Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Background
On October 18th, 2023, the Cybersecurity Infrastructure and Security Agency (CISA), the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released this joint guide: Phishing Guidance: Stopping the Attack Cycle at Phase One.
The joint guide outlines phishing techniques malicious actors commonly use and guides network defenders and software manufacturers to reduce the impact of phishing techniques in obtaining credentials and deploying malware. The goal of this post is to create a repository of best practices and steps to secure your Sophos Central platform alongside this guidance.
We’ll primarily focus on Sophos Central email Protection and Phish Threat.
Phishing to Obtain Login Credentials
Defined as "Malicious actors pose as trustworthy sources (e.g., colleagues, acquaintances, or organizations) to lure victims into providing their login credentials. Malicious actors can use the compromised credentials (e.g., usernames and passwords) to access enterprise networks or protected resources, such as email accounts."
Example Techniques
- Impersonation
- Smishing
- Spoofing caller ID for social engineering
Multifactor Authentication
- Weak Examples:
- Accounts without FIDO or PKI-based
- Push notification without number matching
- SMS or voice MFA
Mitigations
- Implement User Training on Social Engineering and Phishing Attacks
- We offer 30-day trials of Sophos PhishThreat
- Here is the FAQs link
- Existing customers can deploy a campaign in less than 2 minutes!
- Enable Domain-based Message Authentication, Reporting, and Conformance (DMARC)
- Sophos Email: Message Authentication: DMARC, SPF, DKIM
- Microsoft 365: Use DMARC
- Google Workspace: Help with DMARC
- Ensure DMARC is set to "reject" for sent emails
- Policy values explained here
- Sophos Email supports multiple failure types across SPF and DKIM as well
- Implement internal mail and messaging monitoring
- Sophos email: implement Data control policies
- Comprehensive analysis of tools
- Create individual, group, or weighted conditions
- Sophos email: implement Data control policies
- Implement free security tools
- Sophos free tools are here
- Sophos Intelix is included with your central ID
- Harden credentials
- Use FIDO or PKI-based MFA
- Prioritize phishing-resistant MFA for admin/privileged user accounts
- Implementing centralized logins and SSO
- Review MFA lockout and alert settings and track denied (or attempted) MFA logins.
Malware-based Phishing
"Malicious actors pose as trustworthy sources (e.g., colleagues, acquaintances, or organizations) to lure a victim into interacting with a malicious hyperlink or opening an email attachment to execute malware on host systems."
Example Techniques
- Malicious hyperlinks
- Malicious attachments
- Smishing
Mitigations
- Incorporate denylists at the email gateway and enable firewall rules
- Enterprise Level: Sophos Central > Email Protection > Global Settings > Inbound Allow/Block
- Document link
- There’s an upcoming feature release in CY2024 to address this within the console as a GUI country option.
- Local Policy: Sophos Central > Email Protection > Policies > Data Control > Message Attributes
- Here, we can enable Top Level Domains (TLDs) or IP addresses by geographic location.
- There’s an upcoming feature release in CY2024 to address this within the console as a GUI country option.
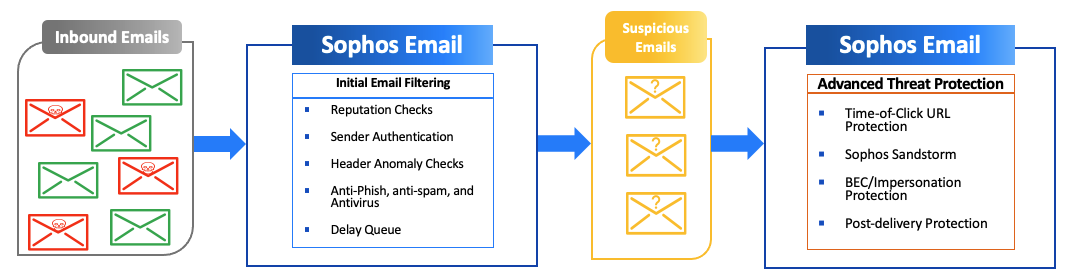
- Use denylists to block known malicious domains, URLs, and IP addresses
- See the image below for the full scanning process
- Sophos Data Control Block Defaults
- NOTE: you can configure virtual any file type
- Full Documentation is here
- Enterprise Level: Sophos Central > Email Protection > Global Settings > Inbound Allow/Block
Other Considerations
NOTE: This isn’t an exhaustive list from their report, but areas where we can support their advice
- Implement application allowlists
- Block macros by default
- Intercept X monitors for this
- XDR + MDR has rules and alerts built for this activity
- Implement remote browser isolation solutions
- Set up self-serve app store
- This is available in Sophos Central Mobile
- SFOS v20 on the XGS platform supports:
- Implement DNS filtering or firewall denylists
- Implement file restriction policies
- Enable safe web browsing policies
- Implement a secure VPN
- Or ZTNA
- Implement SSO for applications
Closing
As a best practice, be sure to maximize your ability to communicate with us:
- Receive email digests, subscriptions, and notifications from the Sophos Community
- Subscribe to the Sophos Notification alerts for products and services
- Complete the Sophos Certification Program (FREE) to obtain access to a senior support agent
- Consider using a Technical Account Manager or TAM to maximize support and minimize risk
- Subscribe to Sophos News for the latest in Threat Research and security news
- If an MDR customer, take advantage of the Monthly Threat Cast, Broadcast Announcements, and resources
- If you are not, consider our offerings to provide cyber resiliency with your staff.
- Most importantly, find out who supports your account and introduce yourself for guided best practices, feature updates, and more!
-jk
Edited title and edited TAGs
[edited by: Raphael Alganes at 8:31 AM (GMT -8) on 11 Jan 2024]
