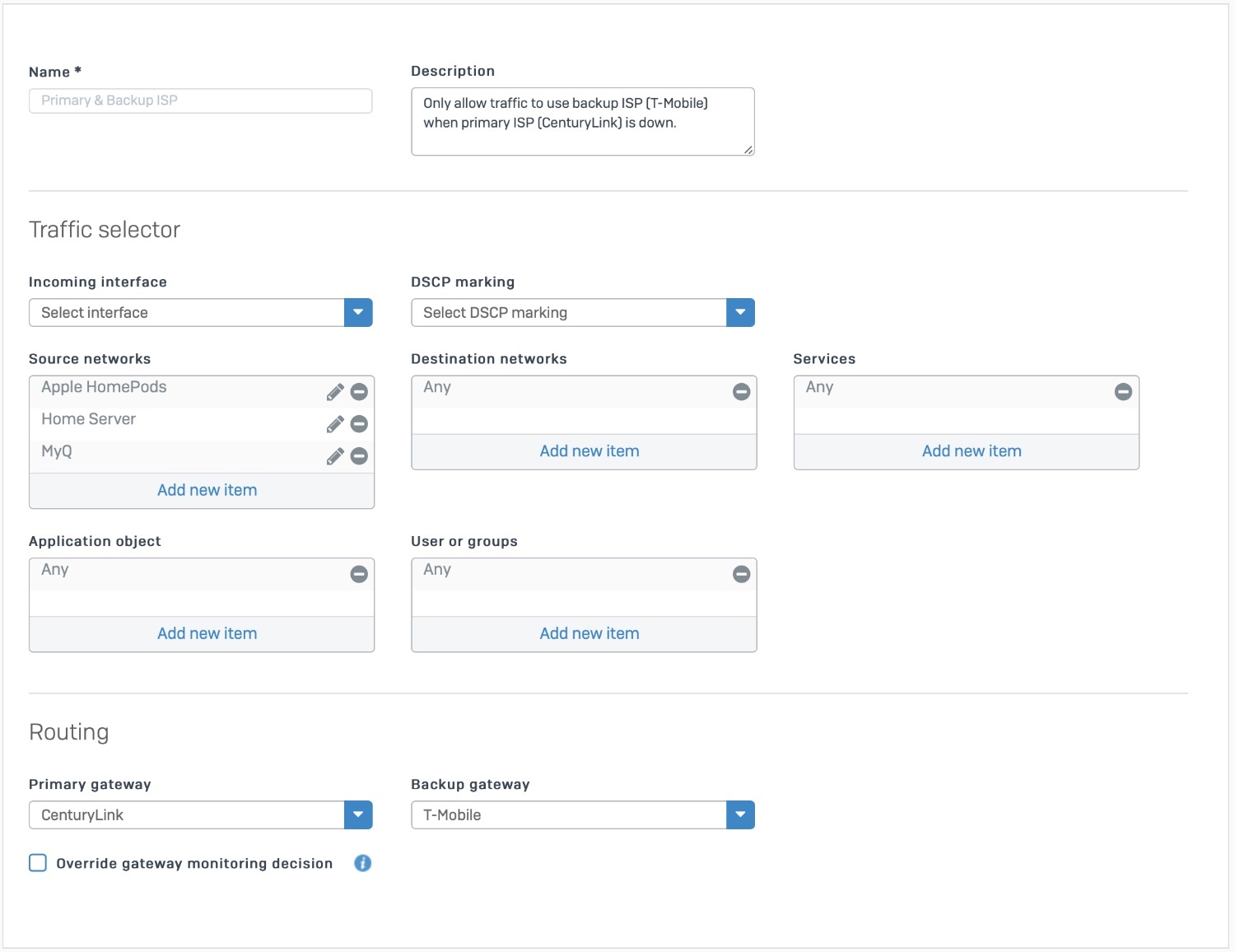
I currently have Sophos XG installed on a Qotom Q335G4 box with two ISPs, a primary and a backup for just a few devices. I have an SD-WAN policy route setup that allows this:
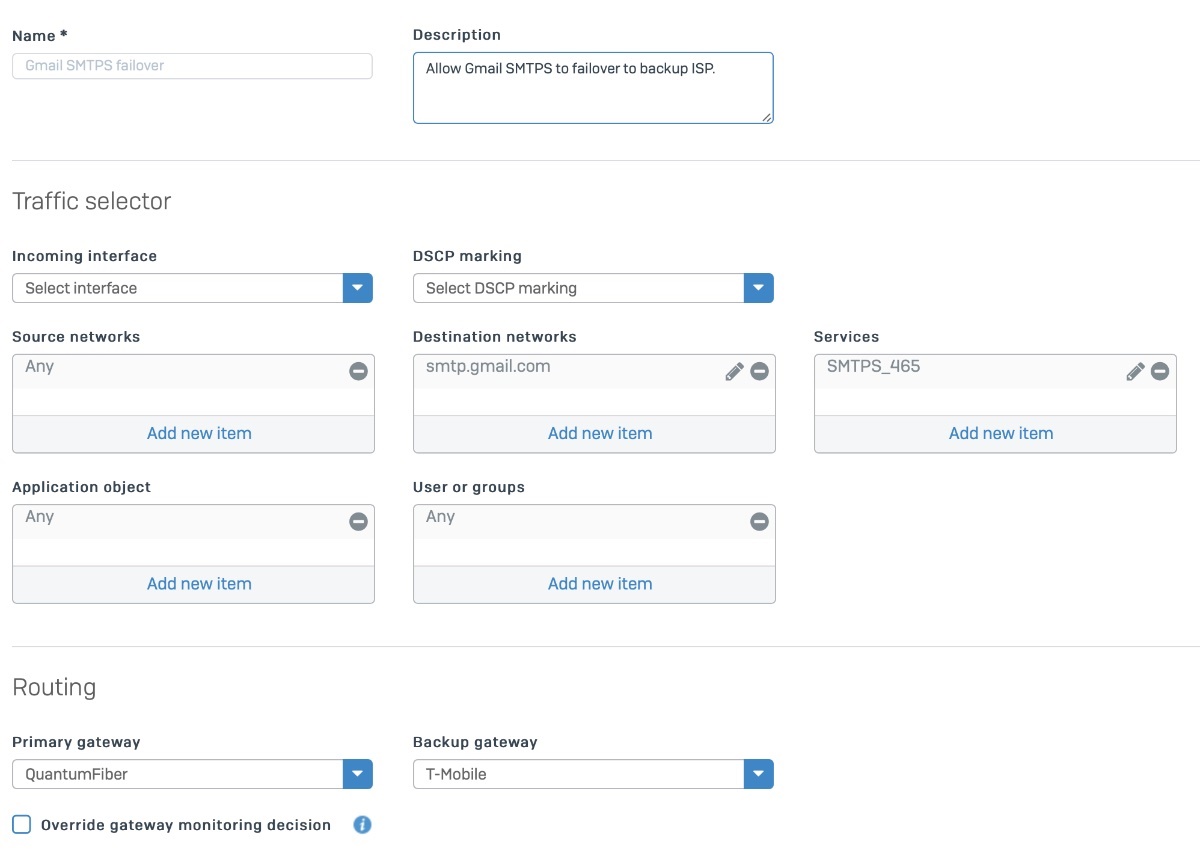
Everything works as expected but I also have email notifications setup in Sophos XG so I'll get an email when one of the ISP interfaces is down. However, when my primary ISP is down, I don't seem to get any emails until it comes back up. I'm assuming it's because Sophos XG itself is only using the primary ISP. Is there a way to allow the Sophos XG device itself to fail over to the backup ISP as well?
This thread was automatically locked due to age.