Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
This article provides details on how to integrate Sophos Intercept X for Mobile with Microsoft Intune. Details are also available in the Sophos Mobile admin guide at docs.sophos.com
The key steps involved are:
- Bind Sophos Mobile with Microsoft Intune
- Confirm the connection in Microsoft Intune
- Deploy the Intercept X for Mobile app to managed devices through Microsoft Intune
Bind Sophos Mobile with Microsoft Intune
- Log in to Sophos Central
- Navigate to the Mobile section
- Navigate to Setup> Sophos Setup
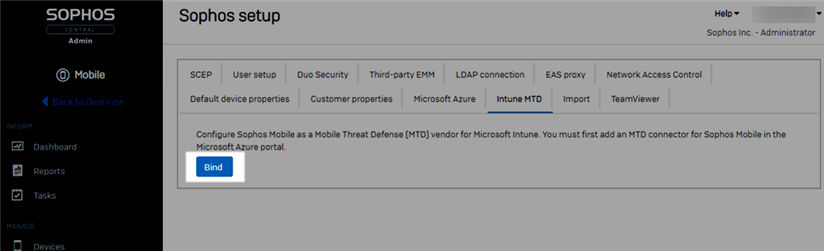
- Open the Intune MTD tab and click 'Bind'
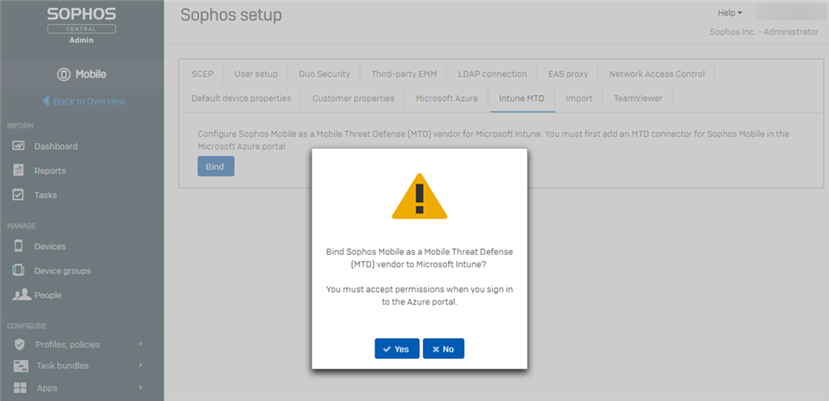
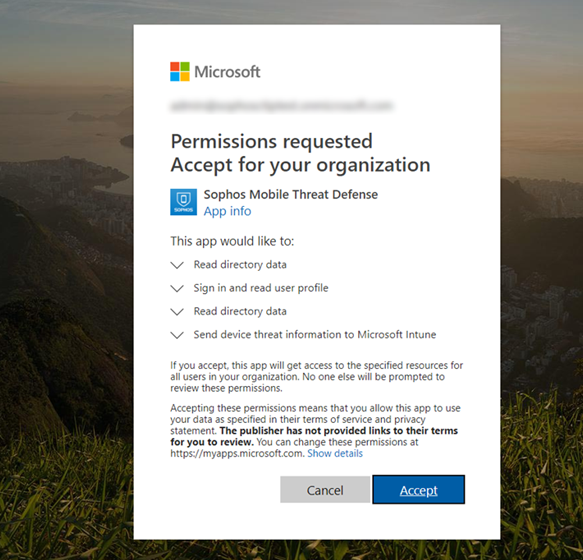
- Click Yes and log into Microsoft Intune with your Azure administrator account and accept the permission request
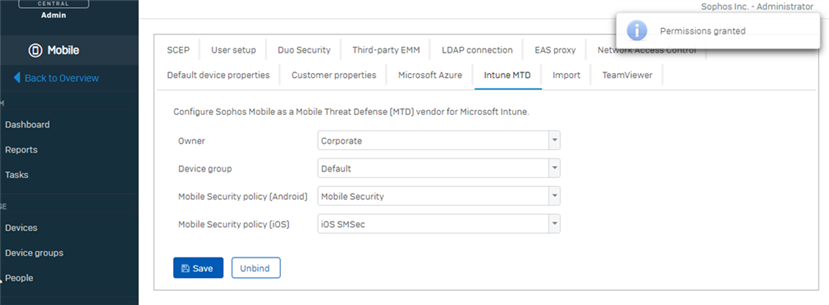
- In the Sophos Central console a message is displayed to confirm the necessary permissions have been granted. Select whether the devices will be corporate or personal devices, the device group they should be member of, and which policies the devices should receive. Click Save.
