Scenario
We want to offer a NBN/4G failover solution for our customers. We are a layer 2 provider so we have full access to radius ips etc
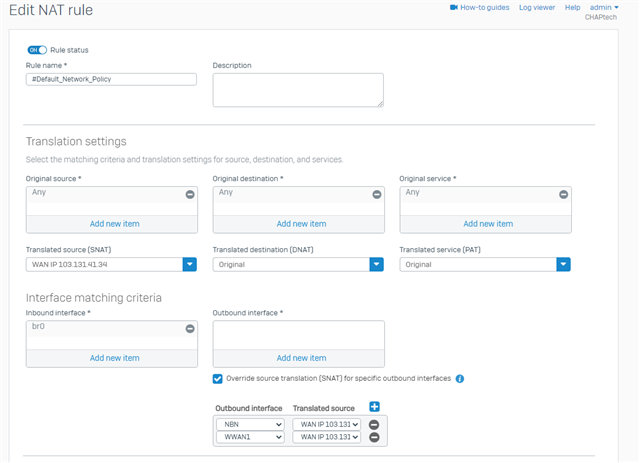
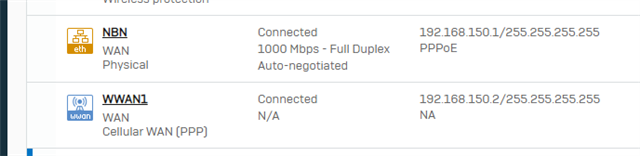
I have setup the UTM so that Port #2 is NBN which is the primary wan and have set an internal private IP as its wan IP, ie 192.168.111.1 and then also have a 4G WWAN setup as the active failover which has a wan IP of say 192.168.111.2, then in radius we used a Framed-Route for the public wan address on both connections with the 4G having a metric of 250, so only active when the NBN is offline. This side of things we do a lot and works well in a Cisco environment.
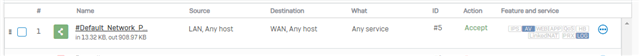
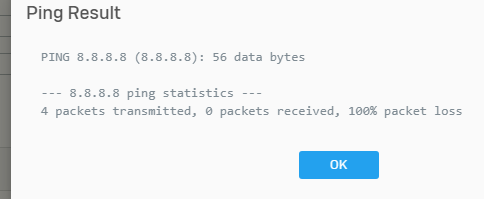
What I then tried was just make an IP Host entry for the public IP and change the default SNAT rule so the source translation from MASQ to the WAN IP Host entry, in theory this should do what I want but doesn't.... I figured maybe I need to bind that Public IP to a loopback or physical interface but there isn't a equivalent of loopback on the SFOS so I tried doing an alias interface on both the NBN interface and the LAN interface, in both cases I could then ping the Public IP outside in no problems, If i do a ping inside out from the Public IP i could also ping, but from the lan or bridge interface ping fails.
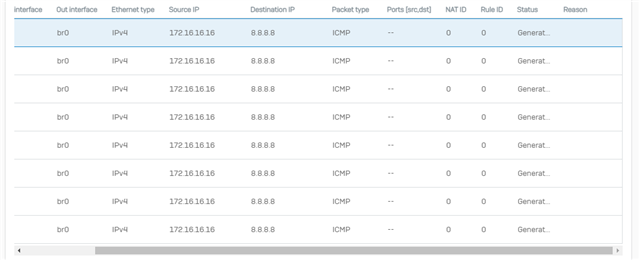
Looking in the packet trace I can try and ping google and see the icmp packet sourcing the lan interface and leaving the ppp interface but it shows firewall and nat rule 0 which im guessing is not matching ? and not masquerading on the way out ? but its a standard lan to wan fw rule with the default unlinked snat rule
I thought I was trying to do something pretty logical and basic here which is quite easy on other platforms, am I over looking something with the UTMS or need to approach it a different way?
cheers and tia
This thread was automatically locked due to age.