Assume, that I got the following email:
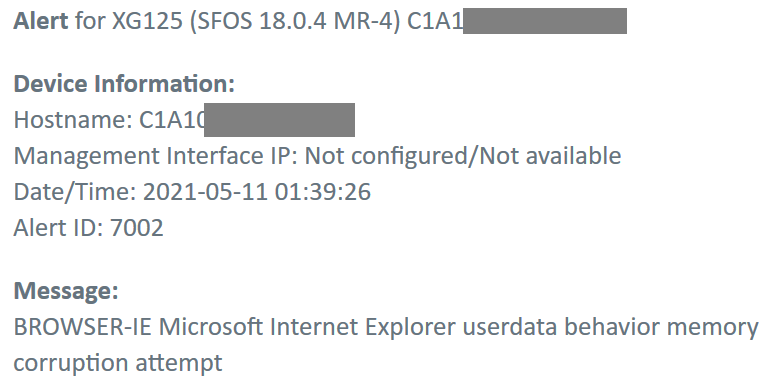
This almost says nothing. The hostname above is the host name of the XG, not the source or the destination of the attack.
Information, that I really must have:
- Source IP of attacker
- Destination IP
- Some kind of signature ID
- The IPS policy, in which the matched signature is contained
- The firewall rule ID
maybe even more
Where can I find that information?
Also, as a result, the "attacker" will become blocked. (I guess). For how long? Where is a list of all blocked attackers? How can i manually unblock an IP? In the above case, this was not necessary, but I also had legitimate actions triggering the IPS.
Why is there no information in the log files? The Log Viewer shows nothing (yes, I have both checkboxes enabled in System Services -> Log Settings -> IPS) and also /log/ips.log does not contain anything:
fgrep -i "BROWSER-IE Microsoft Internet Explorer" /log/*
This yields nothing! Also, specifically searching /log/ips.log yields nothing. There are no entries in /log/ips.log at the time stamp mentioned in the email. How is that possible? Searching for 7002 only shows entries where the timestamp contains 7002. Also this ID is completely useless, because any IPS message has this ID.
YES, I know, there is the report section in the web GUI. But it only shows AGGREGATED information. I do not want this. "Reports" shows a list of attacker IPs, a list of destination IPs and a list of attacks, but NOT which of those belong together. I want detailed information about every single event. Where can I find that?
And as a side note: "Log Settings" and "Notification List" should not be two separate settings. And they definitely should not be different lists. It should be possible to configure for any event where it shall go: Email, SNMP and/or Log.
This thread was automatically locked due to age.


