Hi,
some users are complaining very bad SMB performance when using SSL VPN (TCP) to our XG 18 MR4.
Our diagnosis so far is, that DS-Lite Internet users are affected by the bad performance only. Like Unitymedia / Vodafone Cable.
Users with DSL lines like Telekom without IP-Sharing ot NAT, are not affected.
Location: Germany
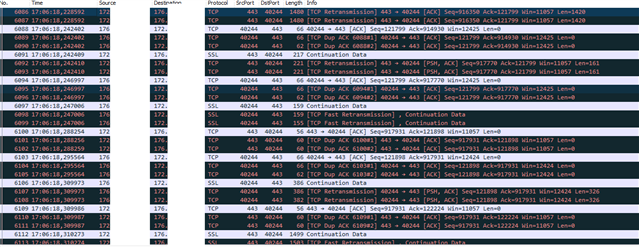
The issue can be noticed when opening a 10 kb MS Office file from an SMB share in the tunnel takes about 30-40 sec to open on DS-Lite, <5 sec on non-DS-Lite.
Opening a 1MB Text file from the same SMB share takes 10 sec on DS-Lite, ~5 Sec on non-DS-Lite.
Strange fact: downloading a large file from the same SMB share is almost the same on DS-Lite and non-DS-Lite.
What I can see in wireshark, is that the MTU is smaller on the DS-Lite side than on our XG firewall. The firewall uses 1500, the VPN client uses 1392.
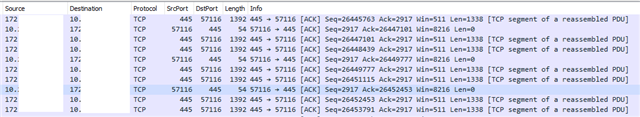
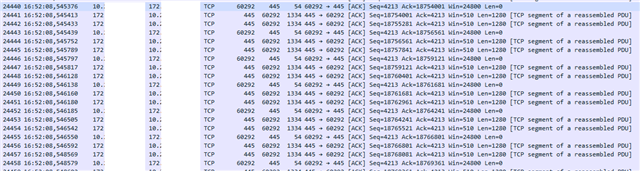
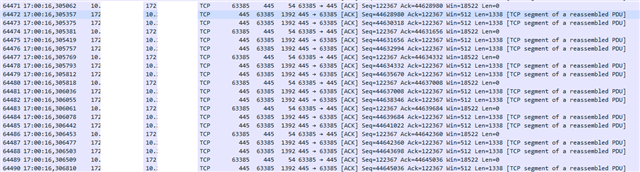
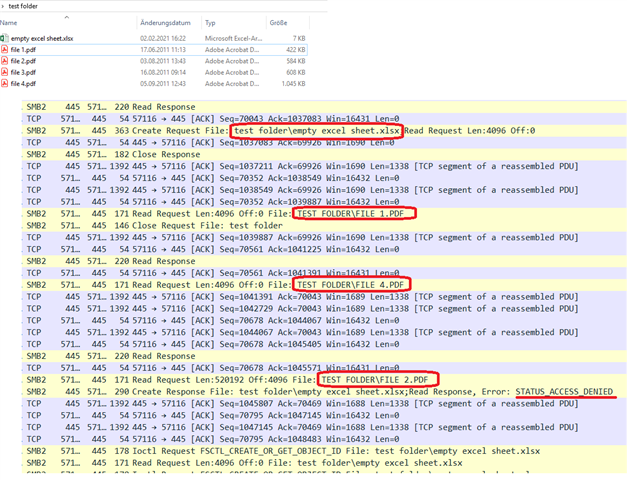
When opening one file from a SMB folder, all other files are also touched by the client and it looks like, they are fully transferred.
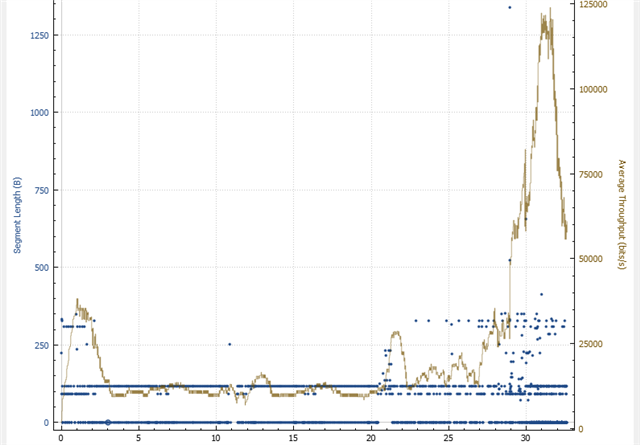
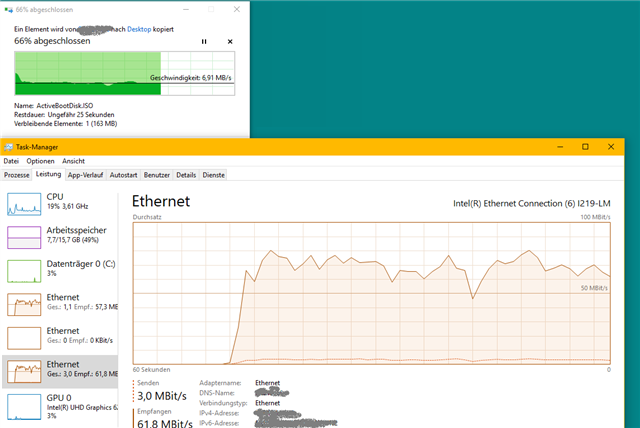
This is what downloading a 500 MB iso-file from the tunnel SMB share to the local machine looks like on DS-Lite. Performance is really OK. Nothing to complain about:
This thread was automatically locked due to age.