Hello,
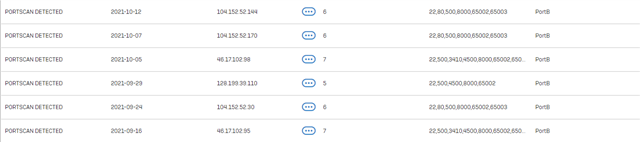
While looking for a way to enable port scan detection on my XG18, all I can find is articles from years ago on how to configure it on the UTM. Are their any recent articles detailing how to be notified of this sort of scanning? You would think it wouldn't be this difficult to set up alerts for this sort of red flag!
This thread was automatically locked due to age.