Confirm the connection in Microsoft Intune
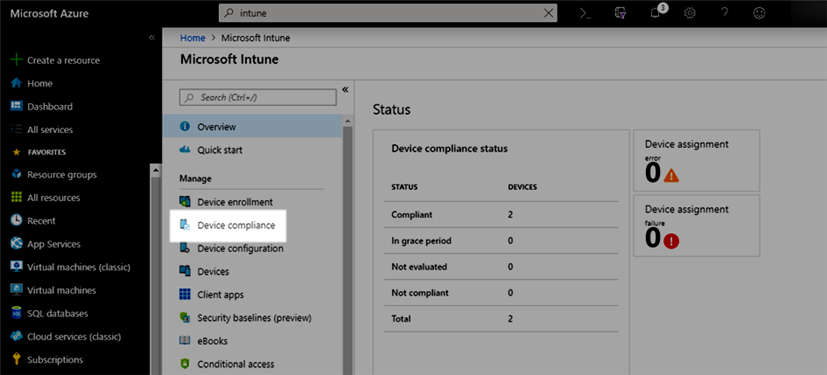
- Log in to Microsoft Azure and navigate to Intune
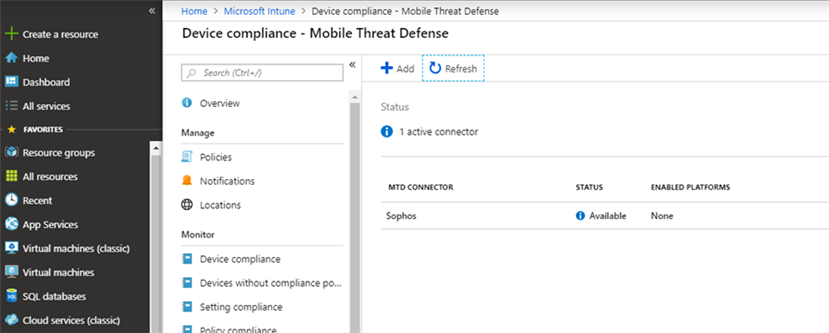
- Click 'Device compliance'
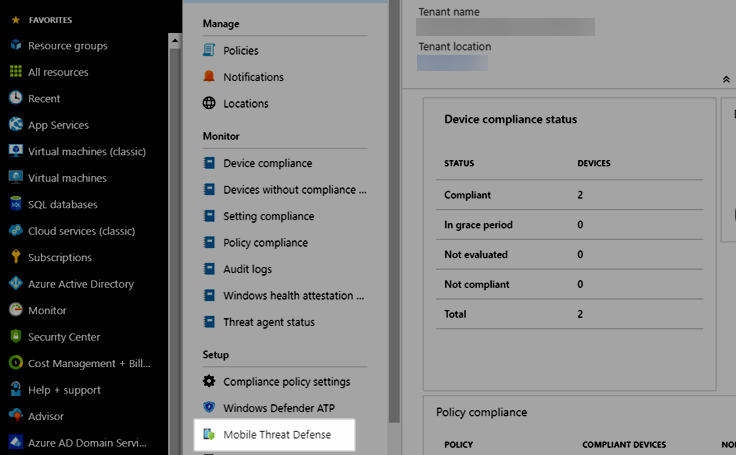
- Click 'Mobile Threat Defense'
- The Sophos connection should already be listed (as a result of the previous steps taken)
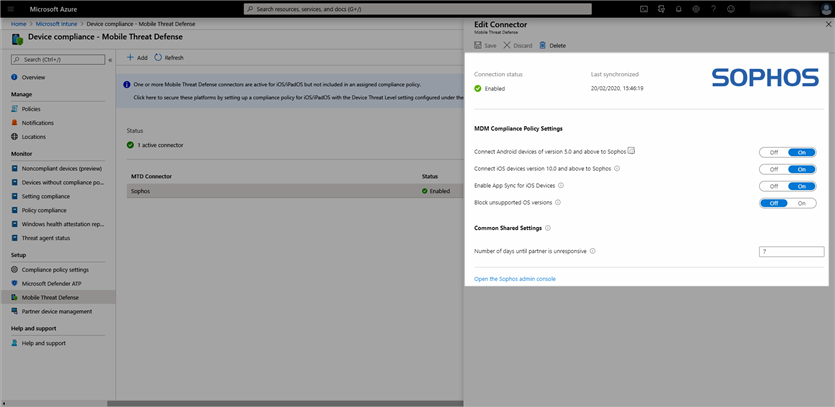
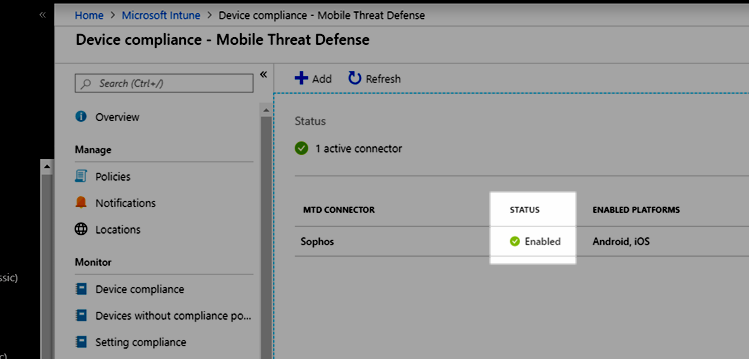
- Click on the Sophos connector and enable the Android and iOS platforms (first 2 radio buttons). Click Save and the connection status will change from Available to Enabled
Deploy Intercept X for Mobile to Intune managed devices
In this stage we will deploy the Intercept X for Mobile app to iOS and Android devices.
