is there a way to verify a 2nd mailserver as trusted without getting header anomaly triggered?
We got an external mail service (Amazon SES) for sending mail batches for newsletter etc.
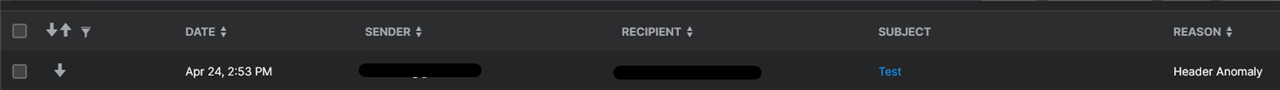
Some of those mails will be send towards internal which tiggers a header anomaly in sophos central caused by the same domain and two different mailservers.
Our goal is that we wanna harden our mail base policy and send these mails header anomaly into quarantine.
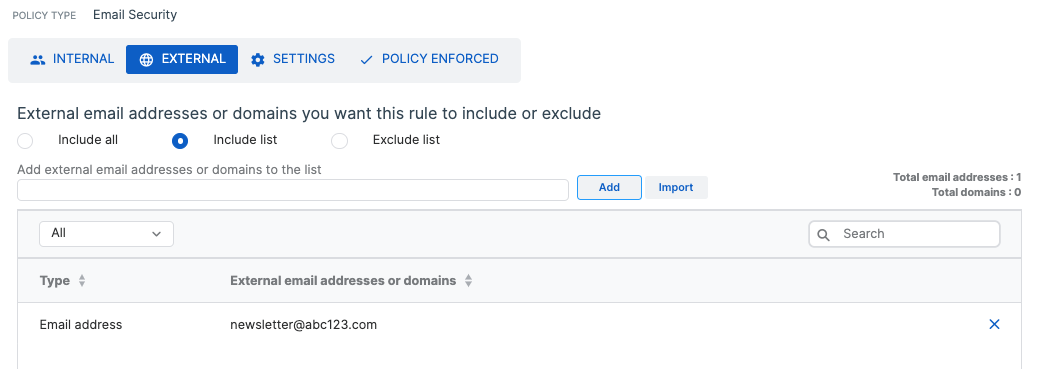
Internal Mailserver: @abc123.com
External Mailserver: newsletter@abc123.com
We configured DKIM aswell but it won't get rid of header anomaly internally.
Any ideas how to solve or improve our settings?
Thanks for your input
This thread was automatically locked due to age.