Hi community,
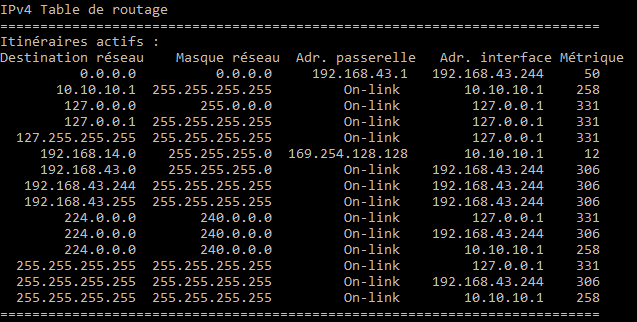
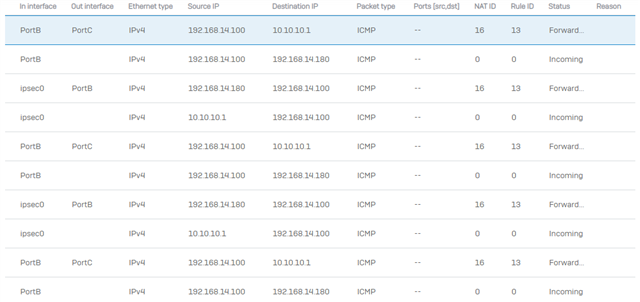
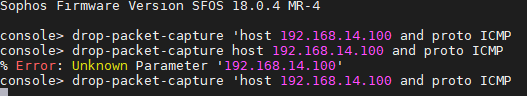
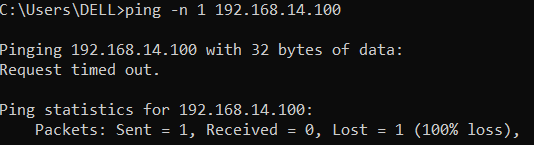
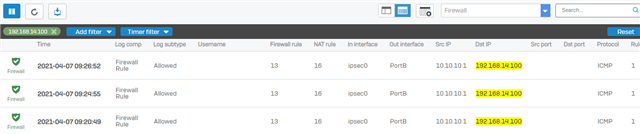
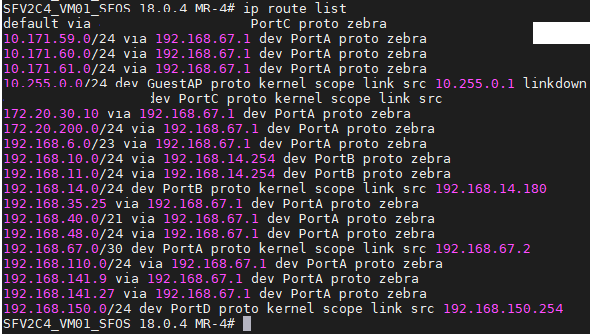
I am facing a problem when i try to tunnel only the traffic to my internal network and other traffic like the internet forwarded to user's remote gateway, in the IPsec remote access section i disabled "make the firewall the default gateway" and entered only the networks that i want to tunnel through the vpn tunnel but its not working.when i connect using sophos connect GUI i can't have access to anything neither the internet nor the remote networks behind the firewall.
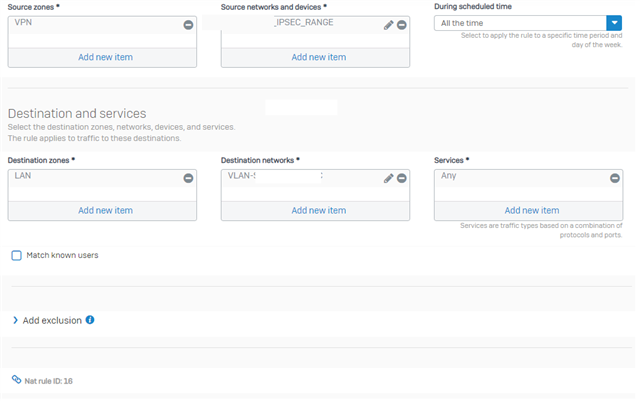
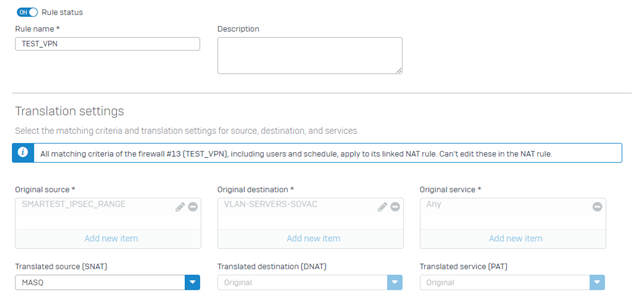
Ofcourse i created a firewall rule to allow traffic from the IPSEC IP RANGE and VPN zone to access the desired network with a linked NAT with MASQ as the source.
THANKS for the HELP GUYS!!
This thread was automatically locked due to age.