I have just experienced the most bizarre situation. Customer has two backup internet connections on Port 2 and Port 3 that run through another router. Port 4 is the main internet connection. When downloading SSL configuration, the Sophos had local LAN IP addresses of Port 2 and Port 3 higher in the priority list. There was no way to change this and of course SSL VPN is never going to connect to a 192.168.xx.xx address.
There is nowhere anywhere in the Sophos unit to specify what WAN ports to use for SSL VPN and no way to change priority order.
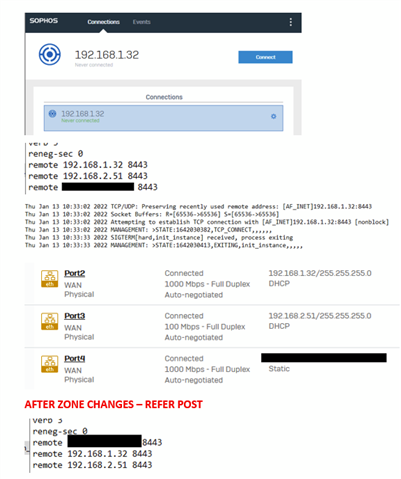
Here is the stupid thing. I created a new zone "WAN2" and moved Port2 and Port3 to "WAN2". I then moved them back to "WAN". Now the WAN IP addresses in the SSL VPN configuration have changed order.
So, it looks like the order of WAN IP addresses in the SSL VPN configuration that a user downloads are the order in which the ports are assigned to the WAN zone. If you want to set the order for SSL VPN connections, set all your ports to some random zone and then assign them back to the WAN zone in the order you want the Sophos SSL VPN to use them.
Dumb - and needs to be fixed, but I'm still waiting for issues from 2012 to be fixed so I won't hold my breathe.
Hopefully this helps someone
This thread was automatically locked due to age.