Hi,
I just figured out to set the XG Firewall to used it only with Web Filtering.
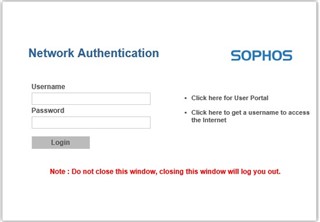
Now when I have hit on a blocked policy, I'm redirected to the Captive Portal and I get the Network Authenticaion to login.
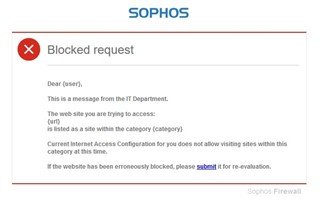
But I want to get the " Blocked Request" page and not the Network Authenticaion page.
How do I accplish this?
TIA
This thread was automatically locked due to age.