Nb It is also necessary for the Intune Company Portal app and Microsoft Authenticator app (on iOS) to be deployed to devices. The steps for deploying these apps are not shown here.
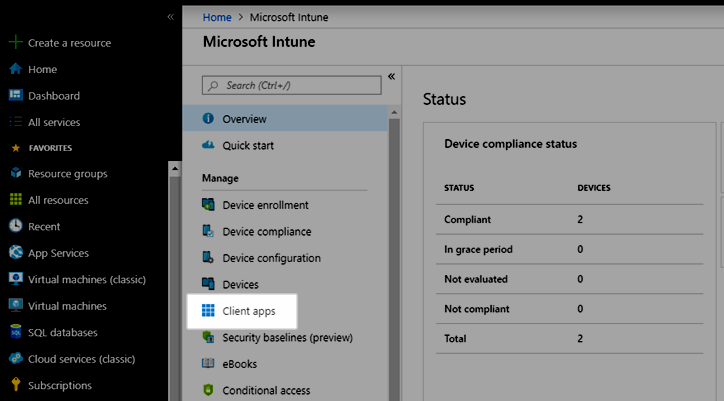
- Log in to Microsoft Azure and navigate to Intune
- Click 'Client apps'
- Click 'Apps'
Deploying to iOS devices
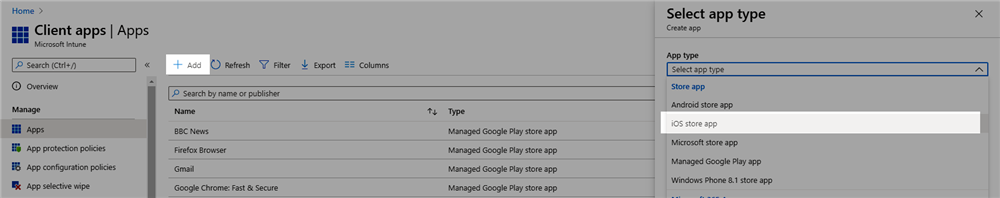
- First we will add the iOS Intercept X app. Click 'Add' and select 'iOS store app'
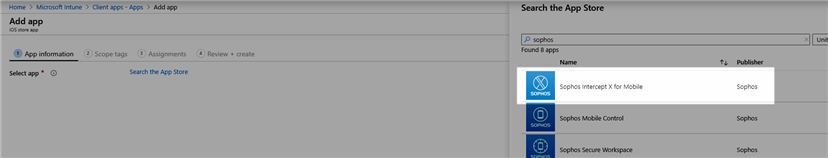
- Click 'Search the App store' and locate the Intercept X for Mobile app. Click 'Select'
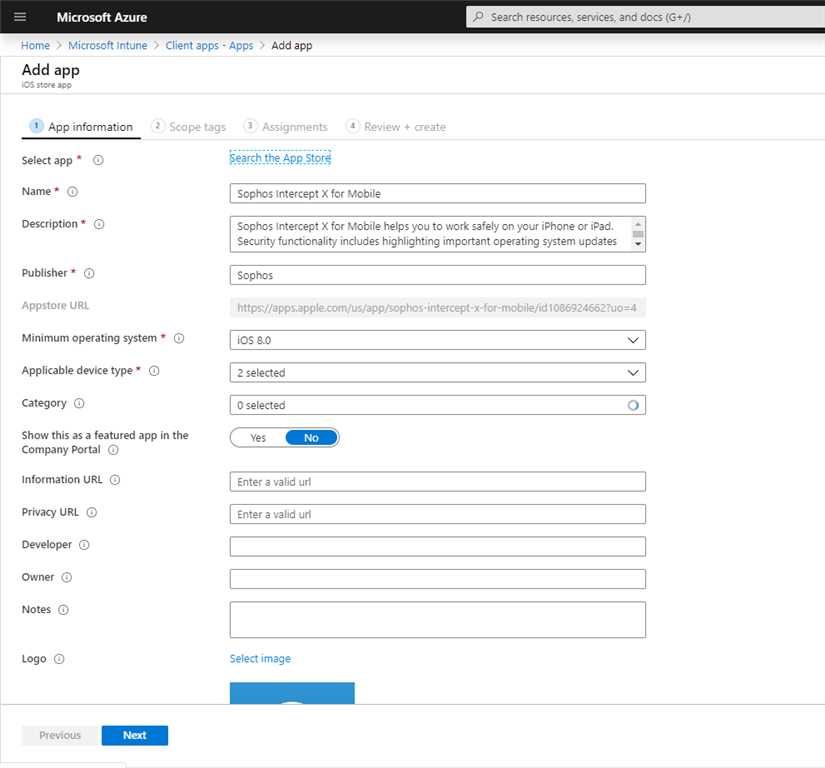
- View the app details displayed and click Next.
