There are some sites that I need Ads blocker disabled, or I wouldn't be able to continue. Is it possible to whitelist?
SFVH (SFOS 18.5.1 MR-1-Build326)
This thread was automatically locked due to age.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Hi,Most certainly is. You need to be using decrypt and scan in the proxy. Create your own web policy using the no adverts, then create exception in the web exceptions.
the block policy needs to be in your firewall rule web setting, you will also need ips enabled.
ian
XG115W - v20.0.3 MR-3 - Home
XG on VM 8 - v21 GA
If a post solves your question please use the 'Verify Answer' button.
Thanks for giving me instructions on enabling, installing CA. Currently, I've only installed/ enabled it on 2 devices, for testing, so as not to disrupt web access. Without the CA, I can't do anything, with CA installed, I can surf easily.
I'm trying to create web exceptions for sites. I chose web category instead. I'm not seeing option to bypass ad block though.
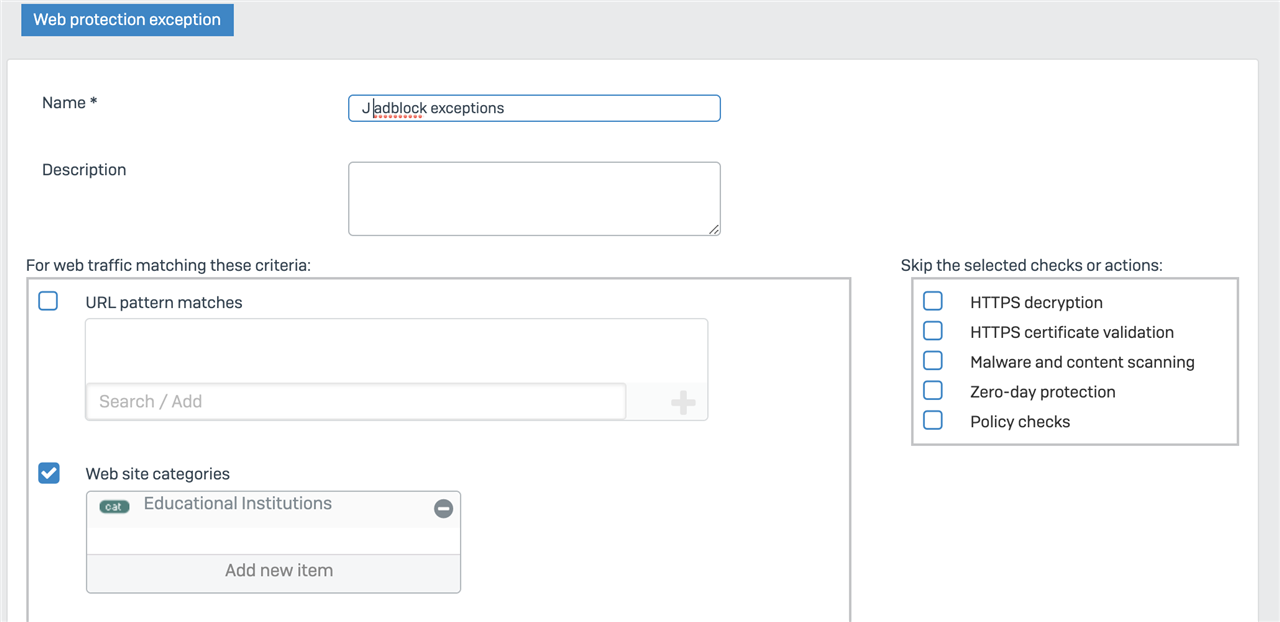
Thanks!
A follow-up question, not sure if still related. SSL/ TLS inspection is related to "Decrypt HTTPS during web proxy filtering?" So should turn it on to start derypting HTTPS? Furthermore, clients without CA installed won't be able to surf if they on the same firewall rule? Can I exclude clients from decrypting https? Do I do this by creating a new ssl/ tls rule, with specific source networks and devices?
Hi,
there is a post from Lucar on the subject, though not sure in what thread. Ssl/tls scans the traffic before passing it for the proxy if the proxy is ticked.
The only way that i am aware of is seperate rule for those clients with out the ca installed. Do you use an AD for authentication otherwise I suggest you look at the various client types in the authentication tab.
ian
XG115W - v20.0.3 MR-3 - Home
XG on VM 8 - v21 GA
If a post solves your question please use the 'Verify Answer' button.
Don't use AD. So far, I've created a separate firewall rule, and given my 2 devices for testing it's own firewall rule, with above recommendations, and SSL/ TLS enabled on the 2 devices. So far, I'm seeing in Firewall page how many % decrypted. Without this, it's always 0. I think I'm doing it correctly now. Thanks!
It is quite simple:
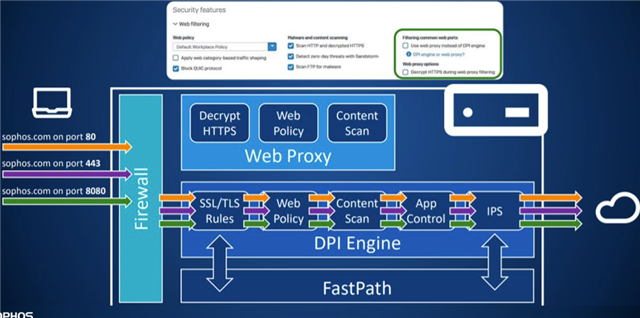
There are two completely different engines in SFOS. Web Proxy and DPI engine. If you tick those both option on the right site in the firewall rule, the traffic will be going over the web proxy (But only 80/443). If you leave it untick and have a TLS/SSL Decryption rule, it will use the DPI Engine. The picture above is by not uing the legacy (old) proxy.
The Web Proxy on the right site of the firewall rule has advantages over the DPI Engine. Means that if you use it, it will be used instead of the DPI Engine.
__________________________________________________________________________________________________________________
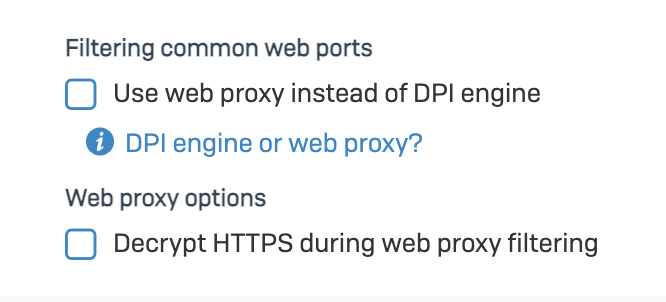
I left it both unchecked, so it uses the DPI Engine, correct? It's more efficient to use DPI Engine?
While SSL/ TLS Inspection enabled, websites function properly, but mobile apps, such as banking apps, cannot sign in. As soon as I turn off SSL/ TLS Inspection, it goes through. Why is this the case?
You have to start to maintain a exception List for certain apps and applications. And you have to roll out the Cert on mobile as well.
HTTPS decryption can and will not work for certain apps, which make sure, this kind of interception is not happening. See: MITM attacks.
__________________________________________________________________________________________________________________