Sophos Factory offers pre build pipelines to upload and manage certificates on a Sophos Firewall.
For example can you upload and use Certificates like LetsEncrypt Certificates in SFOS with those Pipelines.
If you have a Certificate already generated like described here: [HowTo] Lets Encrypt Renewal Process with Factory
You can simply use those certificates with the predefined Pipelines. You find them in the global catalog: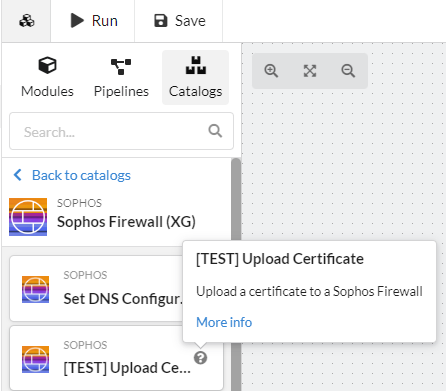
This Pipeline require the following Inputs:
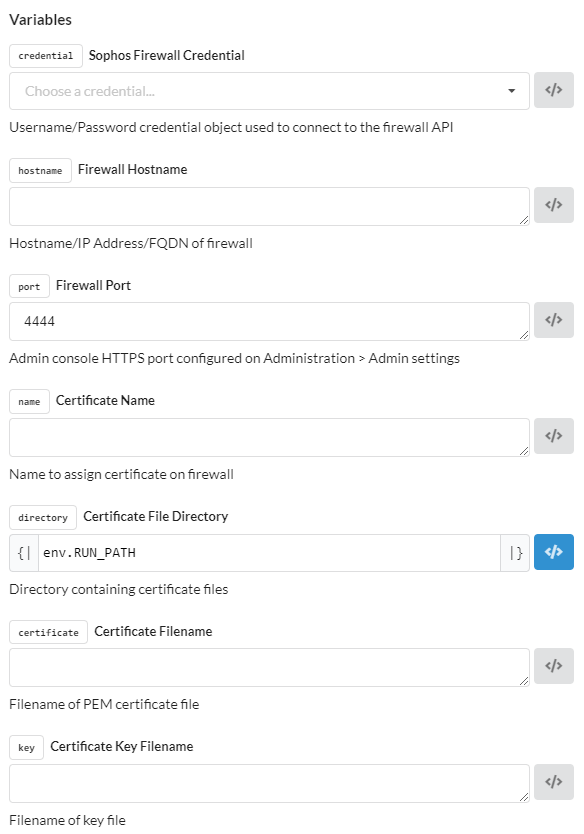
Which could be extracted by a pipeline before that. Like this one: [HowTo] Lets Encrypt Renewal Process with Factory
In combination:
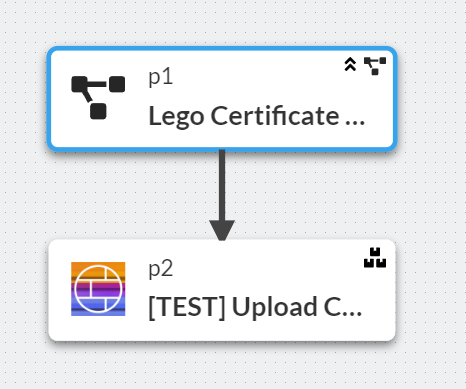
Which will upload the certificate to the firewall.
To integrate the Firewall, please follow the following: Sophos Factory: Integrate Sophos Factory with Sophos Firewall
This would be the editor code for everything:
---
variables:
- type: String
name: Domain
key: domain
required: true
visible: true
default: false
description: Domain to Generate and Upload
- type: String
name: hostname
key: hostname
required: true
visible: true
default: false
steps:
- id: p1
name: Lego Certificate Renewal
type: pipeline
depends: []
properties:
pipeline_id: 6479fd20949984ba31087e65
pipeline_revision_id: latest
variables:
credential: Saleseng
domains: '{|vars.domain|}'
email: admin@saleseng.de
url: 'https://github.com/go-acme/lego/releases/download/v4.10.0/lego_v4.10.0_linux_386.tar.gz'
provider: route53
resolvers: 8.8.8.8
tos: true
- id: p2
name: '[TEST] Upload Certificate'
type: pipeline
depends:
- p1
properties:
pipeline_id: 6526c138429a74127ab653d1
pipeline_revision_id: 652706774512ac34f47a4896
variables:
credential: FirewallCreds
hostname: '{|vars.hostname|}'
port: '4444'
name: '{|vars.domain + date_format(''yyyy-MM-dd'') |}'
directory: '{|env.RUN_PATH + "/.lego/certificates"|}'
certificate: '{|vars.domain + ".pem"|}'
key: '{|vars.domain + ".key"|}'
outputs: []
layout:
elements:
- id: p1
position:
x: -85
'y': -180
links: []
- id: p2
position:
x: -85
'y': -95
links:
- sourceId: p1
sourcePort: bottom
targetPort: top
vertices: []
Fully automated Upload:
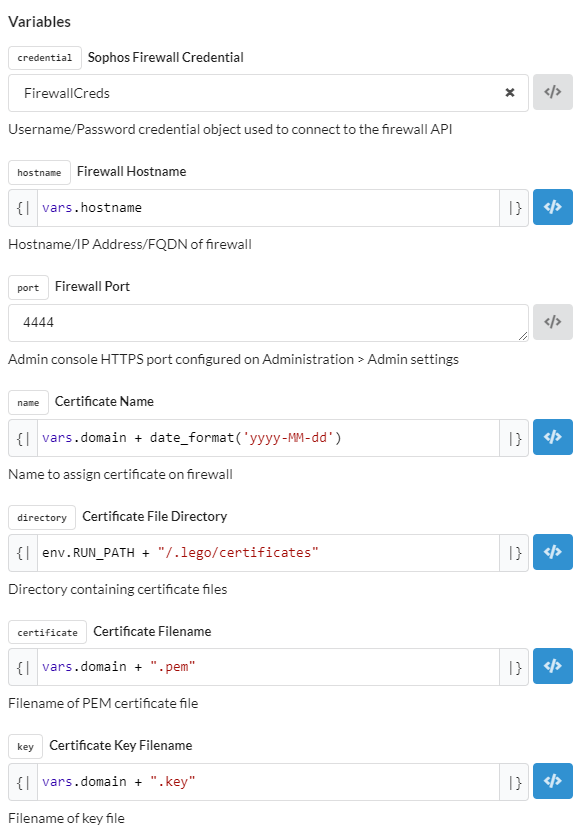
Edited TAGs and Title
[edited by: emmosophos at 11:11 PM (GMT -7) on 1 Apr 2024]

