Hi Everyone!
Do you have some emails failing to be sent to the Exchange 2019 after configuring Sophos Email gateway mode? If so, please read on.
Scenario
Used to have only Exchange 2019 (On-Prem) then Central Email Gateway mode is implemented to protect it.
Suddenly some of the inbound emails are failing delivery with a "550 5.7.1 Sender ID (PRA) Not Permitted" error.
Symptom
Message History
![]()
Message Details
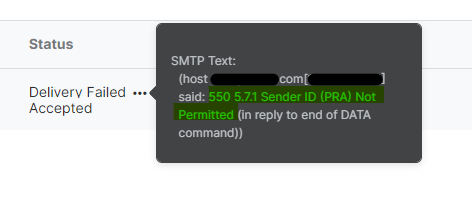
Cause
This is due to the Anti-spam agents (which Sender ID Agent is a part of) having been installed previously within the Exchange 2019 server (and has its action set to 'Reject').
By default this agent is not installed but must have been installed using the command in the Exchange Management shell:
& $env:ExchangeInstallPath\Scripts\Install-AntiSpamAgents.ps1
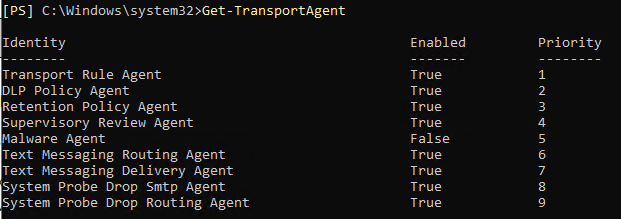
Here is the Exchange Transport Agent list by default:
Here is how it looks when the anti-spam agents are installed:
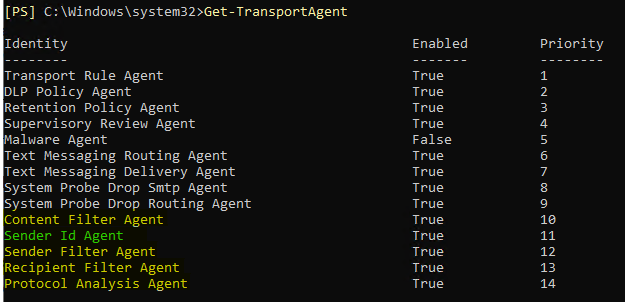
Sender ID Agent is what checks for SPF records.
It makes sense to have SPF checking while Exchange was the "edge" server however now that Sophos Email is the one accepting emails on behalf of the domain, it is now the new "edge".
Here is a Recommended Reads I have created previously explaining the proper email host to perform SPF sender checks:
Sophos Email: The proper host to do SPF sender checks
Resolution
Since Sophos Email has taken over protecting the users, we can now now either disable the Sender ID agent or change its behavior.
Options
Disable Sender ID agent:
- Within the Exchange Management Shell, use the command to confirm first if Sender ID Agent has been installed: Get-TransportAgent
- Once confirmed, use this command to disable it: Disable-TransportAgent -Identity "Sender Id Agent"
- You will get a prompt to confirm and once you confirmed Yes, it will show a warning that MSExchangeTransport service needs to be restarted.
- You can either restart it via services.msc or you can use this command: Restart-Service -name MSExchangeTransport
Change behavior of Sender ID agent:
- Within the Exchange Management Shell, use the command to confirm that the 'SpoofedDomainAction' is set to 'Reject' by using: Get-SenderIdConfig
- Once confirmed, use this command to change its setting to 'StampStatus': Set-SenderIdConfig -SpoofedDomainAction StampStatus
- Confirm that it has been applied by using the command again: Get-SenderIdConfig
Here is an example of the SenderIdConfig output where the action is set to 'Reject':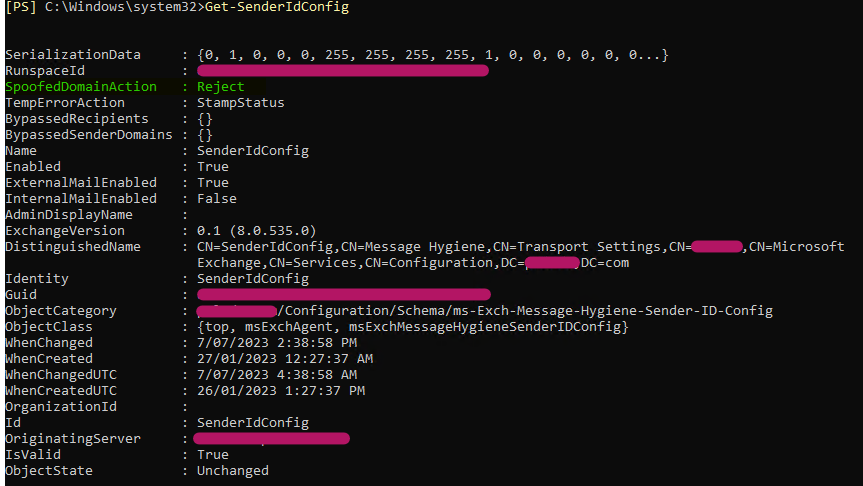
That's all!
Edited Title and edited TAGs
[edited by: Raphael Alganes at 8:32 AM (GMT -8) on 11 Jan 2024]
