We have 40+ XGs for our clients in MS Azure and now one of them wants to block most web activities, except for a handful of sites they use (slack, gitlab, google, and a bunch of others). The problem is that Exceptions don't seem to work. I have tried regex and just the simple domain names, no luck.
- Created a Policy
- Added a bunch of categories and stuff to it, with a default allow at the bottom.
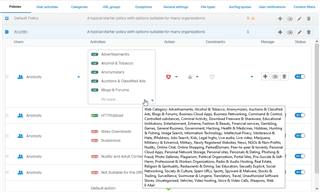
- Created Exceptions, adding all the sites they wanted to use.
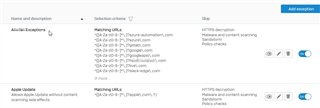
- Used Policy Test as well as created an actual Rule and all the sites are still blocked on the test machine.
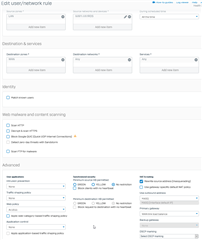
What gives? This firewall OS surprises me more and more every day.
This thread was automatically locked due to age.




