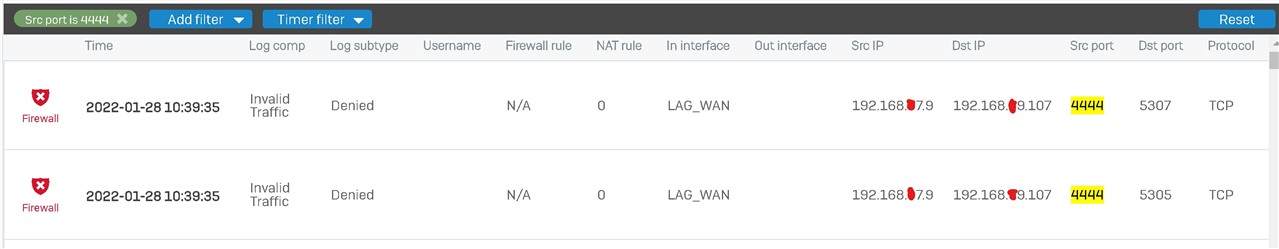
Rule
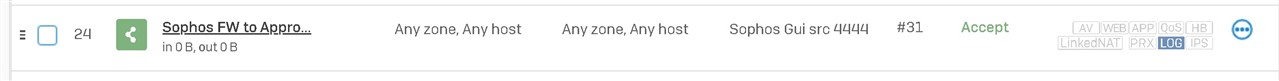
It looks like the Sophos IP 192.168.67.9 is not accessible from the LAN side. I think the networking is setup correctly, i can now access different vlans and everything is talking to each other (provided there is rule in place to allow it)
How do i add another IP on the bridge pair or expose the Sophos to the LAN side? (preferably on the 192.168.67.0 vlan)
I've tried all sorts and it keeps resulting in failure, any ideas would be most welcomed
Thanks for your time
This thread was automatically locked due to age.