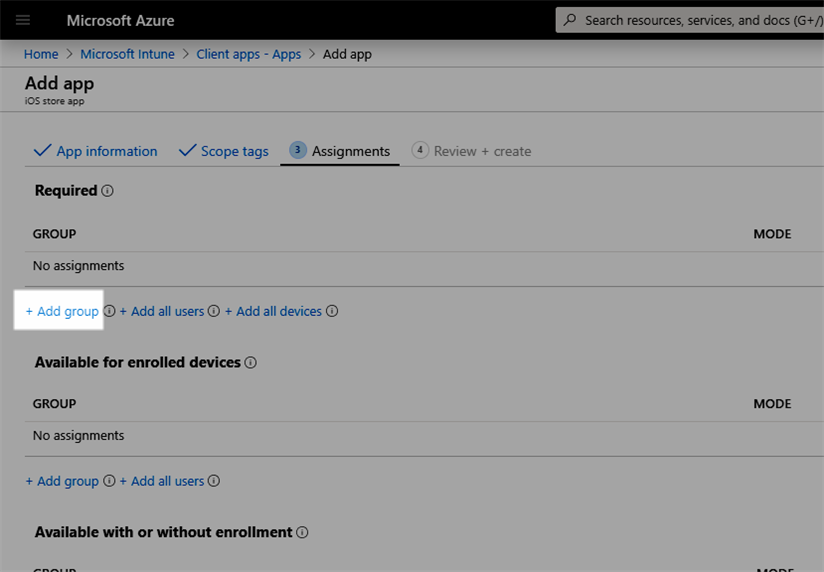
- Click Next in the The 'Scope tags' section (this section is optional)
- Click 'Add group' and select the Azure groups that you want the Intercept X app to be deployed to.
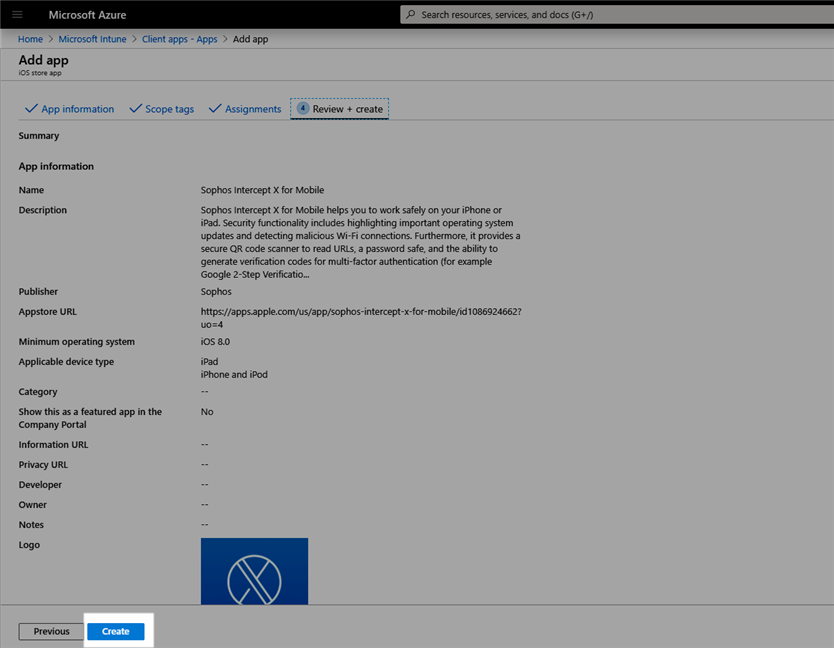
- Click Next and on the summary screen click Create. The Intercept X for Mobile app is now assigned to the iOS groups selected.
This Intercept X iOS app has now been deployed. Optionally, we can also choose to pass managed settings to the app to remove some steps for end users.
