Hello,
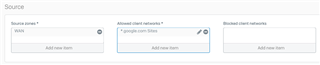
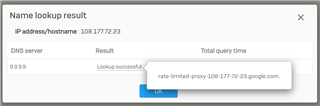
I created a DNAT rule and I am trying to block all incoming traffic unless it is coming from a *.google.com domain. I have set up a FQDN host of *.google.com and added it to the "Allowed client networks" but it doesn't seem to be doing a reverse DNS lookup on the traffic. For example, one of the IPs is 108.177.72.23 and when I do a DNS lookup on it in the diagnostics it correctly finds the address as "rate-limited-proxy-108-177-72-23.google.com" but the rule doesn't allow the traffic through. Is this type of rule possible with Sophos XG?
DNAT Rule:
DNS Lookup:
Thanks.
This thread was automatically locked due to age.