Hello community,
we have migrated from Sophos UTM to Sophos Mail Advanced.
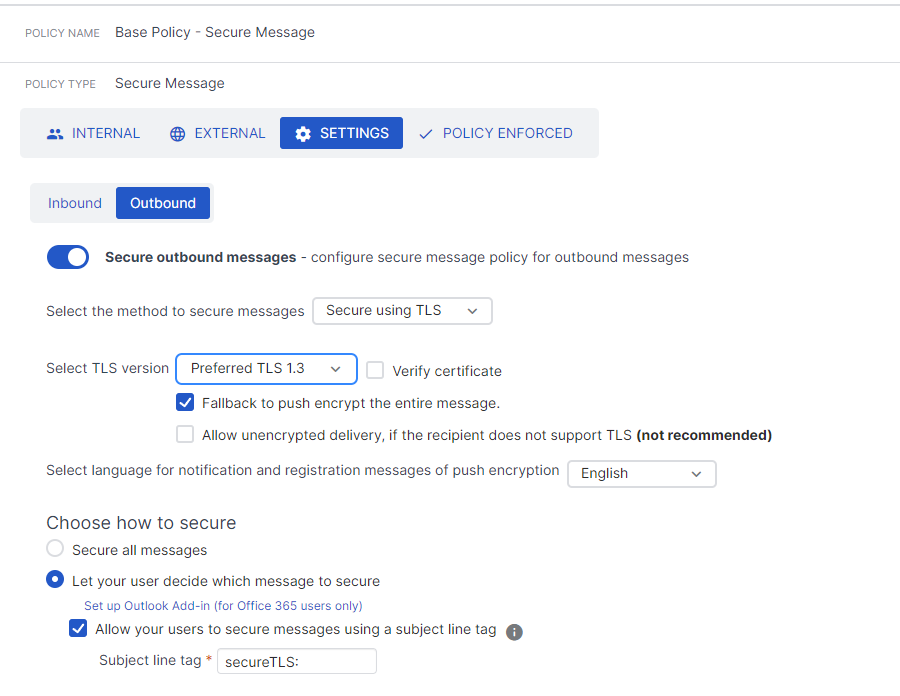
On our UTM, we could configure transport encryption to TLS 1.2. Additionally, each internal user could choose to send an email using Sophos SPX for end-to-end encryption.
While the rule set in Sophos Mail Advanced is straightforward, I am having difficulty understanding how to replicate our UTM configuration there. What I want to achieve:
- Sending with TLS 1.3/1.2
- Receiving with TLS 1.3/1.2
- Optional: Utilizing Push Encryption when a keyword is mentioned.
What is the best pracitise for doing this?
Thank you
This thread was automatically locked due to age.