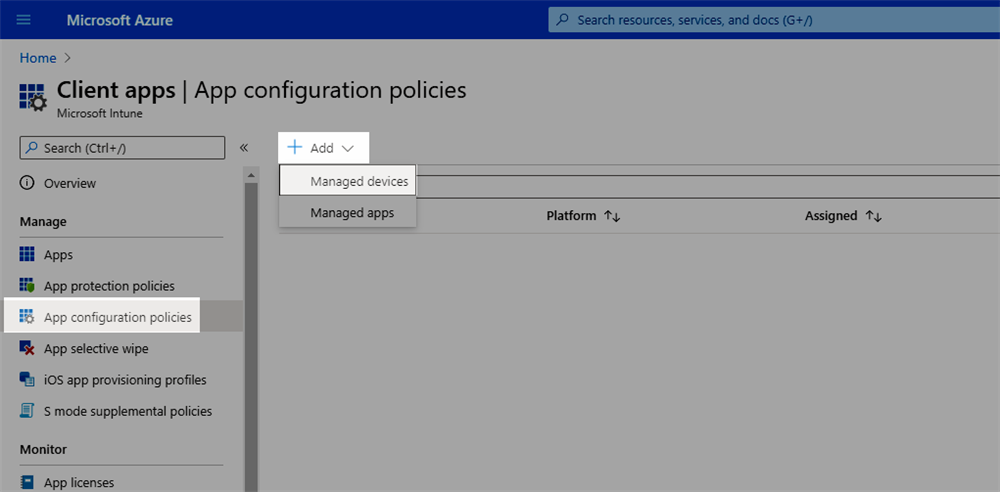
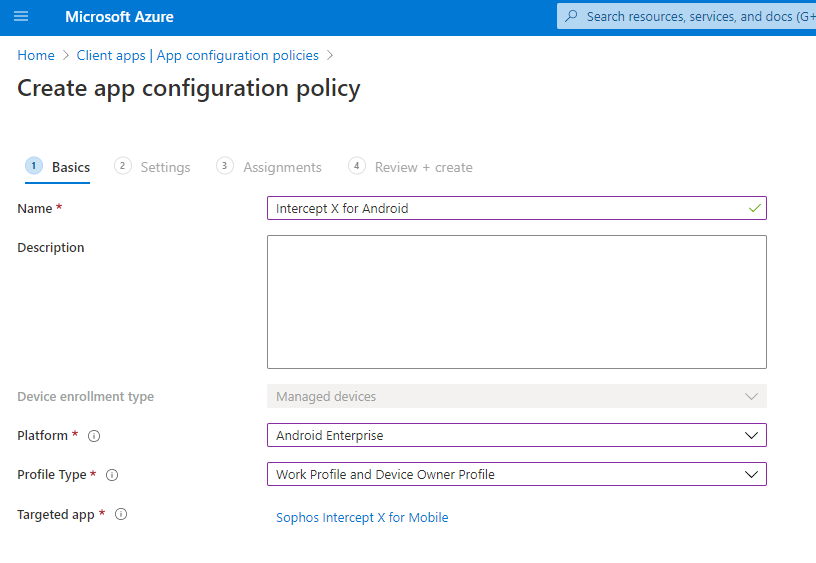
- Navigate to Clients Apps> App configuration policies. Click 'Add' and select 'Managed Devices'
- Give the policy a name, select iOS as the platform, and select Sophos Intercept X for Mobile as the targeted app
- Choose 'configuration designer' from the dropdown.
- Entering 'deviceName' allows you to choose which value will be sent to Sophos Central (e.g. User Name or User Principal Name). If this value is not selected, the Azure AD ID will be used as the device name instead. - the list of available variables is in the Microsoft documentation learn.microsoft.com/.../app-configuration-policies-use-ios
- Entering the 'eulaDisabled' and 'startIntuneConnection' values removes the need for end users to accept the EULA, and makes it easier for them to complete the app enrolment - please note, the entries are case sensitive ('eulaDisabled' and 'startIntuneConnection')
- Click Next to move to the 'Assignments' page. Assign the policy to the required group of users.
- Move to the 'Review + Create' page to complete and save the policy.
Optional - deploy web filtering profile
Intercept X for Mobile on iOS uses a web content configuration profile to provide web filtering on supervised iOS devices. Administrators can deploy the profile to devices, preventing end users having to install it themselves.
- Obtain the file by browsing to the following location: https://secureservices.sophosmc.com/webfiltering/activate-smsec-plain.mobileconfig
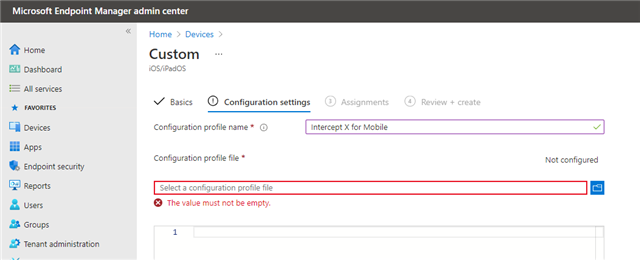
- In Intune, go to Devices> Configuration Profiles> Create profile and select a 'Custom' iOS profile

- Follow the wizard and give the policy a name. On the 'Configuration settings' page, upload the .mobileconfig file that was just downloaded
- On the 'Assignments' tab, select the devices to assign the configuration profile
After saving the policy, the web content configuration policy will be deployed to devices.
