Hi
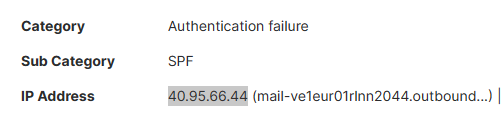
We have problem getting emails from o365 that comes from ip 40.95.0.0/16 range.
Microsoft calls it relay pool. Its not the in the SPF pool.
Does anyone know what to configure so the emails will not be with spf error?
Anyone?
Shay
This thread was automatically locked due to age.