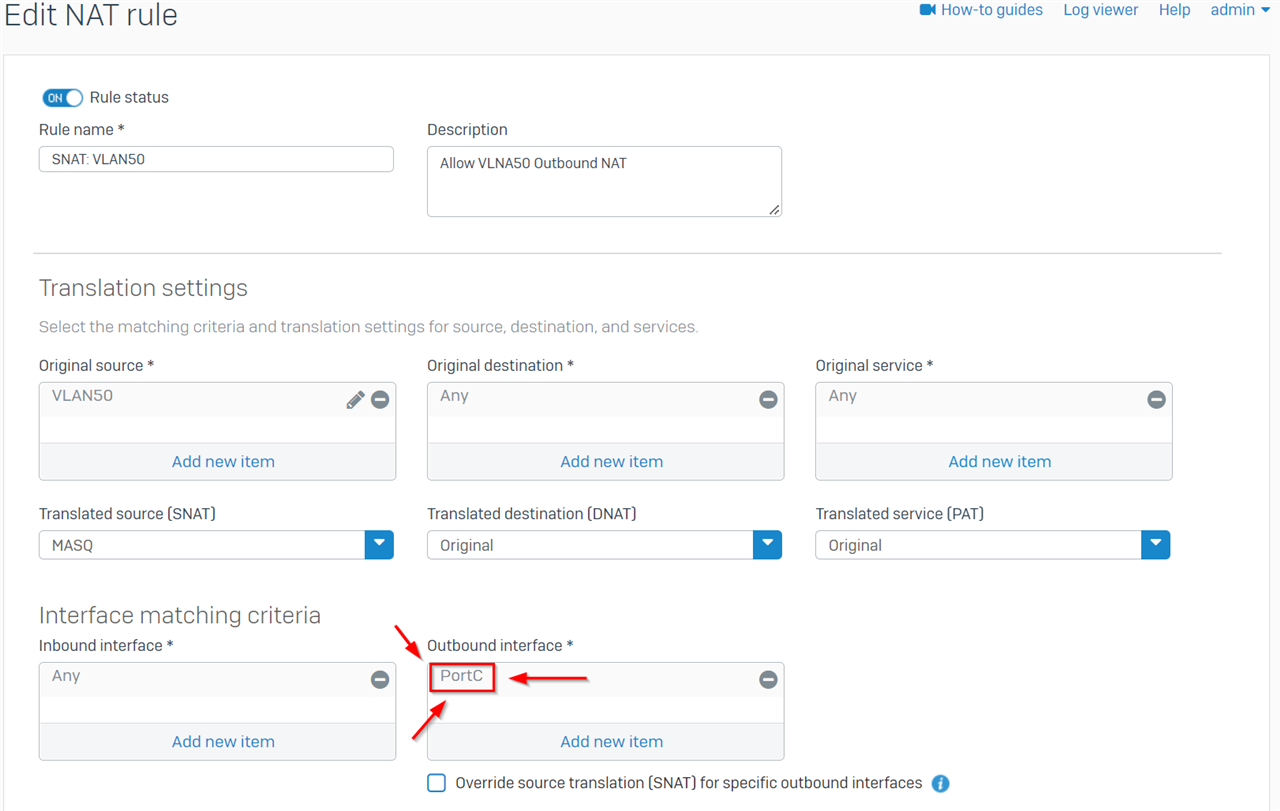
Hi,
I have created a site-to-site IPSec VPN between my XG and Azure.
The tunnel is up, confirmed both sides and I can connect from Azure to local, but not the other way around.
I followed this article to the letter: https://community.sophos.com/sophos-xg-firewall/f/recommended-reads/126356/sophos-xg-firewall-v18-to-azure-vpn-gateway-ipsec-connection.
I have multiple VLANs configured on my XG. I haven't done anything specific for those - not that I know if I need to. The firewall rule encompasses all the VLANs.
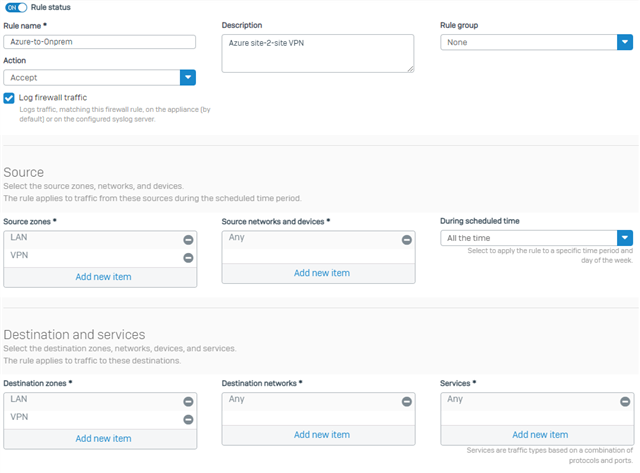
When testing connectivity from local to Azure, I can see the rule is allowed.
I have a gaping hole in my Azure NSG (ANY-ANY), both inbound and outbound.
The Azure endpoint is Ubuntu 20.04 LTS and as far as I know, all firewalls are off:
user@vm01:~$ sudo ufw status verbose Status: inactive
Here is the main VPN config page:
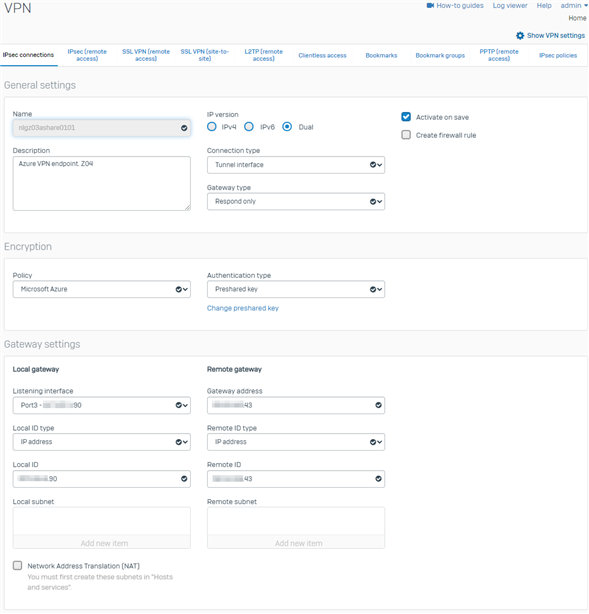
I'm not particularly familiar with Ubuntu, so it may be something on the endpoint, however, I'd like to rule out XG's VPN config.
I read the note about the XG version and I am currently running on SFOS 18.0.4 MR-4. Can't upgrade just yet.
If anyone can think of anything I should try, please shout.
T.I.A
This thread was automatically locked due to age.