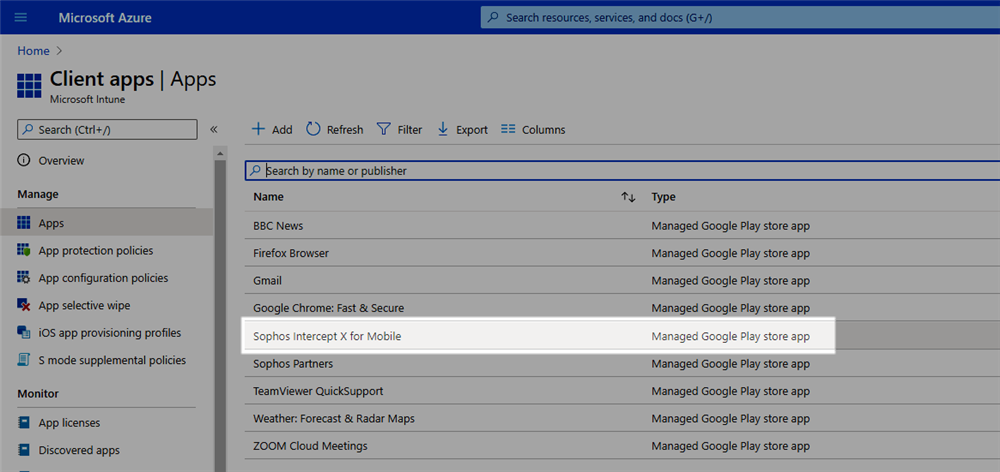
Deploying to Android devices
- Return to the Client Apps> Apps section
- Click Add
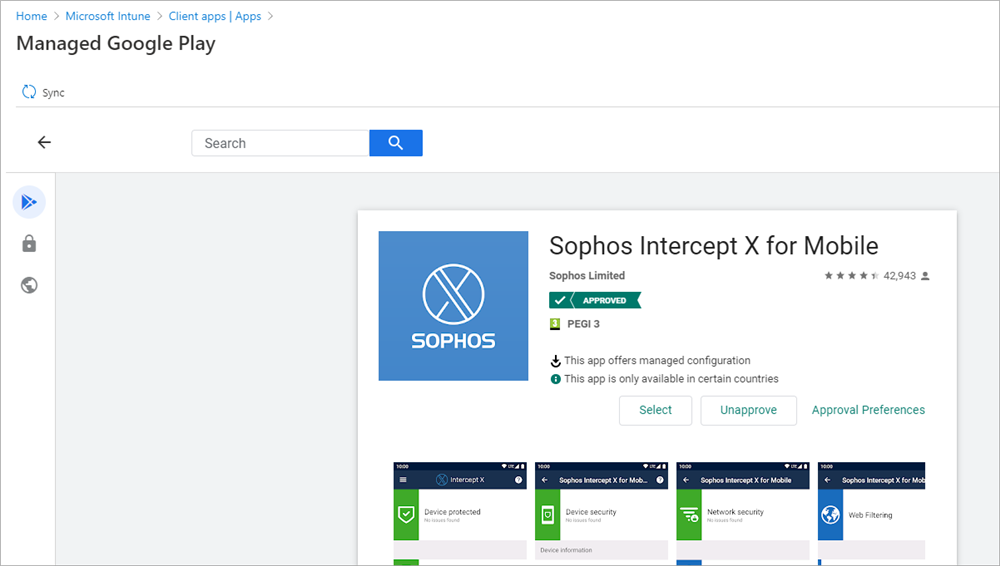
- Select Managed Google Play app
- Search the Play Store for Sophos Intercept X
- Select Intercept X and approve the app. After approving the app return to the Intune Client Apps page.
- The Intercept X app will now appear in the list of apps. Note that some information is synced from the Google Play Store so it can take a few minutes for the app to be shown.
