hi,
can sophos please advise on how to troubleshoot this kind of errors ?
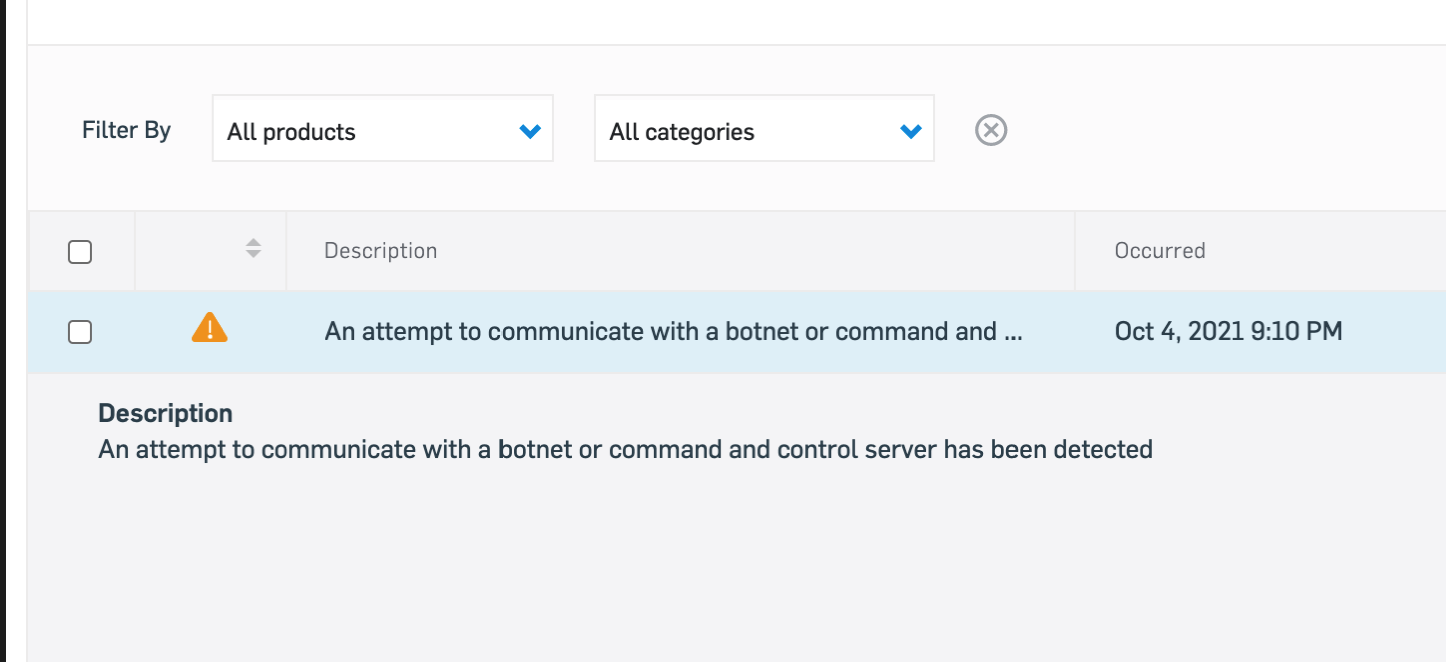
this alert comes to administrators/clients and looks severe
when you click show more info in central there is no more info
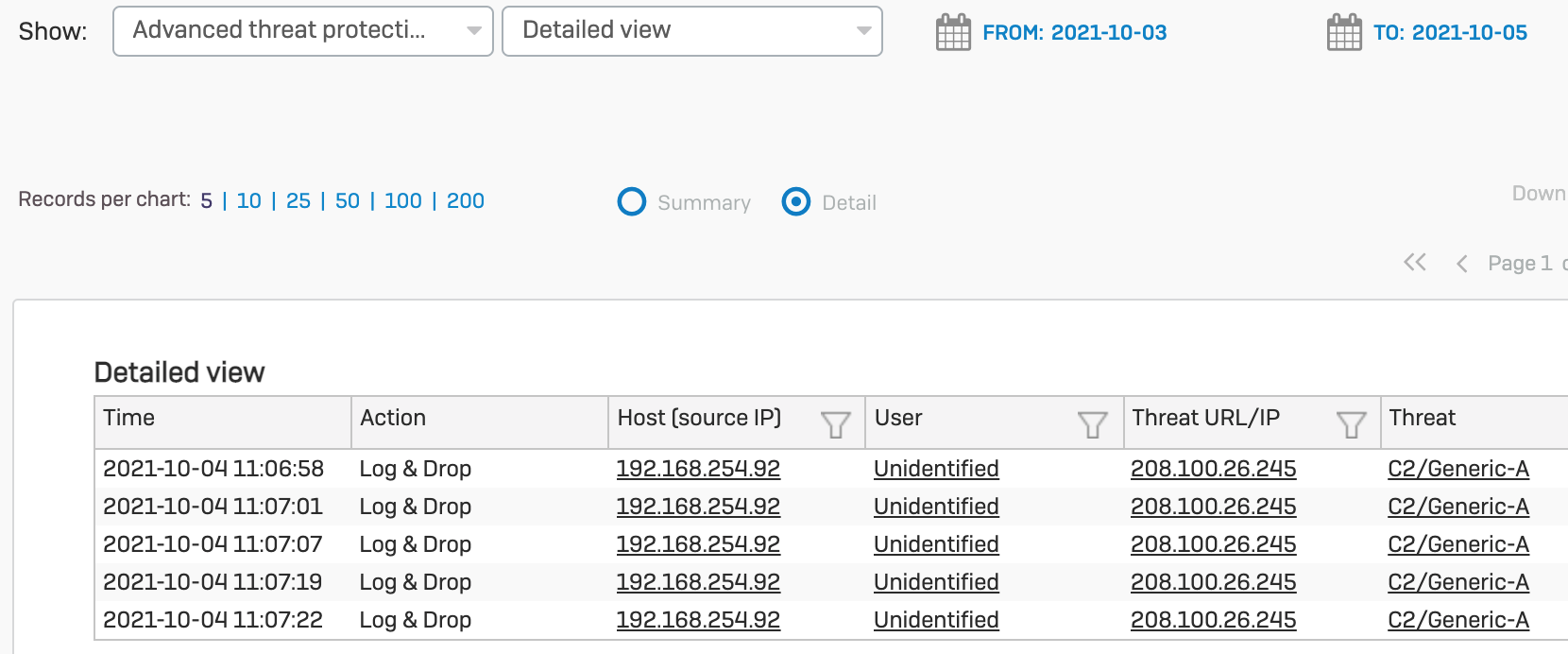
when you go in the XG or XGS in advanced threat protection, most of the times there is no mention of a botnet and in most cases the threat ip is 8.8.8.8
please advise on how we troubleshoot this kind of error.
This thread was automatically locked due to age.