Hi all,
I think I am just misunderstanding how this works but maybe you can help me with clarifying. :-)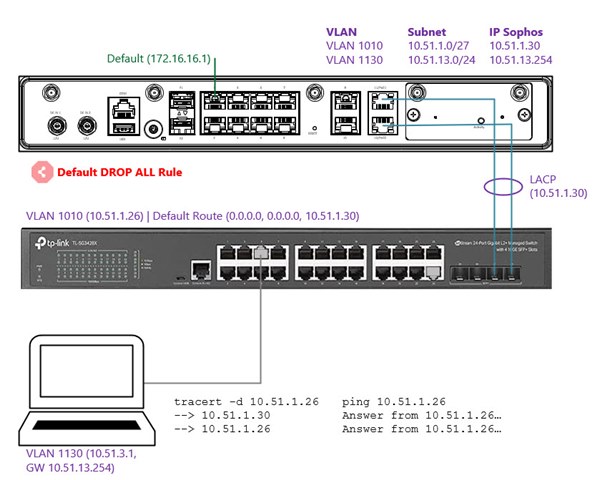
Components:
- Sophos XGS 126
- TP-Link Managed Switch
Configuration:
- Sophos connected to switch via LAG on fibre channel, IP: 10.51.1.30/27 (VLAN 1010)
- Multiple VLAN interfaces added on the LAG interface (all in zone "LAN")
- Switch has 10.51.1.26/27 in same VLAN
- Client is connected to switch in different VLAN (1130) which is routed via the firewall (Sophos should be gateway for all subnets)
Goal:
- Be able to control traffic between different VLANs (i.e. clients should not be allowed to access switches but printers in different subnet).
Issue:
As I understand, the Sophos has a DROP ALL rule which drops all traffic not explicitly allowed by other rules before it. So this means from my understanding that no traffic between VLANs (even on the same zone, LAN in this case) should work in the first place, right?
What I experience: I have configured no firewall rules but I can ping the switch (10.51.1.26) and even access the web interface from my client (10.51.13.1). A tracert shows that the traffic definitively goes through the firewall. So it seems to me as if the DROP ALL rule does not work here...? I also tried creating new zones and moving the firewall interfaces to different zones (still LAN, but a newly created zone in it), but also no effort.
Question:
How can I accomplish the goal to control traffic between different LAN subnets? What are the best practices here?
Thanks in advance for your replies!
Best regards
Ben
This thread was automatically locked due to age.