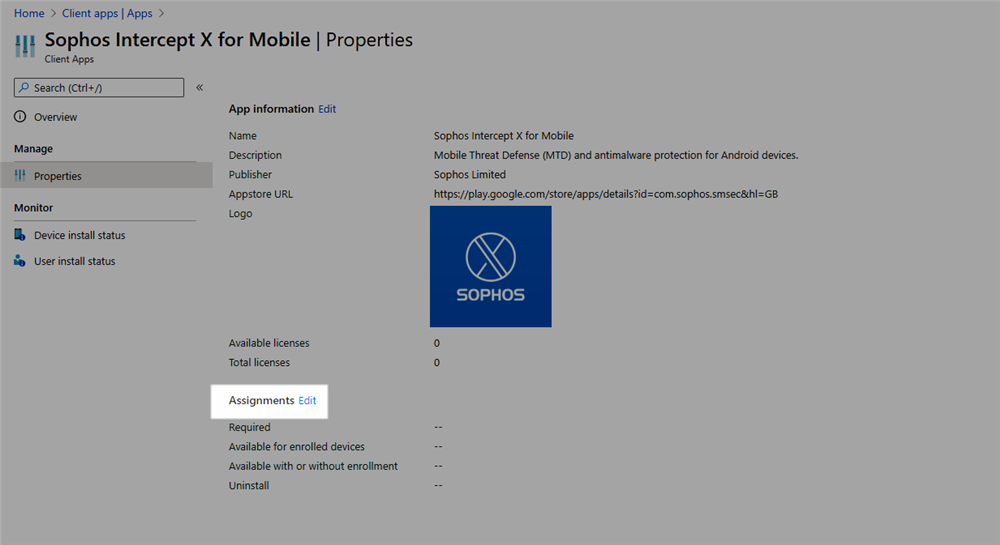
- Click on the Intercept X app and go to Properties> Assignments> Edit
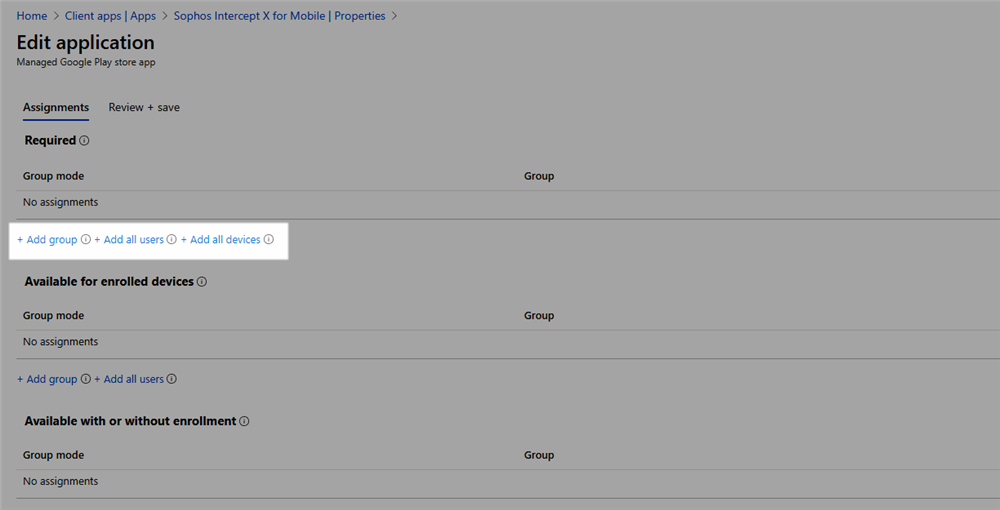
- Use the 'Add group' (or 'Add all users' or 'Add all devices') to deploy the Intercept X app to devices
- Click 'Review + Save' to check the details, and click Save
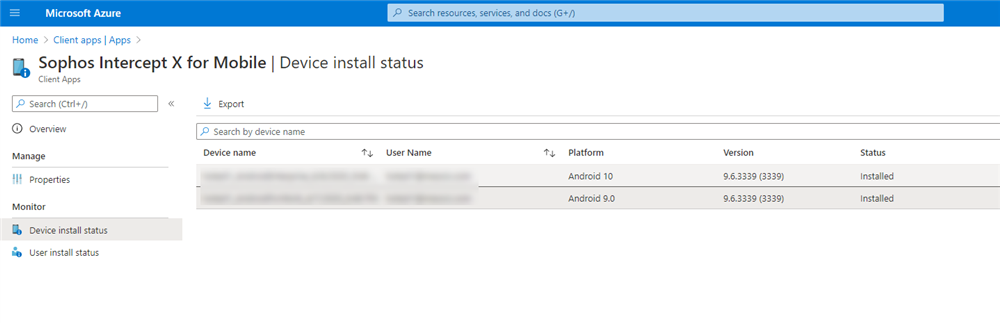
- The 'Device install status' tab shows the success of deployments
This Intercept X Android app has now been deployed. Optionally, we can also choose to pass managed settings to the app to remove some steps for end users.
