My Sophos XG installation has stopped validating. The time is correct on the firewall and it has an internet connection.
In the licensing log, there is a device not found error
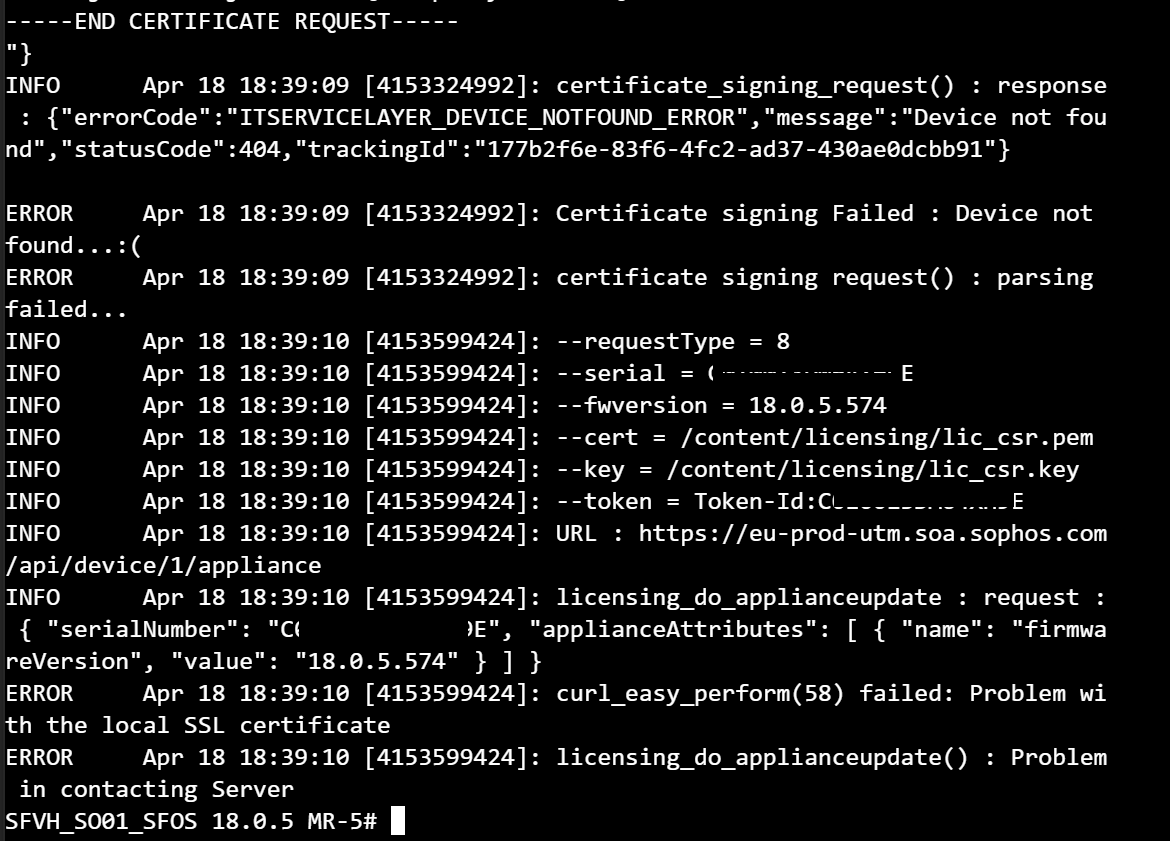
The content/licensing folder is empty
This thread was automatically locked due to age.


