Hi,
We are presenting an inconvenience to establish the session between a Mikrotik router that is located in the main office as a remote connection router for the different remote locations which XG FIREWALL would have as a client to establish the connection.
The connections are as follows:
- MIKROTIK HEADOFFICE IP PUBLIC STATIC. SERVER RECEIVING CONNECTIONS.
- XG FIREWALL IP PUBLIC DYNAMICS. SERVER THAT ESTABLISH THE CONNECTIONS TO THE MAIN SITE.
Error message from the MIKROTIK side:
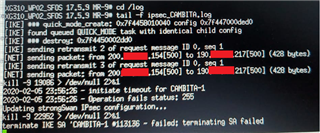
- FEB/05/2020 22:32:57 MEMORY IPSEC, INFO RESPOND NEW PHASE 1 (IDENTITY PROTECTION): 190.XXX.XXX.217[500]<=>200.XXX.XXX.154[500]
- FEB/05/2020 22:32:57 MEMORY IPSEC, INFO NO SUITABLE PROPOSAL FOUND
- FEB/05/2020 22:32:57 MEMORY IPSEC, INFO 200.XXX.XXX.154 FAILED TO GET VALID PROPOSAL.
- FEB/05/2020 22:32:57 MEMORY IPSEC, INFO 200.XXX.XXX.154 FAILED TO PRE-PROCESS PH1 PACKET (SIDE: 1, STATUS 1).
- FEB/05/2020 22:32:57 MEMORY IPSEC, INFO 200.XXX.XXX.154 PHASE 1 NEGOTIATION FAILED.
Error message from the XG FIREWALL side:
XG CONFIGURATIONS:
IPSEC POLICIES:
- key schange: IKEv1
- Authentication: Main mode
- key negotiation tries: 5
- Re-key connection: ON
- PHASE1:
- key life: 5400
- Re-key margin: 360
- Randomize re-keying margin: 100
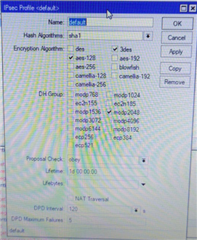
- DH GROUP: 14 DH2048
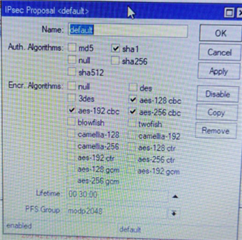
- Encryption: AES128 Authentication: SHA1
- Encryption: 3DES Authentication: SHA1
- PHASE2:
- PFS GROUP: 14 DH2048
- Key life: 5400
- Encryption: AES192 Authentication: SHA1
- Encryption: AES128 Authentication: SHA1
- Encryption: AES256 Authentication: SHA1
- DEAD PEER DETECTION:
- Check peer after: 30
- Wait for response up: 120
- When Peer unreach: Disconnect
IPSEC CONNECTION:
- Genral Settings:
- Connection type: Host to Host
- Gateway type: Initiate the connection
- Encryption:
- Policy: XXXXXXXX_MK
- Authentication type: Preshared key
- Gateway Settings:
- Local gateway Interface: Port3: 200.XXX.XXX.154 (NO ROUTER NAT)
- Local ID Type: N/A
- Local Subnet: N/A
- Remote Gateway Address: 190.XXX.XXX.217
- Remote ID Type: N/A
- Advanced:
- User authentication mode: As Client
- Username: Sophos1234
- Pass: Sophos1234
MIKROTIK CONFIGURATION:
PHASE 1:
PHASE 2:
The MIKROTIK ROUTER its behind a NAT Router with static pubic ip.
I follow all this URL https://community.sophos.com/products/xg-firewall/f/vpn/89428/ipsec-site-to-site-tunnel-between-mirkotik-xg105-failing-second-phase-peer-did-not-accept-any-proposal-sent and we still have problems. I try with ipsec site to site with IKEv2.
Thanks
This thread was automatically locked due to age.