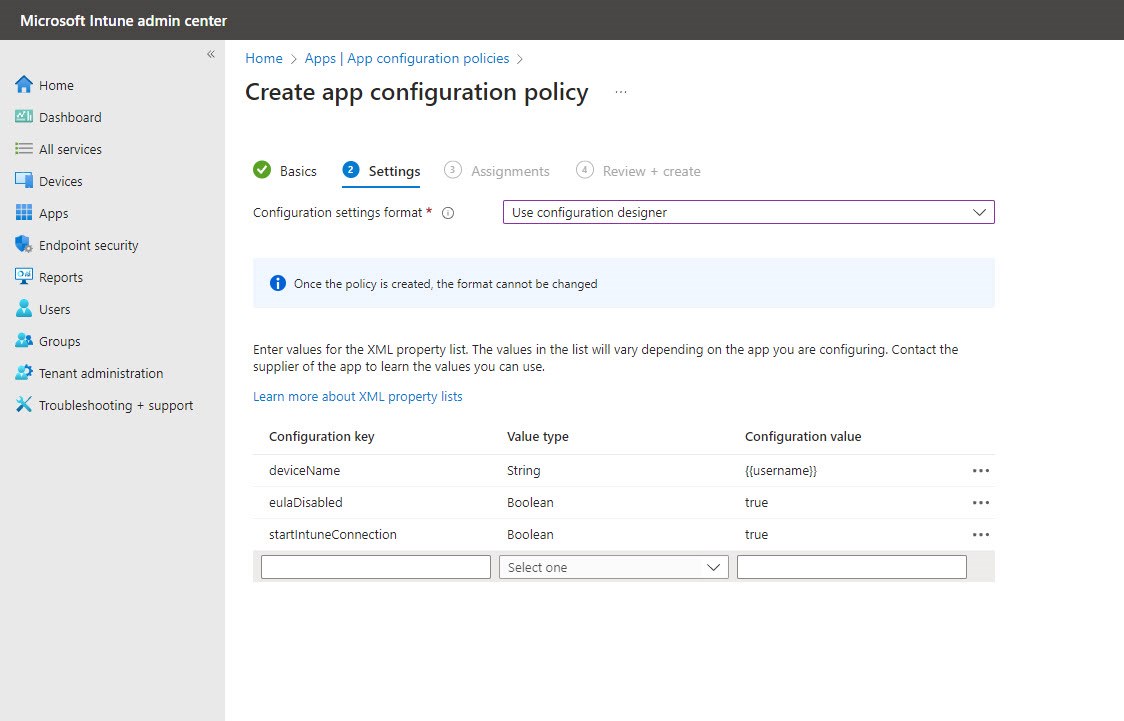
- Navigate to Clients Apps> App configuration policies. Click 'Add' and select 'Managed Devices'
- Give the policy a name, select Android Enterprise as the platform, the profile type as Work and Device Owner, and select Sophos Intercept X for Mobile as the targeted app
- In the Permissions section click the 'Add' button. This allows you to auto-grant permissions for the app, meaning the end user is not prompted to provide them
- For example provide permission for Storage (to enable malware scanning) and Location (to enable wifi man-in-the-middle protection)
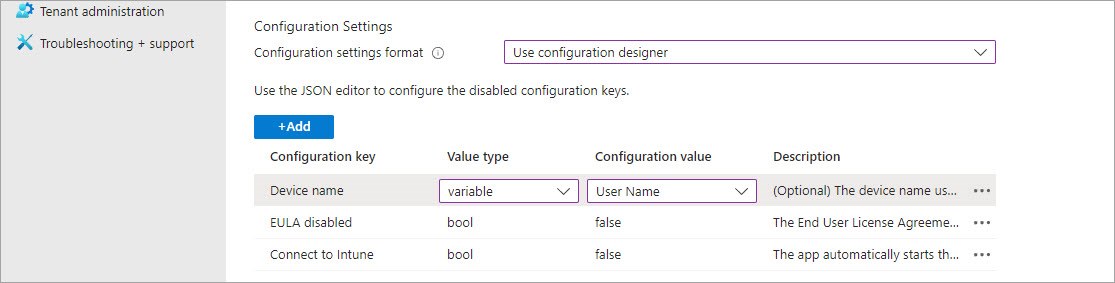
- In the Configuration Settings section select 'Use configuration designer' from the dropdown and click the 'Add' button
- Add the configuration keys as shown below.
- Device name - the device name that will be sent to Sophos Central (e.g. User Name or User Principal Name). If this value is not selected, the Azure AD ID will be used instead.
- The 'EULA disabled' and 'Connect to Intune' remove the need for end users to accept the EULA, and makes it easier for them to complete the app enrolment.
- Click Next to move to the 'Assignments' page. Assign the policy to the required group of users.
- Move to the 'Review + Create' page to complete and save the policy.
Have an idea or suggestion regarding our Documentation, Knowledgebase, or Videos? Please visit our User Assistance forum on the Community to share your idea!
Updated
[edited by: tom_w at 4:20 PM (GMT -7) on 19 May 2023]